Threat Monitoring PowerPoint PPT Presentations
All Time
Recommended
FnCyber is a cyber security solution company that opts for functional methods of securing your system. FnCyber one of the best cyber security provider company offering wide range of cyber security solutions and protect clients from cyber threat. With the help of threat modelling and response consultant you can protect your data from cyber threats. Website: https://www.fncyber.com/threat-response-engineering
| PowerPoint PPT presentation | free to download
Brand Monitoring and Brand Protection Solution against Online Brand Abuse! Secure your online Brand and Business against Brand Abuse, Social media abuse.
| PowerPoint PPT presentation | free to download
U.S. Market for Patient Monitoring Equipment @ http://www.reportsnreports.com/reports/183478-us-market-for-patient-monitoring-equipment-2012.html The market for Patient Monitoring Devices and equipment includes multiparameter vital sign monitors, wireless ambulatory telemetry monitoring, telehealth monitoring, intracranial pressure devices, electromyography (EMG) devices, electroencephalography (EEG) monitors, cerebral oximetry devices, fetal and neonatal monitors, pulse oximetry devices, cardiac output monitoring devices and blood pressure monitors. Scope of Report: This report pertains to a forecast period of 10 years (2010 2020) for the US Market
| PowerPoint PPT presentation | free to download
Should be hard to be detected by the monitoring/detection systems. Code-based ... PN-code has a sharp auto-correlation peak (1 bit wide) and has very low cross ...
| PowerPoint PPT presentation | free to view
Other background information: land use, geology ... E.g. Soil erosion monitored in selected catchments. SESSION 2. Monitoring ...
| PowerPoint PPT presentation | free to view
THE INTEGRAL ASSESSMENT OF BIOTERRORISM THREAT. Episode III. ONE ... National Academy of Sciences of Ukraine. Konstantyn Atoyev. The threats of bioterrorism ...
| PowerPoint PPT presentation | free to view
The combination of protection and security services with CCTV monitoring has shown to be an effective technique to improve safety and defend against potential threats. When you choose HRS Security Services for your CCTV monitoring services, you can rely on unmatched experience, individualized solutions, and a dedication to excellence in every aspect of security services.
| PowerPoint PPT presentation | free to download
Threat hunters are security professionals who proactively search for threats and vulnerabilities in an organization's systems and networks. They use a variety of tools and techniques to identify potential threats, investigate suspicious activity, and respond to security incidents.
| PowerPoint PPT presentation | free to download
At Seceon, we believe that prevention is always better than cure. That's why our Online insider threat prevention services focus on proactively identifying and mitigating threats before they can cause any harm. Our solutions include employee training and education, risk assessments, access control, and continuous monitoring of user activity. We also provide regular reports and analysis to keep our clients informed of any potential threats and help them make informed decisions about their Cybersecurity strategies. Call Us: +1 (978)-923-0040
| PowerPoint PPT presentation | free to download
In today’s rapidly evolving world, where data is becoming more valuable than ever, specialized monitoring services are indispensable for businesses, governments, and organizations seeking to maintain an edge in their respective industries. Monitoring services are critical for tracking performance, compliance, and overall operational health. These services enable organizations to stay ahead of potential threats, mitigate risks, and ensure that their systems function smoothly and efficiently. Among the leading providers in this domain is RK Associates, a renowned agency specializing in a broad array of monitoring services tailored to meet the diverse needs of their clients.
| PowerPoint PPT presentation | free to download
With our Automated Threat Detection service, you can rest easy knowing that your business is constantly being monitored for any suspicious activity. Our system can detect a wide range of threats, including malware, phishing attacks, and other forms of cyberattacks, and can provide you with detailed reports and insights to help you make informed decisions about your cybersecurity strategy. Call Us: +1 (978)-923-0040
| PowerPoint PPT presentation | free to download
Threats to Information Security Part 2 Sanjay Goel University at Albany, SUNY
| PowerPoint PPT presentation | free to download
A video monitoring company is an essential tool in your arsenal. With the rise of crime rates and increasing security threats, it's crucial to have a reliable video monitoring system to deter intruders and keep an eye on your premises 24/7.
| PowerPoint PPT presentation | free to download
Monitoring the dark web involves specialized tools and techniques due to its hidden and often illegal nature. Dark web monitoring tools are designed to detect and track activities in the dark web, which may include the sale of stolen data, hacking tools, illegal services, and more. Here are some types of tools and approaches used for dark web monitoring
| PowerPoint PPT presentation | free to download
Threat management is a process that is used by cybersecurity analysts, incident responders and threat hunters to prevent cyberattacks, detect cyberthreats and respond to security incidents. Call us: +1 (978)-923-0040
| PowerPoint PPT presentation | free to download
Conducting a HIPAA Security Risk Assessment is not a one-time task; it requires constant monitoring and evaluation. Technology and security threats are constantly evolving, making it crucial for organizations to reassess their risk landscape regularly. Periodic assessments enable healthcare providers to adapt to new challenges, update security measures, and stay ahead of potential threats to patient data. This proactive approach strengthens data protection and demonstrates patient privacy and compliance commitment.
| PowerPoint PPT presentation | free to download
The global unified monitoring market is estimated to garner a significant revenue by the end of 2031 by growing at a CAGR of ~27% over the forecast period, i.e., 2022 – 2031.
| PowerPoint PPT presentation | free to download
Our team of Cybersecurity experts is highly experienced in identifying and mitigating insider threats before they can cause any damage. We use advanced technology and a range of techniques to monitor user behavior and identify any suspicious activities that could be indicative of an insider threat. We then work closely with our clients to develop and implement customized solutions that meet their unique needs and requirements. Call Us: +1 (978)-923-0040
| PowerPoint PPT presentation | free to download
Cyber Threat Simulation Training covers principles of cyber threats, advanced cyber warfare and threat simulation principles. Cyber Threat Simulation Training is splitted into multiple parts consisting of basic cyber security, advanced cyber security, principles of cyber threat and hands-on threat simulation exercises. Cyber Threat Simulation will train you and your team in the tactical, operational, and strategic level cyber threat modeling and simulation skills. Learn how your security team, threat hunting, incident response more efficient, accurate and effective. To learn more about this course, call us today at +1-972-665-9786 or visit our Tonex training website link. Cyber Threat Simulation Training and Courses https://www.tonex.com/training-courses/cyber-threat-simulation-training/
| PowerPoint PPT presentation | free to download
Threat Management Services
| PowerPoint PPT presentation | free to download
Future Market Insights has recently published a market research report on Global Transaction Monitoring market. The study presents a detailed analysis on the historical data, current and future market scenario for the Transaction Monitoring market.
| PowerPoint PPT presentation | free to download
Territorial Performance Monitoring (ESPON TPM project)
| PowerPoint PPT presentation | free to view
You might have heard of the threats that are built into machines, and the ones that are created by people to exploit loopholes in any given system. We're all aware of the malwares and viruses, the phishing sites, fake accounts, and everything digital threat that exists in this day and age. But let’s throw it back to the classics for a bit to tackle on the still existing grave threat, and probably the most dangerous of them all: insider threats. That's right; there isn't a code, a program, software or data cache that's more dangerous than a human mind.
| PowerPoint PPT presentation | free to download
Livestock Monitoring Market by Offering (Hardware, Software, and Services), Livestock Type (Cattle, Poultry, Swine, Equine), Application (Milk Harvesting, Feeding, Breeding, Behavior Monitoring & Control), Farm Type, Geography
| PowerPoint PPT presentation | free to download
Refrigeration Monitoring Market by Offering (Hardware, Software, and Service), Sensor (temperature, defrost, touch, liquid level, gas detector, contact, motion detector, pressure), Application, Industry, and Region
| PowerPoint PPT presentation | free to download
Here's iZOOlogic comes up with another awareness about malware threat which is necessary to know if you are a business owner of small, large or any scale and you are serious about brand protection and making online reputation strong. Read More: https://www.izoologic.com/
| PowerPoint PPT presentation | free to download
... sewer monitoring solution in Israel Installed in over 20 cities and towns across the country Backed by the Government Israel ... Downloadable charts ...
| PowerPoint PPT presentation | free to view
Ambicam offers Smart office monitoring systems which is come with built-in AI-powered technologies such as face recognition, motion, and object detection. Learn More: https://www.ambicam.in/office-monitoring.php
| PowerPoint PPT presentation | free to download
Threats Today. We've already covered most of the obvious ones. computer crime, privacy, software disasters and other impacts of ... watch Battlestar Galactica ...
| PowerPoint PPT presentation | free to view
This report studies the environmental monitoring market over the forecast period of 2016 to 2021. The market is expected to reach USD 19.56 Billion by 2021, growing at a CAGR of 7.7% during the forecast period.
| PowerPoint PPT presentation | free to download
Threat intelligence provides information across a wide range of sources to assist associations with safeguarding their resources by working with a designated network safety procedure. Call Us: +1 (978)-923-0040
| PowerPoint PPT presentation | free to download
Title: Wireless Network Monitoring Author: Sandeep Last modified by: Sandeep Created Date: 5/23/2003 4:17:35 PM Document presentation format: On-screen Show
| PowerPoint PPT presentation | free to download
Arrhythmia Monitoring Devices market
| PowerPoint PPT presentation | free to download
Arrhythmia Monitoring Devices industry
| PowerPoint PPT presentation | free to download
Arrhythmia Monitoring Devices market
| PowerPoint PPT presentation | free to download
... potential or growing threat from El Ni o, using a staged or graduated approach. ... A Stage 1 Alert or WATCH will be issued when the Pacific Ocean is becoming, or ...
| PowerPoint PPT presentation | free to view
In the fast-paced world of cybersecurity, staying ahead of threats is crucial.
| PowerPoint PPT presentation | free to download
Monitoring mammalian predators in the Whangamarino Wetland - early results Craig Gillies1 & Matthew Brady2 1Aquatic & Threats Unit Science & Technical Group
| PowerPoint PPT presentation | free to view
Domain 3 of the SSCP certification exam is Risk Identification, Monitoring, and Analysis. The Risk Identification, Monitoring, and Analysis domain comprise a 15% weightage of the SSCP certification. This domain is concerned with the systematic assessment techniques which are used to identify and monitor threats continuously.
| PowerPoint PPT presentation | free to download
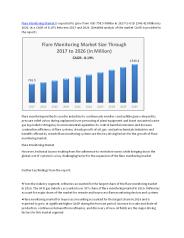
Flare Monitoring Market is expected to grow from USD 758.5 Million in 2017 to USD 1540.42 Million by 2026, at a CAGR of 8.19% between 2017 and 2026.
| PowerPoint PPT presentation | free to download
Future Market Insights has recently published a market research report on Global Machine Health Monitoring market. The study presents a detailed analysis on the historical data, current and future market scenario for the Machine Health Monitoring market.
| PowerPoint PPT presentation | free to download
Title: Data Mining in Cyber Threat Analysis Author: Aleksandar Lazarevic Last modified by: aleks Created Date: 1/18/1999 10:14:32 PM Document presentation format
| PowerPoint PPT presentation | free to download
Indicator Development Criteria used by FHM Program in U.S. ... Indonesia Establishing FHM plots to monitor sustainability and biodiversity of ...
| PowerPoint PPT presentation | free to view
Izoologic protects you against malware, Ransomware, and other advanced online threats that have made antivirus obsolete and ineffective with affordable cost. Contact us today @iZOOlogic.com to know how can you prevent your business.
| PowerPoint PPT presentation | free to download
Operational Standard on the Management of IT Security (MITS) ... Monitor compliance with MITS. IT Security Strategy development. 6. IM Security Programme ...
| PowerPoint PPT presentation | free to view
Comodo MDR Services helps to keep monitor and manage the organization date that being hacked by the cyber criminals attacks. Prevent the malware and threats and keep safe the enterprise data 100% secure now.
| PowerPoint PPT presentation | free to download
The Mobile Channel strategy needs to provide controls to manage and secure the Mobile App deployment. We have created a mobile protection and Phishing Cyber Threat solution. Contact us today @iZOOlogic.com to know how can you prevent your business.
| PowerPoint PPT presentation | free to download
Insulation Monitoring Devices Market by Response Time, Application (Power Utilities, Manufacturing and Production, Mining, Healthcare, Transportation), and Geography (North America, Europe, Asia Pacific, Rest of the World)
| PowerPoint PPT presentation | free to download
Aura emerges as the top pick for small business credit monitoring, offering robust online security for enhanced business protection. CreditQ's expert insight underscores Aura's excellence in safeguarding small businesses' financial health. Secure your business with the best business credit monitoring services recommended by CreditQ and prioritize your online security. Explore more @ https://creditq.in/post/how-business-credit-monitoring-services-empower-your-financial-health/
| PowerPoint PPT presentation | free to download
The American Monitor: Final Notes for 2001 about Post-Attack Public Opinion ... The American Monitor, December 28, 2001. 4. Interesting Observations about ...
| PowerPoint PPT presentation | free to view
Data security and data protection are an essential part of every organization. Data loss and/or data leaks can cause a major threat to a business. To know more visit us -
| PowerPoint PPT presentation | free to download
Safeguarding the IT environment has become an increasingly difficult challenge as cyber attackers have become more sophisticated and prolonged in their efforts to steal valuable information. How can Threat Intelligence help?
| PowerPoint PPT presentation | free to download
Arrhythmia Monitoring Devices market trends
| PowerPoint PPT presentation | free to download
Cyber Threat Hunting Services Provider - Sattrix Information Security narrated steps and techniques to use while doing real-time threat hunting. Check it now.
| PowerPoint PPT presentation | free to download
Network monitoring gives you the visibility you need to stay one step ahead of potential issues. By showing live network performance data in an easy-to-read interface, network monitoring software helps you identify outages that could cause bottlenecks.
| PowerPoint PPT presentation | free to download
Suma Soft has been providing Security Monitoring Service in USA for past 16+ years. Read more - http://bit.ly/2kwoj6Q
| PowerPoint PPT presentation | free to download