Network Security Architecture PowerPoint PPT Presentations
All Time
Recommended
VRS Technologies presenting about network cabling architecture and network cabling services in Dubai.
| PowerPoint PPT presentation | free to download
TinySec: A Link Layer Security Architecture for Wireless Sensor Networks Chris Karlof, Naveen Sastry & David Wagner Dr. Xiuzhen Cheng Department of Computer Science
| PowerPoint PPT presentation | free to download
Network Security Sritrusta Sukaridhoto Netadmin & Head of Computer Network Lab EEPIS-ITS Tentang aku Seorang pegawai negeri yang berusaha menjadi dosen yang baik,...
| PowerPoint PPT presentation | free to view
IPRO media provides the best network security to its customers. Network security is very important to secure your business. IPRO media provides the best network security specialist to each customer. It updates all information about network security. To check any update, you can visit on our website Ipromdia.
| PowerPoint PPT presentation | free to download
Network Security Techniques by Bruce Roy Millard Division of Computing Studies Arizona State University Bruce.Millard@asu.edu What is Network Security Hardware ...
| PowerPoint PPT presentation | free to view
Passcert provides the latest and valid Cisco Security Architecture 700-760 Dumps to help you pass your exam successfully.
| PowerPoint PPT presentation | free to download
The latest version of Security+ SY0-601 have 5 Domains: Domain 1.0: Attacks, Threats, and Vulnerabilities (24%) Domain 2.0: Architecture and Design (21%) Domain 3.0: Implementation (25%) Domain 4.0: Operations and Incident Response (16%) Domain 5.0: Governance, Risk, and Compliance (14%) In this blog, we discuss the second domain, Architecture and Design.
| PowerPoint PPT presentation | free to download
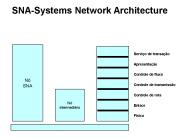
SNA-Systems Network Architecture N SNA Servi o de transa o Apresenta o Controle de fluxo Controle de transmiss o Controle de rota Enlace F sico
| PowerPoint PPT presentation | free to download
The ipromedia is provides training to general staff regarding to security issues and we develop policies that govern how employees can access company information using a smartphone, laptop and home computer.
| PowerPoint PPT presentation | free to download
Network Scanning is a process of identifies the active hosts (Clients and servers) on a network and their activities to attack a network and protect from vulnerabilities and hackers. It becomes complex when you are working in a large organization where hundreds of networks are connected. So every network administrator looking for the best network security tools for easier their process. Here we listed the top 10 network security tools of 2019 https://hackercombat.com/ten-best-network-scanning-tools-for-network-security/
| PowerPoint PPT presentation | free to download
Velevate Provide Network Security Services In UK. This Company Test Your Network With Wonderfull Penetration Testining Knowledge Moreover This Company Test Your Network With All Type Attacks
| PowerPoint PPT presentation | free to download
Distributed Systems Architectures Lectures 17 and 18 Architectural Design - Establishing the overall structure of a software system Topics covered: System structuring ...
| PowerPoint PPT presentation | free to download
Cryptography and Network Security Chapter 16 Fifth Edition by William Stallings Lecture s by Lawrie Brown
| PowerPoint PPT presentation | free to view
802.11 Network Security (Hubert Yang) hwyang@iii.org.tw 802.11 Protocol Architecture 802.11 Access Process 802.11 ...
| PowerPoint PPT presentation | free to view
Network Architecture (R02) - L1 Jon Crowcroft, http://www.cl.cam.ac.uk/~jac22 http://www.cl.cam.ac.uk/teaching/1010/R02/
| PowerPoint PPT presentation | free to download
Security Issues in Distributed Sensor Networks Yi Sun Department of Computer Science and Electrical Engineering University of Maryland, Baltimore County
| PowerPoint PPT presentation | free to view
Networks What is a Network? a set of applications and/or switches connected by communication links many ``topologies'' possible: local area networks (LAN) versus wide ...
| PowerPoint PPT presentation | free to download
Technologies on Network Security Introduction to Technologies on Network Security 1001NS01 MI4 Wed. 3,4 (10:10-12:00 ...
| PowerPoint PPT presentation | free to download
This guides you about how you can become a network security engineer. To be brief, network security jobs include safeguarding the firm's computer networks and systems. They plan and implement security measures to protect the system from cyber attacks, hacking attacks, intrusion, infiltration, and natural disasters.
| PowerPoint PPT presentation | free to download
Golars Networks provides an innovative solution in networking while creating a new milestone and revolution in the industry. There are many valuable reasons why choose Golars Networking Training in United States and here follow a few facts:
| PowerPoint PPT presentation | free to download
It is not just the growing demand for network security professionals that makes it one of the most sought after job profiles, but the salary that they draw also contributes to make it a popular career option.
| PowerPoint PPT presentation | free to download
But allow architecture-aware applications to obtain enhanced ... Soda Hall Base Station DirecPC Basestation Internet Gateway Hughes DBS Basestation ...
| PowerPoint PPT presentation | free to download
WINS require a microwatt of power so it is very cheaper than other security system such as ... LWIM (Low power wireless ... Densely distributed sensor networks.
| PowerPoint PPT presentation | free to download
Chapter 10 Network Security. 5. Data Link Layer Encryption ... End-to-end security protects messages over the. entire path from source to destination. ...
| PowerPoint PPT presentation | free to view
* WTLS is not a single protocol but rather two layers of protocols, ... (in the OSI layering model ... 2004 Document Network Security Essentials Chapter 6 ...
| PowerPoint PPT presentation | free to view
Network Security Monitoring SearchSecurity.com webcast: 4 Dec 02 Richard Bejtlich, Foundstone richard.bejtlich@foundstone.com Robert Visscher, Ball Corporation
| PowerPoint PPT presentation | free to download
Security Target (ST): expresses security requirements for a specific TOE, e.g. by reference to a PP; basis for any evaluation. Evaluation Assurance Level ...
| PowerPoint PPT presentation | free to download
Traditional cameras see in only one direction at a time, ... Firetide / Mesh Wireless Network. CSC Major Distribution Network. Axis / High Performance Cameras ...
| PowerPoint PPT presentation | free to view
The boom of hybrid cloud, BYOD and private virtual clouds are upon us, and as the use of bandwidth-intensive enterprise applications spiking, many large players are spearheading the adoption of Software Defined Networks (SDN) for flexibility, availability and performance. After all the initial skepticism was put to rest, it is quite clear that SDN is here to stay. But the pressing issue seems to be the protection of its dynamic potentiality from compromise.
| PowerPoint PPT presentation | free to download
is an adaptable QoSrouting mechanism for ad hoc networks to ensure QoS even as network resources ... corresponds to applications that have strong delay constraints ...
| PowerPoint PPT presentation | free to download
Setting up a strong line of defense is pretty simple and hassle-free with optimum threat visibility. Though business owners invest in a motley range of security tools and implements, getting the maximum value out of these tools seems to be the real challenge. The best way to put underutilized resources to use and get the highest return on security investment is to assign deployment and security management to a seasoned security operations team. Managed Security Service Providers are the best bet whenever an organization faces the conundrum of miscalculated security strategies and insubstantial situational awareness.
| PowerPoint PPT presentation | free to download
Title: Adventures in Computer Security Author: John C. Mitchell Last modified by: John C Mitchell Created Date: 9/7/1997 8:51:32 PM Document presentation format
| PowerPoint PPT presentation | free to download
Title: Cryptography and Network Security 4/e Subject: Lecture Overheads Author: Dr Lawrie Brown Last modified by: Lawrie Brown Created Date: 3/28/2002 2:06:54 AM
| PowerPoint PPT presentation | free to view
Software Tool ready Dec 2006. InSAW. InSAW methodology. Profiling and Pre-Assessment ... Reference security-relevant architectures ...
| PowerPoint PPT presentation | free to view
LiSP: A Lightweight Security Protocol for Wireless Sensor Networks TAEJOON PARK and KANG G. SHIN The University of Michigan Presented by Abhijeet Mugade
| PowerPoint PPT presentation | free to download
How much security does a new configuration provide? ... What is ? Stands for Common Vulnerability Scoring System ... Blocking ftp traffic, p=0.0072 ...
| PowerPoint PPT presentation | free to download
... traffic and monitor network performance A protocol analyzer can be used to look at each packet in the communication process to see where the problem lies Network ...
| PowerPoint PPT presentation | free to view
Cyber Threats/Security and System Security of Power Sector Workshop on Crisis & Disaster Management of Power Sector P.K.Agarwal, AGM Power System Operation Corporation
| PowerPoint PPT presentation | free to view
Page 1. Architecture Design for Security Processing. Yunfei Wu. Computer Engineering ... Architectural comparison. Commercial Processors (1) Page 6 ...
| PowerPoint PPT presentation | free to view
Security Considerations for Low-Power Constrained Networks Ren Struik (Certicom Research) E-mail: rstruik@certicom.com Certicom Corp. is a wholly owned subsidiary ...
| PowerPoint PPT presentation | free to download
Cyber and Information Security from a Regulatory Viewpoint Cyber Security for Nuclear Newcomer States Dr. Farouk Eltawila Chief Scientist Federal Authority for ...
| PowerPoint PPT presentation | free to download
Enhancing the Security of Corporate Wi-Fi Networks Using DAIR Paramvir Bahl, Ranveer Chandra, Jitendra Padhye, Lenin Ravindranath, Manpreet Singh**, Alec Wolman,
| PowerPoint PPT presentation | free to download
A Security Framework with Trust Management for Sensor Networks Zhiying Yao, Daeyoung Kim, Insun Lee Information and Communication University (ICU)
| PowerPoint PPT presentation | free to view
A Framework for Addressing Security and Managing Business Risk The Information Security Program at Prudential Financial Ken Tyminski Vice President and Chief ...
| PowerPoint PPT presentation | free to download
BLUETOOTH SECURITY VS What is Bluetooth/Background? Technical Specifications Bluetooth Usage Security Concerns in Ad Hoc Networks Bluetooth Advantages
| PowerPoint PPT presentation | free to download
GENI: Global Environment for Network Innovations Jennifer Rexford Princeton University http://www.geni.net Outline Revisiting the Internet architecture Security ...
| PowerPoint PPT presentation | free to download
Big Market Research presents a fresh survey on the report "IT Security Market in China 2015-2019" Access The Full Report On : http://www.bigmarketresearch.com/it-security-in-china-2015-2019-market About IT Security: IT security protects system data and information over a network. It prevents unauthorized access of data and also prevents its modification. IT security deals with the measures taken to detect, monitor, report, and counter data threats. It includes security hardware, software, and services that focuses on security of important parameters, which includes email security, data protection, compliance, web security, data loss prevention, architecture, governance, security information and event management, and identity and access.
| PowerPoint PPT presentation | free to download
... (Common Object Request Broker Architecture) ... Disadvantages: Inefficiency due to ... Known uses Network Traffic Management Mobile Robot PAC Pattern ...
| PowerPoint PPT presentation | free to view
There are many threats to cloud security. The main treats arise from account hijacking, data breaches, inadequate cloud security architecture and strategy, insecure interfaces and APIs, insider threats, limited visibility with regard to cloud usage etc.
| PowerPoint PPT presentation | free to download
Network support service is an application running at the network application layer and above, that provides data storage, manipulation, presentation, communication or other capability which is often implemented using a client-server or peer-to-peer architecture based on application layer network protocols. Network support services include 24×7 network monitoring
| PowerPoint PPT presentation | free to download
Cyberoam delivers cost-effective and comprehensive network security solution, offering enterprise-class security appliances to Small & Medium Enterprises (SMEs). SMEs can function with assured Security-Connectivity-Productivity with Cyberoam features integrated over a single appliance, eliminating the need to invest in multiple network security solutions.
| PowerPoint PPT presentation | free to download
Network Security Lecture 8 Wireless LAN Security WLAN Security - Contents Wireless LAN 802.11 Technology Security History Vulnerabilities Demonstration Wireless LANs ...
| PowerPoint PPT presentation | free to download
Cross-layer Solution to Network Asymmetry ... WMNs lack efficient and scalable security solutions. Distributed network architecture ...
| PowerPoint PPT presentation | free to view
Wireless Mesh Networks Introduction Wireless mesh network architecture Why Wireless mesh network? When Wireless mesh networks? Routing background Problems in existing ...
| PowerPoint PPT presentation | free to download
VANET and FANET are next generation network and due to safety applications more attractions for end users in these networks. In this paper, we will provide the survey on security issues and challenges in the field of MANET, VANET and FANET. The successful implementation of these networks in real environment, it is require the network will be secure and end user can take benefit from their life safety applications.
| PowerPoint PPT presentation | free to download
North America deep learning neural networks (DDNs) market is an machine learning based technology that basically used for , decision making, diagnosis solving prediction, decision and problems based on a well-defined computational architecture. These technologies are widely adopted in the various applications such as computer security, speech recognition, image and video recognition to industrial fault detection, medical diagnostics and finance.
| PowerPoint PPT presentation | free to download