Example One PowerPoint PPT Presentation
Title: Example One
1
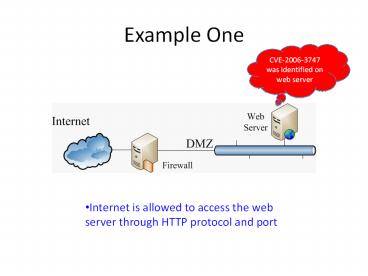
Example One
CVE-2006-3747 was identified on web server
- Internet is allowed to access the web server
through HTTP protocol and port
2
Exploit post-condition
Exploit pre-condition
Exploit post-condition
3
Pre- and Post-conditions can be used in
constructing an attack graph
The vulnerability exists
webServer is network-accessible to an attacker
The web service is running
This attack is possible
The consequence is that webServer is compromised
4
This process is completely automated
What are your threats?
attackerLocated(internet). hacl( internet,
webServer, httpProtocol, httpPort ). hacl( H, H,
_, _). networkServiceInfo( webServer, httpd,
httpProtocol, httpPort, apache ). vulExists(
webServer, cve_apache, httpd ). vulProperty(
cve_apache, remoteExploit, privEscalation ).
Firewall/network analyzer
Vulnerability scanner
NVD
5
But you do need a knowledge base
execCode(H, Perm) - vulExists(H, VulID,
Software, remoteExploit, privEscalation), network
ServiceInfo(H, Software, Protocol, Port,
Perm), netAccess(H, Protocol, Port)
The knowledge is completely independent of any
site-specific settings.
6
Combining attack graphs and CVSS
- Attack graph presents a qualitative view of
security problems - It shows what attacks are possible, but does not
tell you how bad the problem is. - It captures the interactions among all attack
possibilities in your system. - CVSS provides a quantitative property of
individual vulnerabilities - It tells you how bad an individual vulnerability
could be. - But it does not tell you how bad it may be in
your system.
7
Our Approach
- Use CVSS to produce a component metric --- a
numeric measure on the conditional probability of
success of an attack step. - Suppose an attacker needs c1 (network
access) to launch an attack on the vulnerability,
and c2 (host compromised) is the consequence of a
successful attack. the component metric means - Prc2 Tc1
T
This measure does not consider any attacker
behavior
8
High gt 0.2 Mediumgt 0.6 Low gt 0.9
9
Our Approach
- Aggregate the probabilities over the attack-graph
structure to provide a cumulative metric --- the
probability of attacker success in your system. - Suppose there is a dedicated attacker who
will try all possible ways to attack your system.
If one path fails, he will try another. The
cumulative metric is the probability that he can
succeed in at least one path.
10
Calculation of the cumulative metrics
c1
c2
Prc1?
Prc11
Prc2?
Prc20.2
Prc2c10.2
PrexecCode(webServer, apache)0.2
11
Example Two
CVE-2006-3747 was identified on web server
- Internet is allowed to access the web server
through HTTP protocol and port - Web server is allowed to access the MySQL
database service on the dbase server
CVE-2009-2446 was identified on db server
12
Exploit pre-condition
Exploit post-condition
Mediumgt 0.6
13
1execCode(dbServer,root) 2remote exploit of a
server program 3netAccess(dbServer,dbProtocol,dbP
ort) 4multi-hop access 5hacl(webServer,dbServer,
dbProtocol,dbPort) 6execCode(webServer,apache) 7
remote exploit of a server program 8netAccess(web
Server,httpProtocol,httpPort) 9direct network
access 10hacl(internet,webServer,httpProtocol,htt
pPort) 11attackerLocated(internet) 12networkServ
iceInfo(webServer,httpd,httpProtocol,httpPort,apac
he) 13vulExists(webServer,cve_apache,httpd,remote
Exploit,privEscalation) 14networkServiceInfo(dbSe
rver,mySQL,dbProtocol,dbPort,root) 15vulExists(db
Server,cve_mySQL,mySQL,remoteExploit,privEscalatio
n)
0.2x0.60.12
0.2
14
Example Three
CVE-2006-3747 was identified on web server
CVE-2009-2446 was identified on db server
- Internet is allowed to access the web server
through HTTP protocol and port - Web server is allowed to access the MySQL
database service on the db server - User workstations are allowed to access anywhere
CVE-2009-1918 was identified on user workstations
15
Exploit pre-condition
Exploit post-condition
Lowgt 0.9
16
Possible attack paths
17
(No Transcript)
18
6execCode(webServer,apache) 11execCode(workStat
ion,normalAccount) 12remote exploit of a client
program 13hasAccount(secretary,workStation,norma
lAccount) 14canAccessMaliciousInput(workStation,
secretary,internetExplorer) 15Browsing a
malicious website 17hacl(workStation,internet,ht
tpProtocol,httpPort) 21Browsing a compromised
website 24isUserMachine(workStation) 25isWebBr
owser(internetExplorer) 26inCompetent(secretary)
27vulExists(workStation,cve_IE,internetExplorer,r
emoteExploit,privEscalation) 30attackerLocated(i
nternet) 34hacl(workStation,dbServer,dbProtocol,
dbPort)
19
(No Transcript)
20
Challenge
- How to calculate probabilities in an attack graph
with shared dependencies and cycles. - Bayesian Network
- Frigault, et al., 2008, does not allow cycles
- Assuming independence among attack paths
- Wang, et al., 2008
- Customized data-flow algorithm with dynamic
programming - Homer, et al., 2009
21
Result
execCode(dbServer,root) 0.47 execCode(webServer,a
pache) 0.2 execCode(workStation,normalAccount)
0.74
Before execCode(dbServer,root) 0.12
execCode(webServer,apache) 0.2
22
Prioritization
- Given three hardening options
- Patching the web server
- Patching the db server
- Patching the workstation
- Which one would
- you patch first?
23
Suppose we patch the web server
Before execCode(dbServer,root) 0.47
execCode(webServer,apache) 0.2
execCode(workStation,normalAccount) 0.74
After execCode(dbServer,root) 0.43
execCode(webServer,apache) 0
execCode(workStation,normalAccount) 0.72
24
Now lets patch the db server
Before execCode(dbServer,root) 0.47
execCode(webServer,apache) 0.2
execCode(workStation,normalAccount) 0.74
After execCode(dbServer,root) 0
execCode(webServer,apache) 0.2
execCode(workStation,normalAccount) 0.74
25
What if we block network access from Group 2 to
Internal?
Before execCode(dbServer,root) 0.47
execCode(webServer,apache) 0.2
execCode(workStation,normalAccount) 0.74
After execCode(dbServer,root) 0.12
execCode(webServer,apache) 0.2
execCode(workStation,normalAccount) 0.74
26
Optimizing Security Hardening
Let PrexecCode(dbServer,root)p1
PrexecCode(webServer,apache)p2
PrexecCode(workStation,normalAccount)p3 If
C1,C2,C3 are the cost for the compromise of
these three hosts respectively. Then your
expected loss will be LEC1p1C2p2C3p3 All
the hardening measures H1,H2,Hn have costs as
well. If you have a maximum dollar amount H to
spend on hardening, and you want to minimize your
LE, what would you do?
27
Challenges
- Scalability of metric calculation
- Heavily depends on the connectivity of attack
graphs - Exponential in the worst case
- Imprecise input problem
- How sensitive is the outcome to the input
component metrics? - Approximation algorithms to trade precision for
scalability? - Optimization techniques
28
Summary
- Quantitative security risk metrics are important
in making sensible decisions in security
hardening - People are already doing it in an ad-hoc way
without any scientific basis - We want to transform it from a black art to a
science
29
If you cannot measure it, you cannot improve it.
---Lord Kelvin