Prerequisite Knowledge Survey - PowerPoint PPT Presentation
1 / 30
Title:
Prerequisite Knowledge Survey
Description:
Bus, star, ring, point-to-point, and mesh are some of the common physical topologies. ... reduces the interference to and from the other wire pairs in the cable. ... – PowerPoint PPT presentation
Number of Views:44
Avg rating:3.0/5.0
Title: Prerequisite Knowledge Survey
1
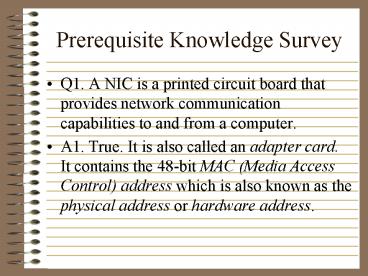
Prerequisite Knowledge Survey
- Q1. A NIC is a printed circuit board that
provides network communication capabilities to
and from a computer. - A1. True. It is also called an adapter card. It
contains the 48-bit MAC (Media Access Control)
address which is also known as the physical
address or hardware address.
2
Prerequisite Knowledge Survey
- Q2. The binary number 10110 is 23 in decimal.
- A2. False. It is 22 (16 4 2).
3
Prerequisite Knowledge Survey
- Q3. Digital bandwidth is measured in bits per
second (bps). - A3. True. It is the rated throughput capacity of
a given network medium or a protocol. It can also
be expressed as kilobits per second (kbps),
megabits per second (Mbps), or gigabits per
second (Gbps).
4
Prerequisite Knowledge Survey
- Q4. A protocol is a set of rules.
- A4. True. These rules detail how devices on a
network must exchange information. This includes
the format of messages that will be exchanged and
the details of error manage-ment.
5
Prerequisite Knowledge Survey
- Q5. Data encapsulation occurs at a single OSI
model layer only. - A5. False. When data move from the upper layers
down through the lower layers, headers, trailers,
and other pertinent information are added by each
of these layers.
6
Prerequisite Knowledge Survey
- Q6. A network layer packet is called a datagram.
- A6. True. When data go down through the different
layers, they become known as segments(upper
layers), packets (layer 3), frames (layer 2), and
bits (layer 1).
7
Prerequisite Knowledge Survey
- Q7. Topology is the physical arrangement of
network nodes and media. - A7. True. See it as the general shape of the
network. Bus, star, ring, point-to-point, and
mesh are some of the common physical topologies.
8
Prerequisite Knowledge Survey
- Q8. A LAN switch, or just a switch, is an OSI
layer 3 (network layer) device. - A8. False. It is an OSI layer 2 device. A router
is a layer 3 device.However, switches can, in
addition, have layer 3 functionality, and,
conversely, routers can have layer 2
functionality built in.
9
Prerequisite Knowledge Survey
- Q9. Routers connect bridges and repeaters.
- A9. False. Routers connect multiple networks
together. They can interconnect different LAN
media and topologies, and also different media
access methods such as Ethernet and Token Ring.
10
Prerequisite Knowledge Survey
- Q10. You need 5 IP addresses to connect 4 hosts
through a hub to the Internet. - A10. False. A host is an addressable device, a
hub is not. Because there are 4 hosts, only 4 IP
addresses are needed, none for the hub.
11
Prerequisite Knowledge Survey
- Q11. The reason that the wires in a UTP cable are
twisted is to make it less expensive. - A11. False. The purpose of twisting is to reduce
interference to and from outside electrical
sources. It also reduces the interference to and
from the other wire pairs in the cable.
12
Prerequisite Knowledge Survey
- Q12. Using repeaters reduces the number of
collision domains. - A12. False. A repeater regenerates and retimes
signaling pulses received at its input before
retransmitting them. It contains no intelligence
to filter traffic and consequently does not
influence the number of collision domains.
13
Prerequisite Knowledge Survey
- Q13. Routers separate collision domains and
broadcast domains. - A13. True. A router separates network segments
and will only process traffic specifically
addressed to it in accordance with the content of
routing tables, thereby separating these domains.
14
Prerequisite Knowledge Survey
- Q14. In a full-mesh topology every node is
connected to the central node. - A14. False. There is no central node, every node
is connected to every other node. A total of (n/2
(n - 1)) connections are required for
this.Example With 20 nodes, a total of (20/2)
(20 - 1) 10 19 190 connections are needed
to establish a full-mesh topology.
15
Prerequisite Knowledge Survey
- Q15. Recognized IEEE sublayers are concerned with
OSI layers 1 and 2. - A15. True. IEEE 802.2 and IEEE 802.3 map to OSI
layers 2 and 1 respectively.
16
Prerequisite Knowledge Survey
- Q16. The first six hexadecimal numbers in a MAC
address are the OUI. - A16. True. The MAC address has 48 bits and is
usually written as 12 hexadecimal characters. The
first 6 are known as the OUI or Organizationally
Unique Identifier and the remaining 6 are
never-used-before numbers, assigned by the
manufacturer of the device.
17
Prerequisite Knowledge Survey
- Q17. The number 2989 in decimal notation is BAD
in hexadecimal notation. - A17. True. It is derived as follows2989 16
186, remainder 13 D186 16 11 B,
remainder 10 ACheckB 11 16 16
2816A 10 16 160D 13, thus 2816 160
13 2989.
18
Prerequisite Knowledge Survey
- Q18. Errors can be detected with the use of CRCs.
- A18. True. CRCs (Cyclic Redundancy Checks)
consist of the result of a mathema-tical
algorithm that is applied by both the sender and
the receiver of the data. If they agree, the data
are considered to be received without error.
19
Prerequisite Knowledge Survey
- Q19. Broadcasting is sending a single frame to
many nodes at the same time. - A19. True. The broadcast MAC address contains all
hex Fs, and the IP broadcast address has all hex
Fs in the HostID. All nodes with these addresses
receive the same copy of the frame.
20
Prerequisite Knowledge Survey
- Q20. CSMA/CD is a non-deterministic protocol.
- A20. True. CSMA/CD which stands for Carrier Sense
Multiple Access/Collision Detection, is a
probabilistic protocol, also called a
non-deterministic protocol, and is used by
Ethernet.Token ring uses a deterministic
protocol.
21
Prerequisite Knowledge Survey
- Q21. FDDI is characterized by a logical ring and
a physical dual-ring topology. - A21. True. With FDDI (Fiber Distributed Data
Interface), data, driven logically (meaning by
software), are travelling sequentially from node
to node as in a ring. However, the actual
designed, physical layout consists of a double
ring.
22
Prerequisite Knowledge Survey
- Q22. Token passing attaches token frames to data
frames to access the network. - A22. False. What happens is, that a node has to
capture a free token first. This allows it to
start transmitting data after changing the state
of the token from free to busy. This ensures that
no other node also can start to transmit, because
every node needs a free token to do that.
23
Prerequisite Knowledge Survey
- Q23. NICs interface with networks and with hosts
through serial connections. - A23. False. Although the interface with the
network is a serial connection (bit-by-bit), the
interface with the host uses a parallel interface
(byte-by-byte).
24
Prerequisite Knowledge Survey
- Q24. Transparent bridges filter traffic based on
IP addresses. - A24. False. Routers do that. Regular trans-parent
bridges perform filtering based on MAC addresses,
unless they also have layer 3 capabilities.
25
Prerequisite Knowledge Survey
- Q25. Routers are less complicated devices than
transparent bridges. - A25. False. Because routers make routing
decisions based on many more parameters than
bridges do, they are also more versati-le, and
consequently more complicated, (and expensive)
than bridges.
26
Prerequisite Knowledge Survey
- Q26. The maximum value of an octet is decimal
256. - A26. False. It is 255. An octet has 8 bits, with
values from 00000000 to 11111111 or, in decimal
notation, 0 to 255. The highest value is
therefore 255. But, because the value of 0 is
included, there are a total of 256 unique bit
combinations
27
Prerequisite Knowledge Survey
- Q27. The network portion of the IP address
129.219.34.9 is 129.219. - A27. True. It is a Class B address. Thus the
first 2 octets form the NetID or prefix
(129.219). The remaining 2 octets are the HostID
or suffix (34.9).
28
Prerequisite Knowledge Survey
- Q28. The maximum number of hosts in a Class C
network is 256. - A28. False. It is 254, because all 0s and all 1s
are not allowed to be used in the NetID.This
leaves 256 - 2 254 hosts that can be
accommodated in a Class C network.All 0s are
reserved for the network address (also called the
wire address), and all 1s are reserved for the
broadcast address.
29
Prerequisite Knowledge Survey
- Q29. The minimum number of bits that can be
borrowed to form a subset is 4. - A29. False. The minimum number is 2. This allows
for addresses 01 and 10.With two bits, 22 4
combinations are possible, but dont forget, we
just discussed that 00 and 11 are reserved for
wire and broadcast address respectively.
30
Prerequisite Knowledge Survey
- Q30. 131.82.21.35 AND 255.255.0.0 131.82.0.0.
- A30. True. In binary10000011.01010010.00010101.0
010001111111111.11111111.00000000.00000000------
--------------------------------------------
AND10000011.01010010.00000000.00000000or in
decimal 131 . 82 . 0
. 0