Intrusion Detection ID - PowerPoint PPT Presentation
1 / 18
Title:
Intrusion Detection ID
Description:
Intrusion Detection (ID) Intrusion detection ... Who gained super user / administrator access. From whom mail was received/sent ... It is considered paranoid. ... – PowerPoint PPT presentation
Number of Views:29
Avg rating:3.0/5.0
Title: Intrusion Detection ID
1
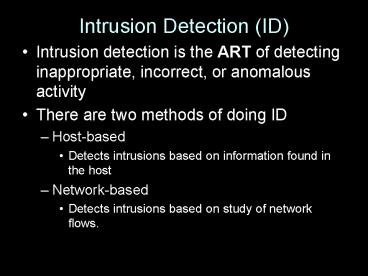
Intrusion Detection (ID)
- Intrusion detection is the ART of detecting
inappropriate, incorrect, or anomalous activity - There are two methods of doing ID
- Host-based
- Detects intrusions based on information found in
the host - Network-based
- Detects intrusions based on study of network
flows.
2
Intrusion Detection (ID)
- There are then two way to approach ID
- Knowledge-based
- The id has a signature pattern that is
unacceptable. - Behavior-based
- The id has a pattern of usage, and looks for
changes in that behavior.
3
Host-based ID
- Uses the systems own auditing tools to detect an
intrusion. - Log files
- Network traffic in and out of a single computer
(personal firewalls and host wrappers) - Process monitoring
- Disk usage
- File system changes
4
Host-based ID
- Log files can tell
- When a user login/out
- How they logged in (console/telnet/ftp/ssh)
- Login attempts and failures
- Who gained super user / administrator access
- From whom mail was received/sent
- When the machine was rebooted
- Any loggable anomalous behavior
5
Host-based ID
- Log files should be protected.
- They are one of the most likely files to be
modified if an intrusion takes place. - Make sure permissions of the logs keeps the
file(s) secureand even unreadable to a hacker. - Try mirroring the log file to another machine
that the hacker most likely wont be able to
access.
6
Personal Firewalls
- We all know about personal firewalls by now.
But - Make the firewall create logs. It can make you
aware of attempted access. - If you just block traffic you will never know
- what hackers are trying to get to (to protect
other systems) - Where the hackers are coming from
- If there are other related issues
7
Host Wrappers
- Used to allow access to certain server programs.
- Can limit based on time of day, repetition.
- Can limit based on ip address /domain
- Can limit based on ip address / domain and
service requested. - Popular host wrappers are
- Unix TCPWrapper
- Windows NukeNabber
8
Process Monitoring
- By monitoring running processes you can see if
applications are running that are not supposed to - Unix
- ps (list running processess)
- lsof (list of open files)
- process accounting (if kernel configured)
- Windows
- Task manager
9
Disk Usage
- Sudden increases / reductions in disk storage
could indicated an intrusion - Use quotas
- Unix tools
- df (disk usage of partitions)
- du (storage in a directory)
- Windows
- Properties under My Computer
10
File system changes
- Monitor your system for file changes
- Size
- Modification date
- File permissions
- Ownership
- Location on the hard drive (sector or inode
number) - Popular tools are
- Tripwire (www.tripwire.com)
- symantec (www.symantec.com)
- ISS by IBM, (www.iss.net)
11
Network-based ID
- Generally done by putting a network card in
promiscuous mode and monitoring all the traffic - With a knowledge-base approach, packets are
considered interesting if they match a
signature - There are 3 different type of signatures
- String
- Port
- Header condition
12
Network-based ID
- String signatures look for certain strings inside
of a packet. Like password, rhosts, su, etc - Port signatures watch for connections to well
know ports that have security problems (nfs) or
are frequently attacked (ftp, telnet, imap) - Header condition signatures look for malformed
headers. - SIN/FIN packet (not allowed)
- Extremely large window size
- Urgent flag for the NetBios packet (WinNuke)
13
Network-based ID
- Well-known, network-based intrusion detection
systems include - Symantec (www.symantec.com)
- Cisco (www.cisco.com)
- ISS by IBM(www.iss.net)
- SNORT (www.snort.org)
14
Knowledge Based ID
- Almost all ID systems are knowledge based
- The ID contains info about know attack methods
and detects or stop them - Only as good as the signatures in the IDS.
- Signatures must be updated constantly
- Very good at detecting an intrusion
- Very low false alarm rate
- Gives a good trace of how to harden your system
- Good analysis of the intrusion with evidence that
can be used to get the intruder.
15
Knowledge Based ID
- Draw backs include
- Only detects known intrusions
- Closely tied to the operating system and programs
running on it. - Very difficult to configure a new intrusion
without catching valid access.
16
Behavior Based ID
- Works by detecting a change in normal behavior.
- Normal behavior is gotten by monitoring the
system for a period of time. - Then this model of normal behavior is compared to
current activity. If there are a difference
between the model norm and current activity, an
alarm is sent.
17
Behavior Based ID
- Advantages
- Can see new and unforeseen attacks
- Less dependant on OS specific mechanisms
- Can even see abuse of privilege which is not
necessarily an attack just an abuse - It is considered paranoid. Any change from
normal is bad until incorporated into the
normal pattern. - Disadvantages
- Many false alarms
- Difficult to get normal behavior
- Behavior changes in time
- An attack can be learned as normal behavior if
it occurs during the learning phase
18
Intrusion Detection
- Both the host based and network based ID should
be used to protect your system. - http//www.sans.org/resources/idfaq/