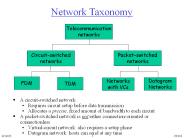
Connect To Avg Network PowerPoint PPT Presentations
All Time
Recommended
Using this, add more devices to Network, install applications on other PCs, phones & tablets and even invite your family members to join your network. Source: https://avgsupportaustralia.blogspot.com.au/2018/01/create-and-connect-to-avg-network.html
| PowerPoint PPT presentation | free to download
The Old Boy (and Girl) Network: Social Network Formation on University Campuses Adi Mayer and Steve Puller Texas A&M
| PowerPoint PPT presentation | free to view
Trojan horse. Claims to be something desirable, but hides something harmful. Network Virus ... Environments with huge data quantities requiring quick availability ...
| PowerPoint PPT presentation | free to download
Data storage plays an essential role in today's fast-growing data-intensive network services. ... Amortize request/transfer cost. Client uses a disk cache ...
| PowerPoint PPT presentation | free to view
Title: NetShield: Massive Semantics-Based Vulnerability Signature Matching for High-Speed Networks Author: ZHICHUN Last modified by: Yan Created Date
| PowerPoint PPT presentation | free to download
100 KB/hr, 25 GB/lifetime. Hear (Speech @ 10KB/s) 40 MB/hr, 10 TB/lifetime. See (TV @ .5 MB/s) 2 GB/hr, 500TB/lifetime. 1K=210. 1M=220 ...
| PowerPoint PPT presentation | free to view
... and servers capacity constraints Self-organize replica into a scalable application-level multicast for disseminating ... 3084 paths w/ 5% improvment: ...
| PowerPoint PPT presentation | free to download
Dealing with fault tolerance / load balancing. Unique service out of the data path ... with different delays of arrival of 0 second (300), 1 second (301) and 2 seconds ...
| PowerPoint PPT presentation | free to download
SENSOR NETWORKS ARCHITECTURE MICA Motes BWN Lab @ GaTech SENSOR NETWORKS FEATURES APPLICATIONS: Military, Environmental, Health, Home, Space Exploration ...
| PowerPoint PPT presentation | free to view
SENSOR NETWORKS ARCHITECTURE MICA Motes BWN Lab @ GaTech SENSOR NETWORKS FEATURES APPLICATIONS: Military, Environmental, Health, Home, Space Exploration ...
| PowerPoint PPT presentation | free to view
UNIT 3 NETWORK LAYER Network Layer It is responsible for end to end (source to destination) packet delivery, whereas the data link layer is responsible for node to ...
| PowerPoint PPT presentation | free to download
Computer Networks Network Layer
| PowerPoint PPT presentation | free to download
Delay Tolerant Networks * * Gateways are entry points to each region. They are points of translation as well as points to enforce policy and control.
| PowerPoint PPT presentation | free to download
Lecture 16: On-Chip Networks Today: on-chip networks background * * * * * * * * * * * * * * Interconnection Networks Recall: fully connected network, arrays/rings ...
| PowerPoint PPT presentation | free to download
Lecture 14: Interconnection Networks Topics: dimension vs. arity, deadlock University of Utah Interconnection Networks Recall: fully connected network, arrays/rings ...
| PowerPoint PPT presentation | free to download
SMTP, POP3, IMAP. 2.5 DNS. 2.6 P2P file sharing. 2.7 Socket programming with TCP ... SMTP / POP3 / IMAP. DNS. programming network applications. socket API. 4/12 ...
| PowerPoint PPT presentation | free to download
all milestones in resolution of problem create a new ticket entry with reference ... Ticket information log : toppingb@facesofdeath.ns.itd.umich.edu said ...
| PowerPoint PPT presentation | free to download
Slides modified from Alberto Leon-Garcia and Indra Widjaja
| PowerPoint PPT presentation | free to download
Sensor Networks & Applications Partly based on the book Wireless Sensor Networks by Zhao and Guibas Constraints and Challenges Limited hardware: Storage Processing ...
| PowerPoint PPT presentation | free to download
Lecture 14: Interconnection Networks Topics: dimension vs. arity, deadlock University of Utah Interconnection Networks Recall: fully connected network, arrays/rings ...
| PowerPoint PPT presentation | free to download
... Packets Pings Host Loss% Snt Last Avg Best Wrst StDev 1. 10.252.102.1 0.0% 6 1.4 2.4 1.4 3.0 0.6 Layer Transport Netstat Tool ini dapat mencetak ...
| PowerPoint PPT presentation | free to download
... * Interconnection Networks Recall: fully connected network, arrays/rings, meshes/tori, trees, butterflies, hypercubes Consider a k-ary d-cube: ...
| PowerPoint PPT presentation | free to download
Wireless Sensor Networks the next IT Revolution
| PowerPoint PPT presentation | free to download
Title: Chapter 7 Lecture Presentation Subject: Packet-Switching Networks Author: Leon-Garcia/Widjaja Last modified by: Stephen Asa Baber Created Date
| PowerPoint PPT presentation | free to download
1. INTRODUCTION SENSOR NETWORKS ARCHITECTURE Key technologies that enable sensor networks: Micro electro-mechanical systems (MEMS) Wireless communications Digital ...
| PowerPoint PPT presentation | free to view
Wireless Sensor Networks Parallel and Distributed Processing Meets the Real World
| PowerPoint PPT presentation | free to download
Impact on devices (measurements and measuring) ... (to inform the source that it's pointless to keep sending more packets at the present time) ...
| PowerPoint PPT presentation | free to download
Lecture 23: Interconnection Networks Topics: Router microarchitecture, topologies Final exam next Tuesday: same rules as the first midterm Next semester: CS/EE 7810 ...
| PowerPoint PPT presentation | free to download
Oct 1988: Ordered first Cisco campus router. May 1989: Solve DECnet problem via TGV Multinet license. Aug ... Jan 1999: AMP net monitor deployed for NLANR/MOA ...
| PowerPoint PPT presentation | free to download
Countries monitored. Contain 78% of world population. 99% of online users of Internet ... nlanr.net/training/presentations/tcp-tutorial.ppt. www-didc.lbl.gov ...
| PowerPoint PPT presentation | free to download
Gather temperature, humidity, light from a redwood tree ... need general programming: nodes in redwood trees don't need to locate snipers in Sonoma. ...
| PowerPoint PPT presentation | free to view
Network Management And Debugging WeeSan Lee http://www.cs.ucr.edu/~weesan/cs183/ Roadmap Interface Configuration Route Configuration Network ...
| PowerPoint PPT presentation | free to download
Lecture 23: Interconnection Networks Topics: Router microarchitecture, topologies *
| PowerPoint PPT presentation | free to download
Database Middleware for Sensor Networks
| PowerPoint PPT presentation | free to download
School of Electrical and Computer Engineering. Georgia ... Motes. BWN ... Rene Mote. Dot Mote. weC Mote. Mica node. 7. IFA'2004. SENSOR NETWORKS ...
| PowerPoint PPT presentation | free to view
Title: PowerPoint Presentation Author: Rajeev Balasubramonian Last modified by: RB Created Date: 9/20/2002 6:19:18 PM Document presentation format
| PowerPoint PPT presentation | free to download
... time slot, each node computes an MD5 hash, that computes its priority ... Each node computes a schedule of slots (and intended receivers) in which will transmit ...
| PowerPoint PPT presentation | free to view
Upcoming events in CS 252. 23-Mar to 27-Mar Spring Break. Wed 8-Apr Multiprocessors ... If Ethernet, broken into 1500B packets with headers, trailers ...
| PowerPoint PPT presentation | free to download
Along with distance, you need to know exactly where the satellites are in space. High orbits and careful monitoring are the secret ...
| PowerPoint PPT presentation | free to view
IT351: Mobile & Wireless Computing Wireless Personal Area Networks (WPAN) Part-2: IEEE802.15 Bluetooth Objectives: To introduce Ad Hoc networking and discuss its ...
| PowerPoint PPT presentation | free to download
... (ttl 128, id 6743, len 40) 0x0000 4500 0028 1a57 4000 8006 6e23 ac10 0d03 E..(.W@...n#.... 0x0010 ac10 0d32 0467 0015 00a1 7162 1689 241b ...2.g ...
| PowerPoint PPT presentation | free to view
Middleware The fascinating world between network and application Erik Ombelets EAI, KBC ICT
| PowerPoint PPT presentation | free to download
BERT. 2006-04-03. Network Management Tools & Applications. 4. Status Monitoring Tools ... Used to assign/read an address to/of an interface. Option -a is to ...
| PowerPoint PPT presentation | free to view
Residential Access Network Evolution
| PowerPoint PPT presentation | free to download
Most Large Scale Sparse' Networks are found to be of the small world type e.g. ... Actors' Database ( 150,000 films, 300,000 combined actors) (www.us.imdb.com) ...
| PowerPoint PPT presentation | free to download
Resilient Overlay Networks. David Anderson, Hari Balakrishnan, Frank Kaashoek and ... A. Collins, E. Hoffman, J. Snell, A. Vahdat, G. Voelker, and J. Zahorjan, IEEE ...
| PowerPoint PPT presentation | free to download
nsrc@summer workshop. eugene, oregon. Network Performance Definitions & Analysis ... Very little free memory. Lots of swap activity (swap in, swap out)? Slow I/O ...
| PowerPoint PPT presentation | free to download
Automatically Building Special Purpose Search Engines with ...
| PowerPoint PPT presentation | free to download
Automatically Building Special Purpose Search Engines with ...
| PowerPoint PPT presentation | free to download
... sort packets according to completion time in ideal system Packetized GPS/WFQ Compute ... no protection Aggregation into ... Transmission line User ...
| PowerPoint PPT presentation | free to download
Automatically Building Special Purpose Search Engines with ...
| PowerPoint PPT presentation | free to download
Critical Infrastructure Protection In the Transportation Network A Mathematical Model and Methodology for Determining and Analyzing The k-Critical Links of a Highway ...
| PowerPoint PPT presentation | free to view
Small-world Overlay P2P Network John C.S. Lui Outline Describe our motivations on small world overlay P2P network. Introduce the background information of P2P network ...
| PowerPoint PPT presentation | free to download
J. Broch, D. Maltz, D. Johnson, Y. Hu, J. Jetcheva, A Performance Comparison of ... J. Broch, D. A. Maltz, D. B. Johnson, Y. C. Hu, and J. Jetcheva. In Proc. ...
| PowerPoint PPT presentation | free to view
TCP Slow Start, Congestion, Avoidance, Fast Retransmit, and ... detect incipient congestion. decide which connections to notify of congestion at the gateway ...
| PowerPoint PPT presentation | free to view
Contents MANET overview Properties of MANET MANET applications Routing and various routing algorithms Unicast routing protocols for MANET Broadcasting protocols for ...
| PowerPoint PPT presentation | free to download