A Definition of Biometrics - PowerPoint PPT Presentation
1 / 28
Title:
A Definition of Biometrics
Description:
'The process of identifying and verifying people based upon ... Has been used to positively identify the famous National Geographic picture of 'The Afghan Girl' ... – PowerPoint PPT presentation
Number of Views:265
Avg rating:3.0/5.0
Title: A Definition of Biometrics
1
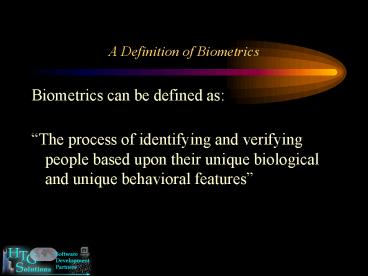
A Definition of Biometrics
- Biometrics can be defined as
- The process of identifying and verifying people
based upon their unique biological and unique
behavioral features
2
The Two Major Types of Biometrics
- There are two major types of biometrics
- Physical biometrics
- The biological data that is captured-includes
the unique features from the finger, the hand,
the face, the eye, and the voice. - Behavioral biometrics
- The non-biological data that is
captured-includes the unique features from the
way we sign our name and the way we type.
3
The Biometric Technologies
- Physical Biometric Technologies
- Hand Geometry Recognition
- Fingerprint Recognition
- Facial Recognition
- Voice Recognition
- Iris/Retinal Recognition
- Behavioral Biometric Technologies
- Signature Recognition
- Keystroke Recognition
4
Physical BiometricsHand Geometry Recognition
Technology
- Works by extracting a 3-D image of the hand (the
top and sides), 96 measurements are taken - Recognized as probably the oldest biometric
technology - Popular applications include physical access
entry and time/attendance applications - Disadvantages Cannot be used for high security
situations, not enough unique features in
hand
5
Physical BiometricsFingerprint Recognition
Technology
- Has been around a very long time, along with hand
geometry scanning - Works by extracting the the breaks and
discontinuities in the valleys and ridges of the
fingerprint-also known as the minutae - Most popular application is physical access
entry, and Single Sign On Solutions for network
security - Disadvantages An extremely damaged
fingerprint will be rendered useless
6
Physical BiometricsFacial Recognition Technology
- Has received the most attention since 9/11
- Misconception that Facial Recognition will be as
good or even better than the Human Brain for
verification and identification of individuals - Works by taking many images of the face, and
extracting unique features of the ears, eyes,
nose, mouth, and cheeks - Popular venues for Facial Recognition include
casinos and airports - Disadvantages privacy rights issues, changes in
the environmental settings, and physical changes
in the features of the face-such as weight
gain/loss, addition or removal of facial hair,
etc.
7
Physical BiometricsVoice Recognition Technology
- Works by recognizing the unique characteristics
of the voice - Text phrase is recited numerous times, and voice
inflections are captured - Popular applications telephony based
verifications (such as accessing credit card
account info, conducting financial transactions,
trading financial instruments, etc.) - Disadvantages extraneous noises in the
environment and physical ailments (cold or flu)
of user
8
Physical BiometricsIris/Retinal Recognition
Technology
- Iris and Retinal Recognition have often been
confused as being similar, however, the two are
very different - Both have been deemed to be among the most
reliable and stable of the biometric technologies
available - The Iris and Retina rarely change over the
lifetime of an individual
9
Physical BiometricsIris Recognition Technology
- Works by extracting the unique features in the
texture and patterns of the iris, (located in the
front of the eye-the colored region between the
pupil and the sclera) - Popular applications expediting the immigration
process at airports, physical access entry, and
network security - Has been used to positively identify the famous
National Geographic picture of The Afghan Girl
10
Physical BiometricsThe Iris
11
Physical BiometricsRetinal Recognition Technology
- Works by examining the unique pattern of blood
vessels in the retina (located at the back of the
eye, near the optic nerve) - Used for extremely high security applications,
such as physical access entry into highly secure
areas of military or government installations - Disadvantages Deemed to be very user invasive
can cause much user discomfort and requires the
most cooperation from the user, when compared to
other biometric technologies
12
Physical BiometricsThe Retina
13
Behavioral BiometricsSignature Recognition
Technology
- Examines the way in which we sign our name, not
the signature itself - The unique behavioral characteristics are the
timing, speed, and pressure applied during the
course of signing - It has a high level of resistance to
impostors-easy to forge a signature, but not the
behavioral characteristics. Also deemed to be a
noninvasive biometric technology - However, it has not reached a dominant level of
market share like Fingerprint Recognition and
Hand Geometry Recognition. There have been very
limited uses in the financial sector
14
Behavioral BiometricsKeystroke Recognition
Technology
- Examines the way in which we type on a computer
keyboard - In order to capture the unique features, an
individual must type a specific group of words
approximately 15 times-very often it is the
Username and Password - The unique features include
- The cumulative typing speed
- The elapsed time between consecutive
keystrokes - The time that each key is held down
- The frequency of use of other keys (function
and numeric keys) - The sequence utilized when typing a capital
letter (Shift key or letter key released
first?) - Keystroke Recognition is a 100 software
solution-therefore, all that is needed is a
keyboard-no need to install new hardware
15
Biometric Technology Solutions and Applications
- Biometric Technology has solutions and
applications in the following market sectors - Time and Attendance
- Physical Access Entry
- Computer and Network Logon
16
Biometric Technology Solutions and Applications
Time and Attendance
- Time and Attendance refers to the clocking in and
clocking out of hourly wage employees, and
keeping track of hours worked - Very often, some sort of timecard is used, an
employee ID number, or a Social Security number
for the purposes of clocking in and out - Here lies the problem-an employee could give
another employee their Identification Number, and
have that employee clock in for them, when they
have not even appeared at all for their shift - This is referred to as Buddy Punching
17
Biometric Technology Solutions and Applications
Time and Attendance
- Biometric Technology has been utilized to help
eliminate the problem of Buddy Punching - Many Time and Attendance applications have
utilized Hand Geometry Recognition as the tool of
choice - The employees hand becomes their Clocking In and
Clocking Out mechanism - Since nobody can share their hand, and it is
unique, the problem of Buddy Punching
almost becomes zero
18
Biometric Technology Solutions and Applications
Time and Attendance
- Places where Hand Geometry Recognition is being
used - Owens-Illinois Krispy Kreme Doughnuts Decatur
Hotel Group (in New Orleans) First Bank Puerto
Rico and McDonalds - Advantages of using Biometric Technology for Time
and Attendance - Cost of issuing and replacing Timecards
eliminated - Very accurate Payroll Calculations
and Employee Attendance Records, reduction
in paperwork - Payroll Policies can be applied consistently
and fairly, especially to Overtime and Holiday
Pay
19
Biometric Technology Solutions and Applications
A Hand Geometry Scanner
20
Biometric Technology Solutions and Applications
Physical Access Entry
- Biometric Technology has also made its mark in
Physical Access Entry scenarios - The need to have a lock and key system has become
almost obsolete - Your Hand, Finger, or Eye can be used to unlock a
door - However, most systems today use Hand Geometry
Recognition and Fingerprint Recognition
21
Biometric Technology Solutions and Applications
Physical Access Entry
- Typically, the Hand Geometry Scanner or
Fingerprint Scanner is mounted to a wall, and an
electromagnetic lock strike attached to the door
is wired directly to the Biometric Device - Once the Hand Geometry or Fingerprint has been
verified by the Biometric System, a signal is
sent to the lock strike to unlock the door - In Physical Access Entry scenarios, Biometric
Devices can operate in a standalone or networked
mode, where one door or multiple doors can be
unlocked and opened
22
Biometric Technology Solutions and Applications
Physical Access Entry
- Many types of organizations are using this type
of security, ranging from International Airports
to Military Installations to University
Dormitories to Child Daycare Centers - Advantages of using Biometric Technology
- Only personnel enrolled in the Biometric System
can gain entry - Cost of issuing/replacing ID Cards becomes
almost zero-your Hand Geometry or Fingerprint is
the key - Efficiency and Ease of Use Verification by
Biometric System in less than 1 Second
23
Biometric Technology Solutions and Applications
Physical Access Entry
- Many organizations and businesses today are
adopting the implementation of a Multi-Modal
Security Solution-a Two Tier Security System - This involves using more than one biometric
technology together in order to maximize the
level of security - A typical example of this is using a Hand
Geometry Scanner at the main entry point, and
then using a Fingerprint Scanner at more
sensitive points within the place of business
24
Biometric Technology Solutions and Applications
A Fingerprint Scanner
25
Biometric Technology Solutions and Applications
Computer and Network Logon
- Typically, in order to gain access to a network,
we have to type in an established Username and
Password - However, with the growth of the Internet and Web
Based Applications, the need for multiple
Usernames and Passwords has grown exponentially - As a result, people tend to write down their
Usernames and Passwords on Post Its and leave
them on their computer monitor - This has led to a substantial increase in the
costs of password administration and
maintenance-now at 250 per employee per year
26
Biometric Technology Solutions and Applications
Computer and Network Logon
- The use of Biometric Technology can eliminate the
need for Usernames and Passwords - Your Fingerprint or Iris becomes the mechanism
for gaining access to the network or your
computer - Fingerprint Recognition and Iris Recognition are
the primary tools utilized - This is referred to as Single Sign On
Solutions- because only one piece of
identification, your biometric, is needed
27
Biometric Technology Solutions and Applications
Computer and Network Logon
- These Single Sign On Solution devices come
embedded onto a keyboard, onto a mouse, or into a
small camera (for Iris Recognition) - Advantages of using Biometric Technology for
Computer and Network Logon - Password administration and maintenance costs
become virtually zero - No need to remember multiple Usernames and
Passwords - Use of a Biometric is much more secure than
Usernames and Passwords-after all, a Biometric
cannot be shared - You cannot forget you Biometric-unlike
Usernames and Passwords
28
Biometric Technology Solutions and Applications
A Network Logon Device