Credit Card Hacking Software PowerPoint PPT Presentations
All Time
Recommended
http://bit.ly/12yaHZh FREE Credit Card Numbers That Work…. Enjoy Shopping…. Have Fun… Extra Tags (For Optimization Purpose Only): Credit Card Hacker, Free Credit Card Numbers With All Details, Free Working Credit Card Numbers 2013, Credit Card Hacking Software, Free Credit Card Numbers With CVV2, Free Credit Card Numbers, Credit Card Number Generator, How To Hack A Credit Card For Free, Hacking Credit Cards And Transferring Money To Your Bank, Passwords And Credit Card Numbers Hacked, Credit Card Hacking Tutorials, Free Credit Card Numbers With CVV, Credit Card Hacker 2013, Hacked Credit Card Numbers, Hacked Credit Card Information, Hacked Credit Cards 2013, Free Credit Card Details, Credit Card Numbers That Work 2013, Free Credit Card No, CREDIT CARD GENERATORS, CREDIT CARD HACK 2013, CREDIT CARDS GENERATOR 2013, CREDIT CARDS GENERATOR,
| PowerPoint PPT presentation | free to download
Client calls says they have an issue. They have been notified by the USSS they have had credit cards compromised ... Additonal Ports Open remote control programs ...
| PowerPoint PPT presentation | free to view
Clever Division (formerly called StagedPay) safeguards customers’ credit card numbers simply by not storing them and protect businesses from theft, fraud and data breaches.
| PowerPoint PPT presentation | free to download
Oversee administrative, management and marketing retail functions from a single centralized component. Empower your business today with Our POS Software.
| PowerPoint PPT presentation | free to download
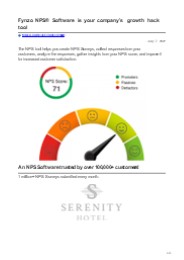
The NPS tool helps you create NPS Surveys, collect responses from your customers, analyze the responses, gather insights from your NPS score, and improve it for increased customer satisfaction.
| PowerPoint PPT presentation | free to download
Understanding Credit Card Security Requirements. Gregory Dove, Manager, ... No, or was complaint, but forensic team discovered compliance lapsed ...
| PowerPoint PPT presentation | free to view
With a nationwide shortage of microchips, we still have hundreds of MICROS POS-compatible EMV terminals in stock and ready for immediate deployment. For businesses, an Emv Solution For Micros Symphony can prove to be quite significant. We can provide you with solutions; with our help, your MICROS POS system will be able to support EMV chip readers, allowing you to transact more freely. We provide Emv Credit Card Reader For Micros 3700 and Micros Symphony.
| PowerPoint PPT presentation | free to download
They believe in assumption of High Risk! No Problem. gopaymentpros.com help high risk merchants find the best payment processing options for their retail and e-commerce businesses. Through a diverse network of domestic and offshore banking partners, they can help your business earn a fast approval and start accepting online credit card payments
| PowerPoint PPT presentation | free to download
Find out the top 10 credit card scams of all time, which created history in their time. Read the blog to learn more about credit card scams.
| PowerPoint PPT presentation | free to download
When Mobile Code and Smart Cards Meet: Java Card Security Gary McGraw, Ph.D. Vice President, Corporate Technology Cigital http://www.cigital.com This lecture made ...
| PowerPoint PPT presentation | free to download
New technology allows multiple applications on the same card ... one major vendor behind Java Card is Visa ... Cards often include secrets from owner ...
| PowerPoint PPT presentation | free to download
'Fix it, don't try to understand it.' Just-in-time program comprehension [Lethbridge] ... However, it's pioneering work on software evolution and software engineering. ...
| PowerPoint PPT presentation | free to download
It’s not uncommon for online retailers to face brute-force attacks often. Like physical stores are vulnerable to thieves and crooks, e-retailers too have their fair share of fraudsters and hackers stealing sensitive credit card details and other confidential information from their ecommerce sites. With advanced hacking and phishing tools and software galore on the web to fetch sensitive information like banking credentials and user passwords, swindlers and hackers, today, don’t necessarily require any additional skill or resources to perform fraudulent transactions.
| PowerPoint PPT presentation | free to download
It’s not uncommon for online retailers to face brute-force attacks often. Like physical stores are vulnerable to thieves and crooks, e-retailers too have their fair share of fraudsters and hackers stealing sensitive credit card details and other confidential information from their ecommerce sites. With advanced hacking and phishing tools and software galore on the web to fetch sensitive information like banking credentials and user passwords, swindlers and hackers, today, don’t necessarily require any additional skill or resources to perform fraudulent transactions.
| PowerPoint PPT presentation | free to download
Hordes sataware of apps byteahead are released web development company every app developers near me day hire flutter developer and ios app devs most a software developers of them software company near me carry software developers near me important good coders user top web designers information. sataware These software developers a applications app development phoenix are vulnerable app developers near me to idata scientists attacks top app development by hackers source bitz who software company near look app development company near me for Software developement near me weaknesses app developer new york
| PowerPoint PPT presentation | free to download
There are many accounting hacks you must consider. Make sure you connect credit cards and bank accounts, you must automate invoicing requirement, etc. Visit: https://jarrarcpa.com/small-business-accounting/
| PowerPoint PPT presentation | free to download
Nowadays there is software in market which helps individuals or businesses to pay or receive payments at half the price of payment done through credit/debit cards. It’s also known as Check by Phone Software. With the help of this software, check payments can be transacted over phone, web, email and fax.
| PowerPoint PPT presentation | free to download
Technology Hacks. Design deficiencies and other vulnerabilite ... Software hacks. Second channel attacks. RFID issues. Cell phone vulnerabilities. Grocery cards? ...
| PowerPoint PPT presentation | free to view
Just in the last few years, hundreds of millions of credit card details have been leaked. This is achieved by exploiting weaknesses in hardware and software. Cybersecurity can be defined as technologies and methods to protect the confidentiality, integrity, and availability of computer systems and networks against unauthorized access. The purpose of cybersecurity is to protect all organizational infrastructure from both external and internal threats. Organizations are beginning to know that malware is publicly available, which makes it easy for anyone to become a cyber attacker, and companies provide security solutions to protect against attacks.
| PowerPoint PPT presentation | free to download
Stored program units. Built in. User created. Several types. Inject SQL, ... Oracle CPUs and hacking forums Roadmaps to your data. Protecting Your Database ...
| PowerPoint PPT presentation | free to view
Malicious code. Hacking and Cybervandelism. Credit card fraud. Spoofing. Denial of Service Attacks ... Examples of Malicious. Code. Page 241. Table 5.2. Tools ...
| PowerPoint PPT presentation | free to view
Objective of this software is to maintain software piracy protection and allow access to authenticate users only. Piracy has become so prevalent over the Internet that poses a major threat to software product companies. To avoid hacking and stealing software need arises to protect the information and products from being plagiarized. This achieves the same purpose successfully
| PowerPoint PPT presentation | free to download
We already have driving licences that are credit card size with our photos on them. ... Reducing car pollution. Ethical, moral and social issues. Software theft ...
| PowerPoint PPT presentation | free to view
Third edition Sara Baase Chapter 5: Crime What We Will Cover Hacking Identity Theft and Credit Card Fraud Scams and Forgery Crime Fighting Versus Privacy and Civil ...
| PowerPoint PPT presentation | free to view
Emulation requires emulation software, a PC to run the emulation software on, ... DirecTV fries access cards they suspect as unauthorized. ...
| PowerPoint PPT presentation | free to view
n : the co-option of another person's personal information (e.g., name, social ... Camera phones. Software tools. Credit card 'skimming' ATM spy cameras ' ...
| PowerPoint PPT presentation | free to view
In recent years, the retail and hospitality industries have been rocked with data breaches with point of sale malware becoming increasingly common. Among several POS hardware available in-store, digital cash registers are often the most common target of malware designed by hackers to steal important data like credit card information.
| PowerPoint PPT presentation | free to download
... a criminal act perpetuated through computers resulting in violence, death and/or ... social security numbers, credit card numbers, business secretes, and the hack ...
| PowerPoint PPT presentation | free to view
Hacking - showing computer expertise. Cracking - breaching security on software or systems ... Hacking through the ages. 1969 - Unix hacked' together ...
| PowerPoint PPT presentation | free to download
Smart Cards By Sravanthi Karumanchi Introduction The semiconductor revolution has advanced to the point where the computing power that once took up an entire room can ...
| PowerPoint PPT presentation | free to download
Software Security Testing Vinay Srinivasan srinivasan_vinay@yahoo.com vinay.srinivasan@techmahindra.com cell: +91 9823104620 By Vinay Srinivasan (Tech Lead) Working ...
| PowerPoint PPT presentation | free to download
A study covering 30 countries and nearly 5,000 ... NNTP. Usenet. IRC. Posts. Downloads. Notifies. Queries. Hacker. Post trojan. Victim downloads/runs ...
| PowerPoint PPT presentation | free to view
Not uncommon for hackers to quit a job rather than conform to a dress code. ... Convertible (steal cell phone to use phone services; steal credit card to purchase ...
| PowerPoint PPT presentation | free to view
Certified Ethical Hackers can now be found working with some of the greatest and wealthiest industries such as healthcare, education, government, manufacturing, and many others. Due to the sheer demand, CEH certified Ethical Hacker is a lucrative and rewarding career choice currently and this potential is only going to increase in the future.
| PowerPoint PPT presentation | free to download
1. Web Hacking. Case Studies. 2. Web Site Hacking ... People hacking web sites are usually, though not always, using old and well ...
| PowerPoint PPT presentation | free to download
... the more substantial can be the risks and losses caused by a corporate site hack. ... Filter is the most effective way to protect sites against possible security ...
| PowerPoint PPT presentation | free to download
... Credit Card Programs (American Express, JCB, Discover) ... Discover Financial Services. MasterCard Worldwide. Visa International. JCB (Japan Credit Bureau) ...
| PowerPoint PPT presentation | free to view
Draper builds a 'blue box' used with whistle allows phreaks to make free calls. ... Software, KPMG, Fleet International, Cingular Wireless, Columbia Daily Tribune, ...
| PowerPoint PPT presentation | free to view
There are six important things that should be kept in mind in order to reduce the risk of security breach and stay away from being blacklisted. Especially, if you own an e-commerce site, information like personal details, credit card details can be stolen and can be misused or website can be hacked and can go down for quite a long time, which in turn will have bad impact on your business. Due to such reasons you should pay special attention to WordPress standard ssl security.
| PowerPoint PPT presentation | free to download
Rue de Bitbourg 11 L1273 Luxembourg HAMM. cdelbrassine@itworks.lu. DELBRASSINE Charles ... PCI Qualified Payment Application Security Assessor. IT Works S.A. ...
| PowerPoint PPT presentation | free to view
Explore our comprehensive guide to building custom financial management software. Discover key ideas, development stages, and features to create a solution.
| PowerPoint PPT presentation | free to download
It provides best training for an ethical hacking and, certified ethical hacking, EC-council certified security analyst .certified ethical hacking is a process. The users to modify any computer software and hardware. The EC-Council Certified Security Analyst V9 (ECSA) penetration testing course is a testing-based capability of a penetration tester. The EC-Council Certified Security Analyst V9 (ECSA) penetration testing course is a testing-based capability of a penetration tester. If you join this you can contact us www.certstore.in
| PowerPoint PPT presentation | free to download
It provides best training for an ethical hacking and, certified ethical hacking, EC-council certified security analyst .certified ethical hacking is a process. The users to modify any computer software and hardware. The EC-Council Certified Security Analyst V9 (ECSA) penetration testing course is a testing-based capability of a penetration tester. The EC-Council Certified Security Analyst V9 (ECSA) penetration testing course is a testing-based capability of a penetration tester. If you join this you can contact us www.certstore.in
| PowerPoint PPT presentation | free to download
Software engineers need to learn how to build systems that are on time and within budget ... Why build in prototyping & user testing? What's different during ...
| PowerPoint PPT presentation | free to download
Explore our widespread network of reliable money transfer hack locations throughout the United States. Trust us for a swift and reliable financial experience!
| PowerPoint PPT presentation | free to download
Selecting the best accounting software is a crucial decision. Here's a comprehensive guide to select an ideal accounting software for small businesses.
| PowerPoint PPT presentation | free to download
The act of hacking or breaking into a computer system, for a politically or ... http://www.crime-research.org/news/ . Works Cited. Samavati, Shaheen. ...
| PowerPoint PPT presentation | free to view
Mike McConnell. Former DNI, NSA. Head of Booz Allen Hamilton. National Security Business If we were in a cyberwar today, the United States would lose.
| PowerPoint PPT presentation | free to view
Building your own cryptocurrency exchange can be a challenging and expensive endeavor. However, using Binance clone software can make the process easier, faster, and more cost-effective.
| PowerPoint PPT presentation | free to download
To get free stuff. Impress their peers. Not get caught. Underemployed Adult Hackers ... that we download and install from the net (remember nothing is free) ...
| PowerPoint PPT presentation | free to download
Verify e-cards. Emailpi.Com installs spy ware through the opening of ... Never accept an offer for free credit reports or monitoring. Protection Can Be Cheap ...
| PowerPoint PPT presentation | free to view
A politically motivated defacement of PAC station desktop wallpaper. The regular wallpaper was used to provide instructions for use of the PAC and was 'locked down' ...
| PowerPoint PPT presentation | free to view
Networks are composed of two or more computers that share resources (such as printers and CDs), exchange files, and allow electronic communications. A network of computers may be connected by cables, telephone lines, radio waves, satellites, or infrared beams.
| PowerPoint PPT presentation | free to download
Hire a hacker for resolve technical issues with your computer system. The words "hire a hacker for resolve technical issues with your computer system" is a very common statement.
| PowerPoint PPT presentation | free to download
Know the What, Why and How about Ethical Hacking. It is sometimes also known as penetration testing or pen-testing.
| PowerPoint PPT presentation | free to download
A Smart card based e-driving licence & ID card By Mr Muhammad Wasim Raad Computer Eng. Dept, KFUPM What is a Smart card? A smart card is the size of a conventional ...
| PowerPoint PPT presentation | free to view