Gridworld PowerPoint PPT Presentations
All Time
Recommended
Make learning fun and competitive. In the following areas: AI software design and ... Coding in lectures quite nerve-wracking and very instructive to students ...
| PowerPoint PPT presentation | free to view
GridWorld Introduction Peter Cowling University of Bradford P.I.Cowling@bradford.ac.uk Outline Aims of the project Design Philosophy Outcomes The student ...
| PowerPoint PPT presentation | free to view
Online server results, allows students to compete and allows agents to gauge tactics. ... GridWorld was fun: To use, develop for, and to play. ...
| PowerPoint PPT presentation | free to view
Security a player AI could crash the server. Uploading - the FTP could deadlock. Memory leaks ... types. Complete move to .Net 2.0. Greater use of AppDomains ...
| PowerPoint PPT presentation | free to view
OGSA-DAI Scenarios. and Requirements. OGSA-DAI for Developers. GridWorld 2006, Washington DC ... Arrange visits and collaborations. Contribute your own extensions ...
| PowerPoint PPT presentation | free to view
And enable Web sites to get proxy certificates for authenticated users. GridWorld 2006 ... Authentication module stores the proxy in the proxyStore named by ...
| PowerPoint PPT presentation | free to view
Title: Using Hierarchical Reinforcement Learning to Solve a Problem with Multiple Conflicting Sub-problems Author: Stephen Robertson Last modified by
| PowerPoint PPT presentation | free to download
... declining enrollments in Computer Science programs, many new tools have been ... Daniel Rogers, Ph.D. SUNY Brockport. Technology Education ...
| PowerPoint PPT presentation | free to view
Proof (sketch) Pieter Abbeel and Andrew Y. Ng. Algorithm (projection version) w(1) w(2) ... Proof (sketch) Pieter Abbeel and Andrew Y. Ng. Apprenticeship Learning via ...
| PowerPoint PPT presentation | free to download
RL formalism. Assume that at each time step, our system is in some state st. ... RL formalism. Markov Decision Process (S,A,P,s0,R) W.l.o.g. we assume. Policy ...
| PowerPoint PPT presentation | free to download
Pieter Abbeel and Andrew Y. Ng. Apprenticeship Learning. Learning from ... Pieter Abbeel and Andrew Y. Ng. Preliminaries. Markov Decision ... and Andrew Y. ...
| PowerPoint PPT presentation | free to download
Warm-Up: Find the output to the following code segments: String state = 'Mississippi' ... Immutability of Strings. H. Comparing Strings. Ch29HomeworkAssign Set #3: ...
| PowerPoint PPT presentation | free to view
Using Hierarchical Reinforcement Learning to Solve a Problem ... Explore the terrain Collect soil samples Return to base for refuelling My Project Apply ...
| PowerPoint PPT presentation | free to download
Reinforcement Learning Eligibility Traces Content n-step TD prediction Forward View of TD ...
| PowerPoint PPT presentation | free to view
APCS AB. Turn-In/Review: Lab8 a c. In-Class/Homework: Lab8 d g ... Exercises 4-6. Group Activity (2-4 per Group) APCS - AB. Warm-Up: Binary Tree Worksheet 1 ...
| PowerPoint PPT presentation | free to view
WELCOME TO OPEN HOUSE Vicki Coffman Computer Science Pre-AP Advanced Placement CS3 Pre-AP Topics Variables and constants Data types Program input/output Data ...
| PowerPoint PPT presentation | free to view
Polymorphism - What is polymorphism? - Examples - public, private, and protected How is it done in Java? Done automatically!!! COOL STUFF!!! Example - BankAccount ...
| PowerPoint PPT presentation | free to view
Never cut traces. Disadvantage: Complicated to implement ... Critic: On-policy learning of Vp. Use TD(l) as described before. ...
| PowerPoint PPT presentation | free to view
Shout dt backwards over time. The strength of your voice decreases with temporal distance by gl ... Watkins: Zero out eligibility trace after a non-greedy action. ...
| PowerPoint PPT presentation | free to download
Title: Testing Extensible Design Patterns in OO Frameworks through Scenario Templates Author: Christina Last modified by: Robert Lingard Created Date
| PowerPoint PPT presentation | free to download
Focus first on policy evaluation, or prediction, methods. Then extend ... Statistics of arrivals and departures are unknown. n=10, h=.5, p=.06. Apply R-learning ...
| PowerPoint PPT presentation | free to view
Show how DP can be used to compute value functions, and hence, optimal policies. Discuss efficiency and utility of DP. Objectives of this chapter: ...
| PowerPoint PPT presentation | free to view
Opensciencegrid.org. OSG User and Virtual Organization Support. Rob Quick. 11 September 2006 ... VO Users Contact their VO support center to begin the ...
| PowerPoint PPT presentation | free to download
for APCS Success Stuart Reges, Principal Lecturer University of Washington H l ne Martin, CS teacher Garfield High School
| PowerPoint PPT presentation | free to download
Finding Optimal Solutions to Cooperative Pathfinding Problems Trevor Standley and Rich Korf Computer Science Department University of California, Los Angeles
| PowerPoint PPT presentation | free to view
task of learning from observing an expert/teacher. Previous work: ... IRL step: Estimate expert's reward function R(s)= wT (s) by solving following QP ...
| PowerPoint PPT presentation | free to download
Experience-Oriented Artificial Intelligence Rich Sutton with special thanks to Michael Littman, Doina Precup, Satinder Singh, David McAllester, Peter Stone, Lawrence ...
| PowerPoint PPT presentation | free to view
The central process by which the abundance of life forms have come to exist. ... Finches. Origin of Species - 1859. Expression of Emotion in Man and Animals - 1872 ...
| PowerPoint PPT presentation | free to download
When offline, the new V(s) will be for the next episode. Error Reduction Property ... Two cases: Both behavior and estimation policies take the greedy path. ...
| PowerPoint PPT presentation | free to view
Pipe. Activity Processing (Current Release) ... Pipe. Activity Interface. All activities must implement the Activity interface ...
| PowerPoint PPT presentation | free to view
Idea: Look farther into the future when you do TD backup (1, 2, 3, ..., n steps) ... Use V to estimate remaining return. n-step TD: 2 step return: n-step return: ...
| PowerPoint PPT presentation | free to view
R. S. Sutton and A. G. Barto: Reinforcement Learning: An Introduction. 1 ... R. S. Sutton and A. G. Barto: Reinforcement Learning: An Introduction. 13 ...
| PowerPoint PPT presentation | free to view
Apprentissage par renforcement (Reinforcement Learning (RL)) Chapitre ... Reinforcement Learning: An Introduction http://www-anw.cs.umass.edu/~rich/book ...
| PowerPoint PPT presentation | free to view
We lend our LEGO NXT robots and PicoCricket kits. Up to 3 weeks at a time ... LEGO, Alice, PicoCrickets, Scratch. YWCA Teen Girls in Tech ...
| PowerPoint PPT presentation | free to view
These methods bootstrap and sample, combining aspects of DP and MC methods ... What is common to all three classes of methods? DP, MC, TD ...
| PowerPoint PPT presentation | free to view
Use bounds on girth of graphs instead. Analyzing greedy localization ... Relate to bounds on girth (shortest cycle) from Euler's formula, ... Girth: length ...
| PowerPoint PPT presentation | free to download
DAS-5341: M todos de Solu o para Problemas de Aprendizagem por Refor o Prof. Eduardo Camponogara
| PowerPoint PPT presentation | free to view
K nstliche Neuronale Netze Stefan Hartmann Forschungszentrum caesar Warum Neuronale Netze? Neuronale Netze sind eine von der Natur inspirierte Methode, Computer ...
| PowerPoint PPT presentation | free to view
What are the belief-space properties that allow some POMDP problems to be approximated efficiently, explaining the point-based algorithms success?
| PowerPoint PPT presentation | free to download
Jim Dowling, Eoin Curran, Raymond Cunningham and Vinny Cahill, 'Collaborative ... Actions ={delegation} U {DOP actions} U {discovery} Connection Costs ...
| PowerPoint PPT presentation | free to view
Machine Learning
| PowerPoint PPT presentation | free to download
The ProxyStore repository stores proxies with unencrypted keys and allows for ... Calls MyProxy-logon which verifies the password and delegates a proxy ...
| PowerPoint PPT presentation | free to view
'babysitter' scripts 'babysitter' scripts are common but in general they ... Conceptual details of BabySitter. Resource manager and handler ... Past: babysitter ...
| PowerPoint PPT presentation | free to download
callbacks for attempts to get or set the value. Apps can be notified when ... Callback-driven notification. User has to deal with XML wildcard messages. Usage: ...
| PowerPoint PPT presentation | free to view
Keep track of services and be warned of failures ... Warn on error conditions. All of these have common needs, and are built on a common framework ...
| PowerPoint PPT presentation | free to view
... on Site boundary. Edge Services Framework (ES Wafers). User Workspace on WNs ... software in area that is read-only by all cmsgrid user jobs running on site/campus. ...
| PowerPoint PPT presentation | free to view
Tabula Rasa. No background knowledge other than the training examples. Knowledge-based learning ... Tabula Rasa, fully supervised. Qns: How do we test a learner? ...
| PowerPoint PPT presentation | free to download
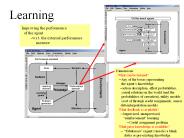
Learning Improving the performance of the agent-w.r.t. the external performance measure Dimensions: What can be learned?--Any of the boxes representing
| PowerPoint PPT presentation | free to download
We provide basic infrastructure to get you one step closer. 5. GT Domain Areas. Core runtime ... MyProxy (One time password support) 17. Other Security Services ...
| PowerPoint PPT presentation | free to view
A:This presentation will cover the features, interface, architecture, ... But not as general as Condor DAG, etc. Asynchronous monitoring. 7. Job Submission Options ...
| PowerPoint PPT presentation | free to view
Reinforcement Learning and Soar Shelley Nason Reinforcement Learning Reinforcement learning: Learning how to act so as to maximize the expected cumulative value of a ...
In-class assignment & discussion. Overview day 2 (Tuesday 9-12) ... TD-Gammon: Tesauro. world's best backgammon program. Elevator Control: Crites & Barto ...
Ability to handle probabilistic action effects. An action may lead to success ... Automatically handle parameter controlling randomness in action choice ...
... xml.rels ppt/s/_rels/18.xml.rels ppt/s/_rels/17.xml. ... oleObject27.bin ppt/media/image37.png docProps/thumbnail.jpeg ppt/media/image42. ...