Secure Knowledge Management - PowerPoint PPT Presentation
1 / 1
Title:
Secure Knowledge Management
Description:
... envisions an industry in which knowledge service providers may extract knowledge ... Analyze incremental knowledge extraction (ongoing preliminary results ... – PowerPoint PPT presentation
Number of Views:14
Avg rating:3.0/5.0
Title: Secure Knowledge Management
1
Secure Knowledge Management
Shouhuai Xu (UTSA) Weining Zhang (UTSA) Ravi
Sandhu (GMU)
- Motivation DataBase Management Systems (DBMS)
have been widely and successfully used to manage
enterprises data assets. Due to privacy concerns
and regulations, data cannot be shared among
parties as one may have wanted. This means that
the knowledge (e.g., decision trees) hidden in
the data cannot be shared. This project envisions
an industry in which knowledge service providers
may extract knowledge from many owners data to
serve customers need for knowledge in their
business activities.
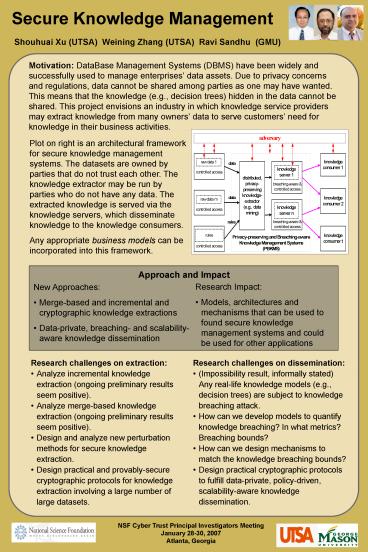
Plot on right is an architectural framework for
secure knowledge management systems. The datasets
are owned by parties that do not trust each
other. The knowledge extractor may be run by
parties who do not have any data. The extracted
knowledge is served via the knowledge servers,
which disseminate knowledge to the knowledge
consumers. Any appropriate business models can be
incorporated into this framework.
Graphics goes in this box. Graph captions in
Helvetica, 36pt, white.
Approach and Impact
- Research Impact
- Models, architectures and mechanisms that can be
used to found secure knowledge management systems
and could be used for other applications
- New Approaches
- Merge-based and incremental and cryptographic
knowledge extractions - Data-private, breaching- and scalability-aware
knowledge dissemination
- Research challenges on extraction
- Analyze incremental knowledge extraction (ongoing
preliminary results seem positive). - Analyze merge-based knowledge extraction (ongoing
preliminary results seem positive). - Design and analyze new perturbation methods for
secure knowledge extraction. - Design practical and provably-secure
cryptographic protocols for knowledge extraction
involving a large number of large datasets.
- Research challenges on dissemination
- (Impossibility result, informally stated) Any
real-life knowledge models (e.g., decision trees)
are subject to knowledge breaching attack. - How can we develop models to quantify knowledge
breaching? In what metrics? Breaching bounds? - How can we design mechanisms to match the
knowledge breaching bounds? - Design practical cryptographic protocols to
fulfill data-private, policy-driven,
scalability-aware knowledge dissemination.