Alignment PowerPoint PPT Presentation
Title: Alignment
1
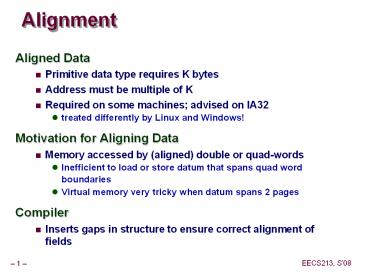
Alignment
- Aligned Data
- Primitive data type requires K bytes
- Address must be multiple of K
- Required on some machines advised on IA32
- treated differently by Linux and Windows!
- Motivation for Aligning Data
- Memory accessed by (aligned) double or quad-words
- Inefficient to load or store datum that spans
quad word boundaries - Virtual memory very tricky when datum spans 2
pages - Compiler
- Inserts gaps in structure to ensure correct
alignment of fields
2
Specific Cases of Alignment
- Size of Primitive Data Type
- 1 byte (e.g., char)
- no restrictions on address
- 2 bytes (e.g., short)
- lowest 1 bit of address must be 02
- 4 bytes (e.g., int, float, char , etc.)
- lowest 2 bits of address must be 002
- 8 bytes (e.g., double)
- Windows (and most other OSs instruction sets)
- lowest 3 bits of address must be 0002
- Linux
- lowest 2 bits of address must be 002
- i.e., treated the same as a 4-byte primitive data
type - 12 bytes (long double)
- Linux
- lowest 2 bits of address must be 002
- i.e., treated the same as a 4-byte primitive data
type
3
Satisfying Alignment with Structures
- Offsets Within Structure
- Must satisfy elements alignment requirement
- Overall Structure Placement
- Each structure has alignment requirement K
- Largest alignment of any element
- Initial address structure length must be
multiples of K - Example (under Windows)
- K 8, due to double element
struct S1 char c int i2 double v
p
c
i0
i1
v
p0
p4
p8
p16
p24
Multiple of 4
Multiple of 8
Multiple of 8
Multiple of 8
4
Linux vs. Windows
struct S1 char c int i2 double v
p
- Windows
- K 8, due to double element
- Linux
- K 4 double treated like a 4-byte data type
5
Overall Alignment Requirement
struct S2 double x int i2 char c
p
p must be multiple of 8 for Windows 4 for
Linux
struct S3 float x2 int i2 char c
p
p must be multiple of 4 (in either OS)
6
Ordering Elements Within Structure
struct S4 char c1 double v char c2
int i p
10 bytes wasted space in Windows
struct S5 double v char c1 char c2
int i p
2 bytes wasted space
7
Arrays of Structures
- Principle
- Allocated by repeating allocation for array type
- In general, may nest arrays structures to
arbitrary depth
struct S6 short i float v short j
a10
a12
a20
a16
a24
8
Accessing Element within Array
- Compute offset to start of structure
- Compute 12i as 4(i2i)
- Access element according to its offset within
structure - Offset by 8
- Assembler gives displacement as a 8
- Linker must set actual value
struct S6 short i float v short j
a10
short get_j(int idx) return aidx.j
eax idx leal (eax,eax,2),eax
3idx movswl a8(,eax,4),eax
a12i
a12i8
9
Satisfying Alignment within Structure
- Achieving Alignment
- Starting address of structure array must be
multiple of worst-case alignment for any element - a must be multiple of 4
- Offset of element within structure must be
multiple of elements alignment requirement - vs offset of 4 is a multiple of 4
- Overall size of structure must be multiple of
worst-case alignment for any element - Structure padded with unused space to be 12 bytes
struct S6 short i float v short j
a10
Multiple of 4
Multiple of 4
10
Alignment Quiz
- For each struct, give the offset of each field,
total size, and struct alignment (1, 2 or 4 byte)
required in Linux. - struct P1 int i char c int j char d
i _1_ c _2_ j _3_ d _4_ total _5_
alignment _6_ - struct P2 int i char c char d int j
i _7_ c _8_ d _9_ j _10_ total
_11_ alignment _12_ - struct P3 struct P1 a2 struct P2 p
a _13_ p _14_ total _15_ alignment
_16_
11
Union Allocation
- Principles
- Overlay union elements
- Allocate according to largest element
- Can only use one field at a time
union U1 char c int i2 double v
up
struct S1 char c int i2 double v
sp
(Windows alignment)
12
Using Union to Access Bit Patterns
typedef union float f unsigned u
bit_float_t
float bit2float(unsigned u) bit_float_t arg
arg.u u return arg.f
u
f
unsigned float2bit(float f) bit_float_t arg
arg.f f return arg.u
0
4
- Get direct access to bit representation of float
- bit2float generates float with given bit pattern
- NOT the same as (float) u
- float2bit generates bit pattern from float
- NOT the same as (unsigned) f
13
Byte Ordering Revisited
- Idea
- Short/long/quad words stored in memory as 2/4/8
consecutive bytes - Which is most (least) significant?
- Can cause problems when exchanging binary data
between machines - Big Endian
- Most significant byte has lowest address
- PowerPC, Sparc
- Little Endian
- Least significant byte has lowest address
- Intel x86, Alpha
14
Byte Ordering Example
union unsigned char c8
unsigned short s4 unsigned int i2
unsigned long l1 dw
c3
c2
c1
c0
c7
c6
c5
c4
s1
s0
s3
s2
i0
i1
l0
15
Byte Ordering Example (Cont).
int j for (j 0 j lt 8 j) dw.cj 0xf0
j printf("Characters 0-7 0xx,0xx,0xx,0x
x,0xx,0xx,0xx,0xx\n", dw.c0, dw.c1,
dw.c2, dw.c3, dw.c4, dw.c5, dw.c6,
dw.c7) printf("Shorts 0-3
0xx,0xx,0xx,0xx\n", dw.s0, dw.s1,
dw.s2, dw.s3) printf("Ints 0-1
0xx,0xx\n", dw.i0, dw.i1) printf("Lo
ng 0 0xlx\n", dw.l0)
16
Byte Ordering on x86
Little Endian (least significant byte has lowest
address)
Output on Pentium
Characters 0-7 0xf0,0xf1,0xf2,0xf3,0xf4,0xf5,0
xf6,0xf7 Shorts 0-3 0xf1f0,0xf3f2,0xf5f4,
0xf7f6 Ints 0-1 0xf3f2f1f0,0xf7f6f5f4
Long 0 f3f2f1f0
17
Byte Ordering on Sun
Big Endian (most significant byte has lowest
address)
Output on Sun
Characters 0-7 0xf0,0xf1,0xf2,0xf3,0xf4,0xf5,0
xf6,0xf7 Shorts 0-3 0xf0f1,0xf2f3,0xf4f5,
0xf6f7 Ints 0-1 0xf0f1f2f3,0xf4f5f6f7
Long 0 0xf0f1f2f3
18
Byte Ordering on Alpha
Little Endian
Output on Alpha
Characters 0-7 0xf0,0xf1,0xf2,0xf3,0xf4,0xf5,0
xf6,0xf7 Shorts 0-3 0xf1f0,0xf3f2,0xf5f4,
0xf7f6 Ints 0-1 0xf3f2f1f0,0xf7f6f5f4
Long 0 0xf7f6f5f4f3f2f1f0
19
Summary
- Arrays in C
- Contiguous allocation of memory
- Pointer to first element
- No bounds checking
- Compiler Optimizations
- Compiler often turns array code into pointer code
(zd2int) - Uses addressing modes to scale array indices
- Lots of tricks to improve array indexing in loops
- Structures
- Allocate bytes in order declared
- Pad in middle and at end to satisfy alignment
- Unions
- Overlay declarations
20
Machine-Level Programming VMiscellaneous
TopicsApr 28, 2008
EECS213
- Topics
- Buffer Overflow
- Floating Point Code
21
Internet Worm and IM War
- November, 1998
- Internet Worm attacks thousands of Internet
hosts. - How did it happen?
- July, 1999
- Microsoft launches MSN Messenger (instant
messaging system). - Messenger clients can access popular AOL Instant
Messaging Service (AIM) servers
AIM client
AIM server
MSN client
MSN server
AIM client
22
Internet Worm and IM War (cont.)
- August 1999
- Mysteriously, Messenger clients can no longer
access AIM servers. - Microsoft and AOL begin the IM war
- AOL changes server to disallow Messenger clients
- Microsoft makes changes to clients to defeat AOL
changes. - At least 13 such skirmishes.
- How did it happen?
- The Internet Worm and AOL/Microsoft War were both
based on stack buffer overflow exploits! - many Unix functions do not check argument sizes.
- allows target buffers to overflow.
23
String Library Code
- Implementation of Unix function gets
- No way to specify limit on number of characters
to read - Similar problems with other Unix functions
- strcpy Copies string of arbitrary length
- scanf, fscanf, sscanf, when given s conversion
specification
/ Get string from stdin / char gets(char
dest) int c getc() char p dest
while (c ! EOF c ! '\n') p
c c getc() p '\0'
return dest
24
Vulnerable Buffer Code
/ Echo Line /void echo() char buf4
/ Way too small! / gets(buf)
puts(buf)
int main() printf("Type a string")
echo() return 0
25
Buffer Overflow Executions
unixgt./bufdemo Type a string123 123
unixgt./bufdemo Type a string12345 Segmentation
Fault
unixgt./bufdemo Type a string12345678 Segmentation
Fault
26
Buffer Overflow Stack
/ Echo Line /void echo() char buf4
/ Way too small! / gets(buf)
puts(buf)
echo pushl ebp Save ebp on stack movl
esp,ebp subl 20,esp Allocate space on
stack pushl ebx Save ebx addl -12,esp
Allocate space on stack leal -4(ebp),ebx
Compute buf as ebp-4 pushl ebx Push buf on
stack call gets Call gets . . .
27
Buffer Overflow Stack Example
unixgt gdb bufdemo (gdb) break echo Breakpoint 1
at 0x8048583 (gdb) run Breakpoint 1, 0x8048583 in
echo () (gdb) print /x (unsigned )ebp 1
0xbffff8f8 (gdb) print /x ((unsigned )ebp
1) 3 0x804864d
Before call to gets
8048648 call 804857c ltechogt 804864d mov
0xffffffe8(ebp),ebx Return Point
28
Buffer Overflow Example 1
Before Call to gets
Input 123
No Problem
29
Buffer Overflow Stack Example 2
Input 12345
Saved value of ebp set to 0xbfff0035 Bad news
when later attempt to restore ebp
echo code
8048592 push ebx 8048593 call 80483e4
lt_init0x50gt gets 8048598 mov
0xffffffe8(ebp),ebx 804859b mov ebp,esp
804859d pop ebp ebp gets set to invalid
value 804859e ret
30
Buffer Overflow Stack Example 3
Input 12345678
ebp and return address corrupted
8048648 call 804857c ltechogt 804864d mov
0xffffffe8(ebp),ebx Return Point
31
Malicious Use of Buffer Overflow
Stack after call to gets()
void foo() bar() ...
foo stack frame
return address A
B
data written by gets()
pad
void bar() char buf64 gets(buf) ...
exploit code
bar stack frame
B
- Input string contains byte representation of
executable code - Overwrite return address with address of buffer
- When bar() executes ret, will jump to exploit code
32
Exploits Based on Buffer Overflows
- Buffer overflow bugs allow remote machines to
execute arbitrary code on victim machines. - Internet worm
- Early versions of the finger server (fingerd)
used gets() to read the argument sent by the
client - finger droh_at_cs.cmu.edu
- Worm attacked fingerd server by sending phony
argument - finger exploit-code padding new-return-address
- exploit code executed a root shell on the victim
machine with a direct TCP connection to the
attacker.
33
Exploits Based on Buffer Overflows
- Buffer overflow bugs allow remote machines to
execute arbitrary code on victim machines. - IM War
- AOL exploited existing buffer overflow bug in AIM
clients - exploit code returned 4-byte signature (the
bytes at some location in the AIM client) to
server. - When Microsoft changed code to match signature,
AOL changed signature location.
34
- Date Wed, 11 Aug 1999 113057 -0700 (PDT)
- From Phil Bucking ltphilbucking_at_yahoo.comgt
- Subject AOL exploiting buffer overrun bug in
their own software! - To rms_at_pharlap.com
- Mr. Smith,
- I am writing you because I have discovered
something that I think you - might find interesting because you are an
Internet security expert with - experience in this area. I have also tried to
contact AOL but received - no response.
- I am a developer who has been working on a
revolutionary new instant - messaging client that should be released later
this year. - ...
- It appears that the AIM client has a buffer
overrun bug. By itself - this might not be the end of the world, as MS
surely has had its share. - But AOL is now exploiting their own buffer
overrun bug to help in - its efforts to block MS Instant Messenger.
It was later determined that this email
originated from within Microsoft!
35
Code Red Worm
- History
- June 18, 2001. Microsoft announces buffer
overflow vulnerability in IIS Internet server - July 19, 2001. over 250,000 machines infected by
new virus in 9 hours - White house must change its IP address. Pentagon
shut down public WWW servers for day - When We Set Up CSAPP Web Site
- Received strings of form
- GET /default.ida?NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN
NNNNNN....NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN
Nu9090u6858ucbd3u7801u9090u6858ucbd3u7801
u9090u6858ucbd3u7801u9090u9090u8190u00c3u0
003u8b00u531bu53ffu0078u0000u00a - HTTP/1.0" 400 325 "-" "-"
36
Code Red Exploit Code
- Starts 100 threads running
- Spread self
- Generate random IP addresses send attack string
- Between 1st 19th of month
- Attack www.whitehouse.gov
- Send 98,304 packets sleep for 4-1/2 hours
repeat - Denial of service attack
- Between 21st 27th of month
- Deface servers home page
- After waiting 2 hours
37
Code Red Effects
- Later Version Even More Malicious
- Code Red II
- As of April, 2002, over 18,000 machines infected
- Still spreading
- Paved Way for NIMDA
- Variety of propagation methods
- One was to exploit vulnerabilities left behind by
Code Red II
38
Avoiding Overflow Vulnerability
/ Echo Line /void echo() char buf4
/ Way too small! / fgets(buf, 4, stdin)
puts(buf)
- Use Library Routines that Limit String Lengths
- fgets instead of gets
- strncpy instead of strcpy
- Dont use scanf with s conversion specification
- Use fgets to read the string