Layer 4 Transport Layer PowerPoint PPT Presentation
1 / 56
Title: Layer 4 Transport Layer
1
Layer 4 - Transport Layer
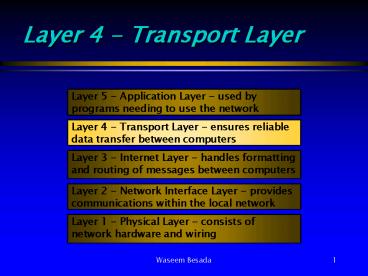
Layer 5 - Application Layer - used by programs
needing to use the network
Layer 4 - Transport Layer - ensures reliable data
transfer between computers
Layer 3 - Internet Layer - handles formatting and
routing of messages between computers
Layer 2 - Network Interface Layer - provides
communications within the local network
Layer 1 - Physical Layer - consists of network
hardware and wiring
2
Networking Protocols
- Networking Protocols
- Specify networking details
- How to pass messages
- What information messages should contain
- How to handle errors
- Provide a common ground
- Hardware from different vendors can communicate
due to common protocol usage
3
Layered Protocol Suites
- Arranged in layers so that each layer only
communicates with the layers directly above and
below - Each layer performs a well defined function
- Conceptually, each layer performs one of two
generic tasks - Network-dependent tasks
- Application-oriented tasks
- OSI Model has seven layers
- TCP/IP Model has five layers
4
Protocol Suites OSI Model
Layer 7 - Application Layer
Application-Oriented Layers
Layer 6 - Presentation Layer
Layer 5 - Session Layer
Layer 4 - Transport Layer
Layer 3 - Network Layer
Network-Dependent Layers
Layer 2 - Link Layer
Layer 1 - Physical Layer
5
Protocol Suites TCP/IP Model
6
Layered Communication
- Communication Between Stacks
- Ultimately between corresponding layers
- Layer 6 talks to layer 6, layer 5 to layer 5,
etc. - In practice
- Each layer uses the services of the layer below
- Each layer provides services to the layer above
- No direct communication between stacks
- Communication between corresponding layers works
its way down the layers of one stack and back up
the layers of the other stack
7
Layered Communication OSI
Computer One
Computer Two
Layer 7 - Application Layer
Layer 7 - Application Layer
Layer 6 - Presentation Layer
Layer 6 - Presentation Layer
Layer 5 - Session Layer
Layer 5 - Session Layer
Layer 4 - Transport Layer
Layer 4 - Transport Layer
Layer 3 - Network Layer
Layer 3 - Network Layer
Layer 2 - Link Layer
Layer 2 - Link Layer
Layer 1 - Physical Layer
8
Encapsulation
- Method by which information passes through the
layers - Mechanism used by each layer
- Current layer wraps higher-layers packet into
the current data section for this layer - Current layer adds its own header
- Current layer may add other information
- Current layer passes its packet to next layer
9
Layered Communication
- Encapsulation (Continued)
- Example
Layer 7 - Application Layer
L7H
Data
Layer 6 - Presentation Layer
L7H
L6H
Data
Layer 5 - Session Layer
L5H
L7H
L6H
Data
Layer 4 - Transport Layer
L4H
L5H
L7H
L6H
Data
Layer 3 - Network Layer
L3H
L4H
L5H
L7H
L6H
Data
Layer 2 - Link Layer
L2H
L3H
L4H
L5H
L7H
Data
L6H
Layer 1 - Physical Layer
10
Protocol Techniques Packet Sequence Numbers
- Packet Sequence Numbers
- Out of order delivery
- Can happen in a connectionless communication
- Different packets take different routes
- Packets do not always arrive in order
- Packet sequencing
- Each packet contains a number which refers to its
sequence in the message - Receiver tracks last in-order sequence number
- Receiver tracks all out-of-order sequence numbers
11
Protocol Techniques Error Control
- Error control
- Echo checking
- Simplest form, also known as manual checking
- When typing characters at a terminal or console,
the character is shown on the screen - You see if theres an error and use the backspace
key to correct the error
12
Error Control ARQ Protocol
- Automatic Repeat Request (ARQ) Protocol
- Automated by the computer systems
- Basic functionality
- Sending machine (Primary) sends a frame
- Receiving machine (Secondary) receives the frame
- Secondary sends a short control frame - ACK or
NACK - to Primary indicating whether the frame
was correctly received - Primary resends the frame on error
- Two types - Idle RQ and Continuous RQ
13
Protocol Techniques Flow Control
- Flow control
- Used to control transmissions between systems of
different speeds - Slower system indicates when faster system must
stop sending frames - If faster system sends too much information,
overrun occurs and frames are lost - Idle RQ and Continuous RQ address flow control as
well as error control
14
Idle RQ Protocol
- Goals
- Provide a simple protocol which allows sending
and receiving of information frames (IFrames) in
the correct sequence and with few (if any) errors - Provide flow and error control
15
Idle RQ Implementation
- Basic implementation
- Primary sends an IFrame and waits
- Secondary receives IFrame and sends an
acknowledgement (ACK) frame when correct - Primary receives ACK frame and sends a new frame
- Protocol known as send-and-wait or stop-and-go
16
Idle RQ Implicit Retransmission
- Two ACK implementations possible
- Implicit retransmission
- Secondary acknowledges only correct frames
- Primary interprets absence of ACK as an
indication of problem - Secondary did not receive frame
- Secondary received a bad frame
- Without ACK, primary retransmits frame
17
Idle RQ Implicit Retransmission Example
- Note that
- Primary can only be waiting for one ACK frame at
a time - Primary can only transmit a new IFrame after
receiving an ACK on the previously sent frame - Primary starts a timer when IFrame is sent, and
retransmits if the timer runs out without an ACK
frame
18
Idle RQ Implicit Retransmission Example (contd)
- Also Note that
- Any corrupted frame received by secondary is
discarded - Timeout interval must be longer than the minimum
time required to transmit and receive ACK from
secondary
19
Continuous RQ Protocol
- Problems with Idle RQ
- Makes poor use of network bandwidth
- Must wait for ACK or NAK after every IFrame
- Continuous RQ Protocol
- Provides a simple protocol which allows sending
and receiving of information frames (IFrames) in
the correct sequence and with few (if any) errors
- flow and error control - Basic implementation
- Primary sends a continuous flow of IFrames
- Secondary receives IFrames and sends
acknowledgement (ACK) frames for correct frames - Primary receives ACK frames and continues
20
Continuous RQ Error Flow Control
- Error control
- Corrupted frames are discarded
- Two Retransmission methods possible
- Selective repeat
- Retransmission of corrupted frames only
- Go-back-N
- Retransmission of corrupted frame and all frames
that follow
21
Continuous RQ Flow Control
- Flow control
- Sliding window
- Primary and secondary agree on maximum number of
frames that can be sent without ACK - Primary sends up to max number of frames
- As secondary receives frames, it sends ACKs
- As primary receives ACKs, it sends more frames
22
Sliding Window Example
Still Unsent
Window
12
11
10
9
8
7
6
5
4
3
2
1
Already Acknowledged
Window
12
11
10
9
8
7
6
5
4
3
2
1
Window
12
11
10
9
8
7
6
5
4
3
2
1
23
Congestion and Collapse
- Network Congestion - occurs when packets arrive
at a router faster than they can be sent on - eventually the router runs out of memory and
begins to discard packets - this forces retransmissions which makes the
congestion even worse - Congestion collapse - occurs when congestion gets
bad enough to render the network effectively
useless
24
Responses to Congestion
- Two Approaches to Handling Congestion
- Arrange packet switches to inform senders when
congestion occurs - Use packet loss as an estimate of congestion
- Responding to Congestion
- Reduce the rate of packet transmission
- Rate control mechanisms as part of a protocol
- Reduce the size of window in sliding window
protocols
25
Transmission Control Protocol Reliable Transport
Service
Layer 5 - Application Layer - used by programs
needing to use the network
Layer 4 - Transport Layer - ensures reliable data
transfer between computers
Layer 3 - Internet Layer - handles formatting and
routing of messages between computers
Layer 2 - Network Interface Layer - provides
communications within the local network
Layer 1 - Physical Layer - consists of network
hardware and wiring
26
TCP Services
- Connection Orientation
- establishes a virtual connection between hosts
- connection is requested and then used to
communicate - Point-to-point Communication
- only two end points - service connects an
application on one host with an application on a
remote computer - Complete Reliability
- guarantees data sent across connection wil be
delivered as sent, error free with no losses or
duplicates and in the same order as transmitted - Full Duplex Communication
- data can flow in either direction and allows
either program to send data at any time
27
TCP Services (contd)
- Stream Interface
- allows sending a continuous stream of octets - no
notion of records - Reliable Connection Startup
- both applications must agree to a connection -
packets from previous connections will not
appear to be parts of the communication on this
connection - Graceful Connection Shutdown
- application program can open connection, send
data, request connection shutdown - all data
will be reliably delivered before shutdown
28
TCP Delivery
- TCP messages are sent using IP datagrams
- this means any routers the messages pass through
do not need to use the transport layer - they
work only with the IP datagram - this speeds delivery - only end points invoke TCP
Appl.
Appl.
router
Net.Iface.
Net.Iface.
Net 2
29
TCP Segments
- Segments
- all data is transmitted in units known as
segments - a segment is essentially a TCP
message - TCP decides when a new segment is to be
transmitted - when a new segment is started depends on nature
of information to be sent - if interactive, may
be a single keystroke per segment - if not
interactive, may be a portion of a file to be
sent - at the receiving host data received in a segment
is placed into a memory buffer and when the
buffer is full, the data is sent to the
application
30
Protocol Port Numbers
- Multiple higher level applications can be served
by TCP (and UDP) at the same time - Protocol Port Numbers (a.k.a. Port addresses) -
specify the sending and receiving applications - Assignment of port addresses
- 1) Central Authority (universal assignment or
well-known port assignments) - each particular application (telnet, ftp, etc) is
given a particular port number and all hosts know
and use that port address for that application - in UNIX these assignments are stored in the file
/etc/services
31
Example well-known services
- /etc/services
- echo 7/tcp
- echo 7/udp
- netstat 15/tcp
- ftp-data 20/tcp
- ftp 21/tcp
- telnet 23/tcp
- smtp 25/tcp mail
- time 37/tcp timserver
- time 37/udp timserver
32
TCP Segment Format
- Acknowledgement Number and Window
- refer to data already received and current window
size - Source Port and Destination Port
- indicate which application the segment is from/to
- Sequence Number
- number used for Continuous RQ protocol
33
User Datagram Protocol Connectionless Service
Layer 5 - Application Layer - used by programs
needing to use the network
Layer 4 - Transport Layer - ensures reliable data
transfer between computers
Layer 3 - Internet Layer - handles formatting and
routing of messages between computers
Layer 2 - Network Interface Layer - provides
communications within the local network
Layer 1 - Physical Layer - consists of network
hardware and wiring
34
UDP Service
- UDP offers connectionless service at the
transport layer - essentially a higher level extension of the IP
datagram - Appropriate uses of UDP datagrams
- use for any message where reliability is not
important and/or is very short - use when no error detection is needed
- example a single short request/response message
exchange is needed between application protocols
35
IPv6 (IPNG)
36
Why Do We Need a New IP-Protocol?
- The address space crisis.
- Poor utilization of numbers.
- Run out by 2008-2018.
- The routing crisis.
- Routing table overflows.
- New functionality.
- Mobile computing.
- Automatic configuration.
- Real time video and audio.
37
Header format
0 4 8
16 24
31
Version
Flow control
priority
Payload Length
Next header
Hop limit
Source address 128 bits
10 X 32 bits 40 octets
Destination address 128 bits
38
IPv6 (IPNG)
- Expanded Addressing Capabilities
- 128 bit address length
- improved multicast routing
- new cluster addresses to identify topological
regions - Header Format Simplification compared with IPv4
- some IPv4 fields have been dropped, some made
optional - header is easier to compute
- Improved Support for Extensions and Options
- more efficient for forwarding of packets
- less stringent limits to length of options
- greater flexibility for introduction of future
options - Flow Labeling Capability
- labeling of packets belonging to a particular
"flow" - allows special handling of, e.g., real-time,
packets - Authentication and Privacy Capabilities
- extensions to support authentication and
(optional) data confidentiality
39
IPv6 packet with all extensions
Application data
Hop-by-hop optionsheader
Routing header
Authentication header
Encapsulation securitypayload header
Destination optionsheader
IPv6 header
Fragment header
TCP header
40 V V 8 V
V V 20 V
Next header field variable
V
40
Writing an IPv6 address
- The 128 bit IPv6 address is written as eight
16bit integers using hexadecimal digits. The
integers are separated by colons. - for example FEDCBA9876543210FEDCBA987654
3210 - A number of abbreviations are allowed
- leading zeros in integers can be suppressed
- - a single set of consecutive 16 bit
integers with the value null, can be replaced by
double colon, i.e., 10800008800200C
417A becomes 10808800200C417A - 1 is loopback address as 127.0.0.1 in IPv4
41
Priority Fields
- Congestion-controlled traffic0
uncharacterized traffic1 Filler traffic
(e.g., netnews)2 Unattended data transfer
(e.g., mail)3 (Reserved)4 Attended bulk
transfer (e.g., FTP, HTTP)5 (Reserved)6
Interactive traffic(e.g., TELNET, X)7
Internet control traffic (e.g., routing
protocols, SNMP)
- Congestion-controlled traffic8 Most willing
to discard (e.g., high-fidelity video) - 15 Least willing to discard (e.g.,
low-fidelity audio)
increasing priority
42
Simplifications
- IPv6 builds on 20 years of internetworking
experience - which lead to the following
simplifications and benefits - Use fixed format headers
- Use extension headers instead, thus no need for a
header length field, simpler to process - Eliminate header checksum
- Eliminate need for re-computation of checksum at
each hop (relies on link layer or higher layers
to check the integrity of what is delivered) - Avoid hop-by-hop segmentation No
segmentation, thus you must do Path MTU discovery
or only send small packets (1996 536 octets,
1997 proposed 1500 octets) - - This is because we should have units of
control based on the units of transmitted data. - Eliminate Type of Service (ToS) field
- Instead use (labeled) flows
43
Quality-of-Service Capabilities(flow label)
- Flow characterized by flow id source address
- Unique random flow id for each source
- Routers identify each flow by the source address
and its label (Streams with non-zero flow
label should take the same route) - Flow labeled streams are treaded differently at
routers for source allocation, discard
requirements, accounting, etc. - Routers must maintain information about the
characteristics of each active flow that may
pass through it. - Sources generates a unique flow label for each
application and should not be used during the
the application lifetime.
44
IPv6 addresses
Allocation space Prefix(binary)
Fraction of address space Reserved 0000
0000 1/256 Unassigned 0000
0001 1/256Reserved for NSAP Allocation
0000 001 1/128 Reserved for IPX Allocation
0000 010 1/128 Unassigned
0000 011 1/128 Unassigned 0000
1 1/32 Unassigned 0001 1/16 Unassigned 001
1/8 Provider-Based Unicast Address 010 1/8 Unassi
gned 011 1/8 Reserved for Geographic-Based
Unicast Addresses 100 1/8 Unassigned 101 1/
8 Unassigned 110 1/8 Unassigned 1110 1/16 U
nassigned 1111 10 1/32Unassigned 1111
110 1/128 Unassigned 1111 1110 0 1/512 Link
Local Use Addresses 1111 1110 10 1/1024 Site
Local Use Addresses 1111 1110 11 1/1024 Multicas
t Addresses 1111 1111 1/256
- Unicast addresses
- Anycast addresses
- Multicast addresses
Anycast address is an address that has a single
sender, multiple listeners, and only one
responder (normally the "nearest" one, according
to the routing protocols' measure of distance).
An example may be several web servers listening
on an anycast address. When a request is sent to
the anycast address, only one responds.
45
Routing Header
- The routing header enables a host to prescribe
which path through a network a particular
datagram should take. This can be used in a
security-sensitive scenario and other
scenarios. - Analysis So that the routing header can be
used, knowledge of addresses and locations of
required routers is necessary. To collect this
information is most probably not an obvious
task. Additionally, if things change in the
network (e.g., a router is added or removed),
things can become very complicated when using
routing headers, since the system must be aware
of such changes. The Routing Header can give
better control to a company when routing packets
through its network, however, an effective use of
this type of packet will require equally an
effective IP address management system within
the company's network.
46
Example Routing Configuration
- Assume Host H1 sends packets to Host H2 The
routing header 1- no routing decision,
(H1,H2) 2- through P1,(H1, P1, H2) 3- if H1
becomes mobile, (H1, PW, P1, H2)
47
IPng - Negative Aspects
- Basic problem IPng is more than an upgrade to
a new IP it's a new protocol, not
backward-compatible with IPv4. - Migration problems The migration to IPng
could create the potential for TCP/IP
interoperability problems. The big problem
is that IPng is incompatible with the current
version of IP. To use the new protocol, net
managers will have to change the protocol stack
software in every networked device. - Changes at the Operating SystemSince the
protocol stack is part of the operating system in
many machines including PCs running UNIX and
the latest versions of Windows NT and OS/2
upgrading the IP stack means replacing the
Operating System.
48
IPng - Negative Aspects (contd)
- Changes at several levels routers, hosts, DNS
A domain name servers (DNS) is the device that
sit at the edge of an Internet connection and
that translate IP's numerical addresses into
Internet format.
49
How to move to IPv6?
50
Solution 1 Dual stack strategy
- The new protocol could be installed on routers
first, then moved to DNSs and finally to
hosts.Such an approach would ensure that as each
component is upgraded, it can still
communicate with all others components in the
network using the old protocol.BUT - This can work only if all vendors agree to
implement both the current version of IP and
IPng stacks on their products! - Even if vendors commit to IPng, a number of
older devices, such as low-end PCs or printers,
won't be part of the migration.
51
Solution 2 a few different coexistent schemes
- An encapsulation protocol that would enable IP
traffic to "tunnel" through an IPng network.
Another scheme to provide gateways that would
enable addresses between IP and IPng
networks.BUT such solutions are either
cumbersome to implement or inefficient- or both.
52
WHATS WRONG WITH IPv6 ?
- No Vendor Push ! No Urgency! Just a few !
- Its engineering-driven Not Market-driven !
- No IPv6 Applications
53
Make the BIG BANG Happen!
- IETF Will Not Support IPv4 beyond 2002
IPv4
IPv6
54
IPv6 Compliance Certification Logo
Inside
55
2001
10
56
Summary
- IPv6 futures and criticism Recommended
reading 15.4