Pseudo Random Number PowerPoint PPT Presentation
1 / 9
Title: Pseudo Random Number
1
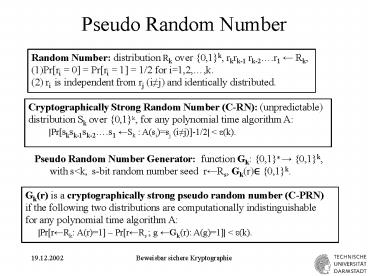
Pseudo Random Number
Random Number distribution Rk over 0,1k,
rkrk-1 rk-2.r1 ? Rk, (1)Prri 0 Prri 1
1/2 for i1,2,,k. (2) ri is independent
from rj (i?j) and identically distributed.
Cryptographically Strong Random Number (C-RN)
(unpredictable) distribution Sk over 0,1k, for
any polynomial time algorithm A
Prsksk-1sk-2.s1 ?Sk A(si)sj (i?j)-1/2 lt
e(k).
Pseudo Random Number Generator function Gk
0,1s ? 0,1k, with sltk, s-bit random
number seed r?Rs, Gk(r)? 0,1k.
Gk(r) is a cryptographically strong pseudo random
number (C-PRN) if the following two
distributions are computationally
indistinguishable for any polynomial time
algorithm A Prr?Rk A(r)1 Prr?Rs
g ?Gk(r) A(g)1 lt e(k).
2
C-PRN ? next bit C-RN
(next bit C-RN) distribution Sk over 0,1k, for
any polynomial time algorithm A
Prsksk-1sk-2.s1 ?Sk A(si)si1-1/2 lt
e(k).
sj
sksk-1 . sj1sjsj-1
. s2 s1
Theorem C-PRN ? next bit C-RN
Proof of C-PRN ? next bit C-RN (1)If Sk
is not next bit C-RN, then there exists
an integer i s.t. Prs ?Sk
A(si)si1-1/2 gt e(k). (2)We can
distinguish (i1)-th bit of the sequence
sm-i-1 A(si) si and sm-i-1
si1 si with probability gte(k).
3
Proof of next bit C-RN ? C-PRN
(1)If Sm is not C-PRN then there is an
algorithm A which distinguishes Sm from Rm.
(2)Let hj rsj, (s?Sj, r?Rm-j), and let pj
PrA(hj)1. If algorithm A can not
distinguish hj and hj1, then we have
relationship pm - po ? pm pm-1
pm-1 pm-2 pm-2 pm-3 . p1 - po
lte(m) Thus there exists an integer I s.t.
PrA(hI)1 - PrA(hI1)1 gte(m).
- Algorithm A next bit C-RN
- Input sI ?Sm
- Output sI1?Sm
- b?0,1 r?Rm-I-1
- wb rbsI
- z?A(wb)
- If z 1 then return b
- else return b
- (3) s sm-I-1 sI1 sI ? Sm
- Pr A(sI) sI1 - 1/2 gte(m).
- It contradicts that Sm is next bit C-RN.
4
One-way function and PRNG
Let f be a permutation function of f 0,1n ?
0,1n. Function f is called one-way if Pr
y?0,1n,f(x)y A(y)xlte(n) holds for any
polynomial time algorithm A.
v(x)?0,1 is called a hard core bit function of
f(x) if (1)v(x) can be computed from x in
polynomial time of n, (2)Pr A(f(x))v(x)-1/2lt
e(n) holds for any polynomial time algorithm A.
- Algorithm PRNG
- Input x?Rn, f, v
- Output rmr2r1
- x1 x
- For i 1 to m
- xi1 f(xi)
- ri v(xi)
- Return rmr2r1
one-way function f 0,1n ? 0,1n, hard core
bit function v of f x?0,1
Theorem (one-way hard core bit function ?
C-PRNG) If m is the polynomial order of n, then
rmr2r1 output by algorithm PRNG is C-PRN.
5
Proof of theorem
(1) Gn(x)v(x)f(x) can not be distinguished
from random distribution Rn1
If yes, there is algorithm A s.t.
PrA(v(x)f(x))1 PrA(Rn1)1gte(n). f is
permutation, PrA(v(x)f(x))1 -
PrA(bf(x))1gte(n) for b?0,1.
PrA(bf(x))1 PrA(bf(x))1 bv(x)
Prbv(x) PrA(bf(x))1 bv(x)
Prbv(x) (PrA(v(x)f(x))1PrA(v(x)f(x))
1)/2
- Algorithm B, hard-core
- Input f(x)
- Output v(x)
- b ?0,1
- a ? A(bf(x))
- If a 1 then return b
- else return b
? PrA(v(x)f(x))1 - PrA(v(x)f(x))1/2 gt
e(n)
PrB(f(x))v(x) PrA(bf(x))1?v(x)b
PrA(bf(x))0?v(x)b PrA(bf(x))1
bv(x) Prbv(x) PrA(bf(x))0
bv(x) Prbv(x) (PrA(v(x)f(x))1
PrA(v(x)f(x))0)/2 gt PrB(f(x))v(x)-1/2gte
(n). (Contradiction to v(x))
6
Proof of theorem (Cont.)
(2) Let r rmrm-1r1 be the output by
algorithm PRNG. We prove that r and Rm are
indistinguishable.
- Algorithm PRNG
- Input x?Rn, f, v
- Output rmr2r1
- x1 x
- For i 1 to m
- xi1 f(xi)
- ri v(xi)
- Return rmr2r1
If not, algorithm A for hj rm-j aj,
(r?Sm, a?Rm), an integer I s.t. PrA(hI)1 -
PrA(hI-1)1 gte(n), where Sm is the
distribution arisen from PRNG.
For (n1)-bit input y yn1 yn, we define
B(y) A(v(fm-I-1(yn))v(f2(yn))v(f(yn
))v(yn)yn1aI-1 )
If y?Rn1?B(y) has the same distribution with hI.
If y Gn(x) v(x)f(x) ?B(y)
A(v(fm-I(x))v(f2(x))v(f(x))v(x)aI-1
) has
the same distribution with hI-1.
PrB(Rn1)1 PrB(Gn(x))1 PrA(hI)1
PrA(hI-1)1 gt e(n)
7
C-PRN by RSA encryption
Let (n,e) be the public-key of the RSA (1) RSA
encryption M ? Me mod n is one-way under the RSA
assumption (2) To find the least significant bit
LSB(M) for C is a hard core bit function of
the RSA function under RSA assumption.
- Algorithm RSA-PRN
- Input n, e, r (r log n-bit seed)
- Out m-bit r
- x1 r
- For j1 to m
- xj1 xje mod n
- rj LSB(xj)
- Return r rmr2r1
seed
register
C-PRN
xe mod n
8
Other results on bit security
vi(x)?0,1, (i1,2,..,k) is called a
simultaneously hard core bit function of f(x) if
(1) vi(x), (i1,2,..,k) can be computed from x
in polynomial time of n, (2)Pr A(f(x),
v1(x),.., vj-1(x)) vj(x) - 1/2 lte(n),
(i1,2,,k) holds for any polynomial time
algorithm A.
Theorem (Alexi, Chor, Goldreich, Schnorr in
1988) The log2(log2 n) least significant bits
of the RSA encryption are simultaneously 1/2
1/(log n)c secure.
Theorem (Long, Wigderson in 1988) The log2(log2
p) most significant bits of the discrete
logarithm function over Fp are simultaneously 1/2
1/(log p)c secure.
Theorem (Hastad,Schrift,Shamir in 1993) The
(log2n)/2 bits of the discrete logarithm
function over Zn (n is a composite number) are
simultaneously 1/2 1/(log n)c secure.
9
References of Chapter 2
ACGS88 W. Alexi, B.Chor, O. Goldreich, and
C.Schnorr, RSA and Rabin functions Certain
parts are as hard as the whole, SIAM J.Comput.
1988. Knu81 D. Knuth, The art of computer
programming, Addison Wesley, 1981.
Advanced in Cryptolgoy Crypto Advanced in
Cryptolgoy Eurocrypt Advanced in Cryptolgoy
Asiacrypt http//www.iacr.org/
Oded Goldreich Modern Cryptography,
Probabilistic Proofs and Pseudo-randomness
(Algorithms and Combinatorics Vol. 17), 1998,
ISBN 354064766X, http//theory.lcs.mit.edu/oded/