Overwriting PowerPoint PPT Presentations
All Time
Recommended
Writing of covered calls is an extremely important strategy that should be ... Precipitous declines can be disastrous to put writers, as some people discovered ...
| PowerPoint PPT presentation | free to view
More often for mission-critical applications. Multiple backup copies are saved ... Overwritten. Second set of incrementals overwrites the first ...
| PowerPoint PPT presentation | free to download
as with rm command, -i option prompts you to overwrite an existing file ... i option prompts you if you are about to overwrite an existing file ...
| PowerPoint PPT presentation | free to download
... some data which determines the flow of the program, which can be overwritten. ... Can be overwritten similarly to GOT entries ...
| PowerPoint PPT presentation | free to view
If a label (m = a) is overwritten by the label (m = *) in the current set of ... Suppose m = a was first instance of overwritten by a * and let nj = bj be an ...
| PowerPoint PPT presentation | free to view
also known as visible-surface determination' Occluded object ... z-buffer: z2 overwritten by z1. frame-buffer: colour for pixel of S2 overwritten by pixel of S1 ...
| PowerPoint PPT presentation | free to view
However, to enter a new name, simply overwrite the current default. ... Values are changed by clicking the appropriate cell(s) and overwriting with new value. ...
| PowerPoint PPT presentation | free to view
As we did not overwrite the existing OS2008 operating system (which runs on a ... put on the C3200 by completely overwriting the existing operating system with a ...
| PowerPoint PPT presentation | free to view
User ID. Group ID. Process Control Block (PCB) Context Switch (or Process Switch) ... Accomplished by overwriting process imaged of caller with that of called. ...
| PowerPoint PPT presentation | free to download
Definitions in later files overwrite previous definitions. Order of files: Global config file ... to with the CONDOR_CONFIG environment variable, /etc/condor ...
| PowerPoint PPT presentation | free to download
Widely available and commonly used. Real-time, interactive nature ... Insertion of New Slices. Removal of Old Slices. Overwrite Existing Slices ...
| PowerPoint PPT presentation | free to view
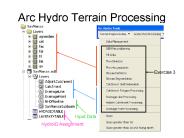
DrainageLine HydroID = 655 to 774 (120 Drainage Lines) ... delete it or overwrite it, HydroID's are all assigned new. HydroID - DrainID ...
| PowerPoint PPT presentation | free to download
Real Unix computers ... the output of one command is used as input for the next Link ... file_name (overwrite) * more file_name Display first n lines of ...
| PowerPoint PPT presentation | free to download
UserAuth using htaccess Apache Auth Basic NTLM Nogetiate Basic Edit your ... it caused can be overwrite the old password Create .htaccess Create new .htaccess file ...
| PowerPoint PPT presentation | free to download
Many event listener interfaces, such as MouseListener, MouseMotionListener, ... Your event handler only OVERWRITE the methods you need. MouseAdapter ...
| PowerPoint PPT presentation | free to download
Applications for arbitrary memory overwrite exploitation demos ... DCOM (seems to be the inflection point), Messenger, MSMQ, Script Engine ...
| PowerPoint PPT presentation | free to view
An architecture for distributed file systems based on shared storage. ... Overwrite/Append Ratio: pre-fetching and space allocation. Work Load Management ...
| PowerPoint PPT presentation | free to download
update memory only on eviction. Caltech CS184b Winter2001 -- DeHon. 34. Write Policy ... eviction trivial (just overwrite) every write is slow (main memory time) ...
| PowerPoint PPT presentation | free to download
directory -v verbose -b makes backups -f force renaming -i prompts to overwrite. Examples: ... files recursively -R copies directories recursively. Examples: ...
| PowerPoint PPT presentation | free to view
Accessories. dataTaker DT50/500/600 ... (overwrite) data storage modes ... Data storage is approx 50,000 readings per Mbyte. Stack and circular ...
| PowerPoint PPT presentation | free to view
maketest using filename.do, replace. Options: using: specifies file to write ... replace: overwrite existing data file. clear: clear current data in memory ...
| PowerPoint PPT presentation | free to download
... files, in order - definitions in later files overwrites previous definitions ... Host names, domain names. IP addresses, subnets. Wildcards ...
| PowerPoint PPT presentation | free to view
Reconfigure the settings as directed. Manually refresh the Group Policy settings ... Reconfigure the Security log size and overwrite properties as directed ...
| PowerPoint PPT presentation | free to view
... and thus protects user from accidental deletes, overwrites and viruses. ... mirror image of the source by deleting. files not present on the system and ...
| PowerPoint PPT presentation | free to view
Science, Technology, and Glob. Grant Overview ... Buffer Overflow: When data is written outside the bounds of ... overwrite security-sensitive data in memory ...
| PowerPoint PPT presentation | free to view
In-memory data is converted to ASCII characters upon output. ... Can freely overwrite/edit existing record w/o disturbing others (fixed length) ...
| PowerPoint PPT presentation | free to view
BASIC TYPES OF LEARNING. A THEORY OF ADULT LEARNING. INSTRUMENTAL ... Overwriting model erasing obsolete knowledge in favour of more serviceable knowledge ...
| PowerPoint PPT presentation | free to view
In the Construct Molecule screen, enter name 'Tutorial1' ... Click the Construct button and select Tutorial as the subset, then click the Overwrite button. ...
| PowerPoint PPT presentation | free to view
Designed inputs can execute malicious codes. Overwrite a local variable ... Nintendo released Wii Menu update 3.3 to prevent this, ...
| PowerPoint PPT presentation | free to download
Associates a list of objects and rights with each subject (dual to ... Propagation required overwriting software at levels A and T by an election official. ...
| PowerPoint PPT presentation | free to download
Overwriting bar-coded information with incorrect answer sheet bubbling ... Recording exam rate incorrectly (MM vice MMN entered on answer sheet) Errors can lead to: ...
| PowerPoint PPT presentation | free to view
A transaction is any one execution of a user program in a DBMS ... WW Conflict - overwriting uncommitted data (lost update): 9. Transaction Schedules ...
| PowerPoint PPT presentation | free to view
Operators A may represent, for example, numerical derivatives ... solution with a t step in time, overwriting u. Unew is only an intermediate stage. ...
| PowerPoint PPT presentation | free to view
how we organize, store, and retrieve information. 6. IS Development ... in memory, must ensure one process doesn't overwrite anther's program or data ...
| PowerPoint PPT presentation | free to view
Warning Devices and Advanced Electronics for specialty vehicles ... 15 seconds after rollover - Throttle position. constant overwriting - Steering & brake input ...
| PowerPoint PPT presentation | free to download
Extract from system configuration utility. Where to extract to and why ... Use extract.Exe. Can extract directly to destination and overwrite the protected file ' ...
| PowerPoint PPT presentation | free to view
Time functions. September 6, 2005. CSCE 510 Systems Programming. 2. CSCE 510 Fall 2005 ... setenv-does not remove old entry if overwrite = 0 ...
| PowerPoint PPT presentation | free to view
First in the list of environment-friendly Hard Drive Shredding is to overwriting the drive. "Circle wiping" programming is utilized to supplant put away information with an example of negligible characters. Continue reading: www.stselectronicrecyclinginc.com
| PowerPoint PPT presentation | free to download
There are no subfolders in your either your workarea or your attachments ... name for different documents, and thereby prevent the overwriting of your files. ...
| PowerPoint PPT presentation | free to view
Files need to be opened before use. Associate a 'file handler' to each file. Modes: read, write, or append ... a : append. Warning: The 'w' mode overwrites the ...
| PowerPoint PPT presentation | free to view
Condor. Distributed batch processing. Large-scale numerical ... restart() invoked by Condor code. Instead of user's main() Overwrites its own data segment ...
| PowerPoint PPT presentation | free to view
Degree 0: T doesn't overwrite dirty data of other transactions ... ( So it's a good idea to periodically flush dirty pages to disk! ...
| PowerPoint PPT presentation | free to download
The foundation skill areas are required from Kindergarten to Grade 12. They are ... ( Helps to keep organized and to avoid overwriting files.) Helpful Hints ...
| PowerPoint PPT presentation | free to view
Freeing only part of a data structure. typedef LISTP { int val; LISTP *val; foo ... can also check each individual reference at runtime. bad pointers. overwriting ...
| PowerPoint PPT presentation | free to download
PHP stands for PHP: Hypertext Preprocessor. PHP is a server-side scripting language, like ASP. PHP scripts are executed ... Truncates the file (overwriting it) ...
| PowerPoint PPT presentation | free to view
The Lost Update Problem. ... memory may be lost. A transaction or system ... theft, sabotage, overwriting disks or tapes by mistake, and mounting of a wrong ...
| PowerPoint PPT presentation | free to view
Cannot overwrite the return address (as on the stack), but can ... Embed random 'canaries' in stack frames and verify their integrity prior to function return ...
| PowerPoint PPT presentation | free to download
Each entry includes name, size, and location of object. ... overridden by a strong symbol of the same name. ... Evil! Writes to x in p2 will overwrite y! Nasty! ...
| PowerPoint PPT presentation | free to download
Insert repeaters between L and F2 = one signal may not overwrite the other ... Flip-flop latch based wire pipelining is applied in a flip-flop based circuit design ...
| PowerPoint PPT presentation | free to view
( after they made a big deal that there were no buffer overflow problems in their code) ... idea is to overflow a buffer so that it overwrites the return ...
| PowerPoint PPT presentation | free to view
Remapping is modification or replacement in default software of ECU. Car remapping is done to optimize the vehicle overall performance. When a car is remapped the modified software is plugged into the serial port of car that overwrites the map of the engine.
| PowerPoint PPT presentation | free to download
Having an arrangement of the .NET Frameworks that works accurately is essential for all Windows clients and designers are no special case. Through the course of development, it is anything but difficult to unintentionally overwrite required records.
| PowerPoint PPT presentation | free to download
A buffer overflow, or buffer overrun, is an ... The result is that the extra data overwrites adjacent memory locations. ... Spraying injected attack code ...
| PowerPoint PPT presentation | free to view
What is Castor? There are two modes for ... Role of Binding files in Castor ... The default behavior of Castor is to overwrite the previously generated Class ...
| PowerPoint PPT presentation | free to view
Jun 15 15:49:42 localhost kernel: About to overwrite chdir at address c0159050 ... Jun 15 16:03:12 localhost kernel: GKM: Please take appropriate action and reboot ...
| PowerPoint PPT presentation | free to download
Writing and Reading a text file. Using the format command. Opening a Textfile ... APPEND; Starts writing at the end of an existing file instead of overwriting the ...
| PowerPoint PPT presentation | free to download

















![CS184b: Computer Architecture [Single Threaded Architecture: abstractions, quantification, and optimizations] PowerPoint PPT Presentation](https://s3.amazonaws.com/images.powershow.com/A1256655833OAftl.th0.jpg)





































