Prepending PowerPoint PPT Presentations
All Time
Recommended
... as-path prepend 47868 MikroTik bug: no-range check prepended 252 times Did not filter Cisco bug: Long AS paths AS path Prepending After: ...
| PowerPoint PPT presentation | free to download
Simple key-prepend/append have problems when used with a Merkle-Damg rd hash ... About as fast as key-prepend for a MD hash. Relies only on PRF quality of hash ...
| PowerPoint PPT presentation | free to download
Prepend 'as' to the name of the class of object returned. asSet (in Collection) ... Otherwise, prepend an adjective to most important superclass. - OrderedCollection ...
| PowerPoint PPT presentation | free to view
binary data format with direct access to recent values. Generic and Portable: ... no 'insert' nor 'prepend'! Possible Approach: ...
| PowerPoint PPT presentation | free to download
The Basics of BGP (Border Gateway Protocol) Routing and its Performance ... highest LOCAL-PREF ... setting the LOCAL-PREF attribute. prepending AS # to AS ...
| PowerPoint PPT presentation | free to download
head tail front back append(x) prepend(x) (s) # (x)in. take(n) drop(n) slice(offset, length) ... reverse(s.front).prepend(s.last) Indicates that T can be any ...
| PowerPoint PPT presentation | free to download
Another approach: host-based multihoming. 4. What is Multihoming? ... AS Path Length Hack: Prepending. Attempt to control inbound traffic ...
| PowerPoint PPT presentation | free to download
Prepend every global identifier with its package prefix. Prepend every source file name with its package prefix. Principles : Purpose of prefix is to : ...
| PowerPoint PPT presentation | free to download
Is it possible to minimize routing packets? Especially those interfering ... Minimize control packets by prepending protocol-level headers onto all data packets ...
| PowerPoint PPT presentation | free to download
Singly Linked Lists What is a singly-linked list? Why linked lists? Singly-linked lists vs. 1D-arrays Representation Space Analysis Creation, Append and Prepend
| PowerPoint PPT presentation | free to download
Once created, elements can be inserted into the list using either the append or prepend methods ... Insertion at the beginning (Prepend) Complexity is O(1) ...
| PowerPoint PPT presentation | free to view
Can now both append and prepend w/o changing final hash ... Possible to prepend each MP3 with a 128 bit multi-doppelganger set, without ...
| PowerPoint PPT presentation | free to view
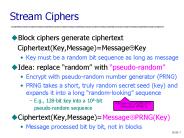
Encrypt with pseudo-random number generator (PRNG) ... To use RC4, usually prepend initialization vector (IV) to the key. IV can be random or a counter ...
| PowerPoint PPT presentation | free to download
Site Local (prepend FEC0::/10 plus subnet) Never route across the internet. Link Local (prepend FE80::/10 plus zeros) Never route away from interface. Addressing ...
| PowerPoint PPT presentation | free to view
take drop findFirst prepend. www.eschertech.com. Suggested answers 4 (cont'd) ... prepend(w) www.eschertech.com. Suggested answers to Exercise 5. function min2a ...
| PowerPoint PPT presentation | free to download
Protection of data from being accessed by unauthorized parties. Existing Tools/Technologies ... Encrypt the data and prepend any appropriate initialization vector (IV) ...
| PowerPoint PPT presentation | free to download
For each choice prepend it to the permutations of what's left after removing the ... For each choice we prepend it to the permutations of list of size three. ...
| PowerPoint PPT presentation | free to download
... specified ASM files or directories. ... ASMCMD prepends the current directory to the command argument ... ASM Directories, Files and File Aliases may be ...
| PowerPoint PPT presentation | free to view
3. Prepend s to Rps. 8. 6. 5. Rps. node. x1. x3. x2. s1. s3. s2. spine. 8. 1. 15. 3. 13 ... 3. Prepend s to Rps. 8. 7. Rps. 8. 1. 15. 3. 13. 11. 9. 7. 5. 2. 14 ...
| PowerPoint PPT presentation | free to download
At that time, had long history of formal analysis of crypto ... Whenever signature taken, prepend to signed data a tag saying what kind of signature it is ...
| PowerPoint PPT presentation | free to download
test productions in Jan 2002 at CERN (LSF) enjoyed nearly 100% ... just prepend an AFS path. a wrapper is created. insert commands to set up correct environment ...
| PowerPoint PPT presentation | free to download
Group prefix-routes by using community. Route received ... To ISP/IIG Customers, IIG advertises. Domestic routes (route from other ISP) with AS-path prepend ...
| PowerPoint PPT presentation | free to view
Given an ATWD or FADC waveform, determine arrival times of all photons which ... more uniform (11 bits all the time), prepend the 10-bit number of the next zero ...
| PowerPoint PPT presentation | free to download
Prepend URI to each tag or attribute name. http://www.princeton.edu:student ... Specify tag names, attribute names. Declare leaf types (contents) Built-in types ...
| PowerPoint PPT presentation | free to download
... specify pass-by-reference, prepend an. ampersand to the ... pass by reference, you can prepend an ampersand. to the actual parameter and still get pass-by ...
| PowerPoint PPT presentation | free to view
Designed as a small molcule visualization application. Focused on large ... Rotations, translations, rotamer library, append/prepend residue, mutate, etc. ...
| PowerPoint PPT presentation | free to view
Information scope is limited, additional readings required. Presentation ... Prepend FF onto 3A:9E9A. Append the result to the SNMA Prefix FF02::1:FF3A:9E9A ...
| PowerPoint PPT presentation | free to view
I'll talk about my daily operation/work for an example of ISP operation ... prepend. stop announcing routes. to certain party. change Local Preference ...
| PowerPoint PPT presentation | free to view
Prepending -1 to the 0-class vector Xi and negating it, gives ... Weights in a ff NN. wmn is the weight of the connection from the nth neuron to the mth neuron ...
| PowerPoint PPT presentation | free to view
P l Halvorsen, Thomas Plagemann, and Vera Goebel ... Prepend UDP and IP headers. Prepare pseudo header for. checksum, clear unknown fields ...
| PowerPoint PPT presentation | free to view
Ruli Manurung & Ade Azurat. Fasilkom UI - IKI20100. IKI 20100: Struktur Data & Algoritma ... insert next, prepend - O(1)? delete next, delete first - O(1)? find - O(n) ...
| PowerPoint PPT presentation | free to view
Information stored indefinitely in memory is known state information ... of the buffer among layers, and allow each layer to prepend another header ...
| PowerPoint PPT presentation | free to view
D. Simpler to prepend and append to files. E. Scott Summers is the X-men's Cyclops ... B. File created before a crash is missing ...
| PowerPoint PPT presentation | free to download
A search term may have a plus sign prepended, in which case it is a required term. ... tag author, in the fragment, increases the rank of this fragment. The ...
| PowerPoint PPT presentation | free to view
Key must be a random bit sequence as long as message. Idea: replace 'random' with 'pseudo-random' ... To use RC4, usually prepend initialization vector (IV) to the key ...
| PowerPoint PPT presentation | free to download
Advantage: allowing programmer to concentrate on more application ... a non-argument procedure with a name formed by prepending a tilde before the class name. ...
| PowerPoint PPT presentation | free to view
Through Java Native Interface (JNI), Java supports the ability to call native ... just pass in 'Hello' since Java will prepend 'lib' * and append the '.so' extension. ...
| PowerPoint PPT presentation | free to view
Check this site for up-to-date program information. This should be your primary ... When sending email to me, please prepend your subject line with SENG520 ...
| PowerPoint PPT presentation | free to view
Lookup table entries either NH IP or enet addr ... Must add code to map MI in filter to internal representation and prepend the VLAN tag. ...
| PowerPoint PPT presentation | free to download
Same best effort semantics as IP. No ack, no sequence, no flow control ... Compose pseudo header. Temporarily prepended to UDP message. Pad data to 16-bits multiple ...
| PowerPoint PPT presentation | free to view
By monitoring frequency and length of messages, even encrypted, nature of ... Prepend header. Figure 16.14 SSL Record Protocol Operation. Record Protocol Header ...
| PowerPoint PPT presentation | free to view
Want to save power without a performance hit. Dynamic ... For multi-node tests, prepend number of nodes. 4 2: 4 nodes, cores 0 and 1 active, 8 total cores ...
| PowerPoint PPT presentation | free to download
221 if (ipcperms(&msq- q_perm, msgflg)) 222 ret = -EACCES; 223 else { 224 int qid = msg_buildid(id, ... 339 * We prepend the allocation with the rcu struct, and ...
| PowerPoint PPT presentation | free to view
INFSCI 1052. Example: Use of searching for h2 within section of ID of main .prepend a class ... Using a transparent .png. http://www.sis.pitt.edu/~perkoski ...
| PowerPoint PPT presentation | free to view
The size of the pointer variable must be n bits where 2n bytes is the size ... which the pointer points prepend *, the indirection (or dereferencing) operator ...
| PowerPoint PPT presentation | free to view
Except members in a class are 'private' by default while members in a struct are ' ... If so, prepend T:: to the variable name and use the static data member ...
| PowerPoint PPT presentation | free to view
Peering Exchange Architectures Jeff Bartig University of Wisconsin WiscNet Engineering Overview OmniPOP - new CIC R&E exchange in Chicago Way too many hours of ...
| PowerPoint PPT presentation | free to download
'No matter how correct a mathematical theorem may appear to be, one ought never ... In class excercise. You design the program (pair up) ...
| PowerPoint PPT presentation | free to download
Julia Berg. Jason Codding. Alec Goebel. Kevin Goggins. Julie Hitchcock. Steven Miller. Rachel McManus ... Special method in a class invoked by the new operator ...
| PowerPoint PPT presentation | free to download
Peering (no transit, except for the down streams) To domestic ISPs (bi-literal or via IX) ... Mission impossible. What should be the solution? NOC. Lessons Learned (2) ...
| PowerPoint PPT presentation | free to download
Doubly Linked Lists Representation Space Analysis Creation and Insertion Traversal Deletion Representation Doubly Linked Lists : Space Analysis The space requirements ...
| PowerPoint PPT presentation | free to download
Those of you who have taken CSCI-4210, Operating Systems, should be ... fork(), exec(), waitpid(), etc. We will not be discussing these functions in this class ...
| PowerPoint PPT presentation | free to view
This is a view derived from the Route-Views archive, where each AS has a single colour. ... 14. IPv6 Unique ASNs. 15. IPv6 Aggregation Potential. 16. The Movie ...
| PowerPoint PPT presentation | free to download
Title: BGP Attributes and Policy Control Subject: ISP Workshops Asia Pacific Author: Philip Smith Description: BGP Attribute Presentation Master Last modified by
| PowerPoint PPT presentation | free to view
Singly Linked Lists Representation Space Analysis Creation and Insertion Traversal Search Deletion Representation We are using a representation in which a linked list ...
| PowerPoint PPT presentation | free to download
To learn and discuss network and routing policy. To help your networks expand into ... exchange points back to the same POP e.g. PacBell, PAIX (SJC), MAE-West ...
| PowerPoint PPT presentation | free to view