Interdomain Routing - PowerPoint PPT Presentation
1 / 29
Title:
Interdomain Routing
Description:
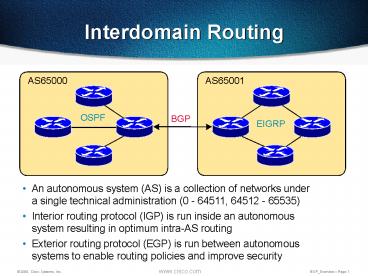
An autonomous system (AS) is a collection of networks under. a single technical administration (0 ... BGP uses TCP for reliable transport - CPU intensive ... – PowerPoint PPT presentation
Number of Views:45
Avg rating:3.0/5.0
Title: Interdomain Routing
1
Interdomain Routing
AS65001
AS65000
- An autonomous system (AS) is a collection of
networks under a single technical administration
(0 - 64511, 64512 - 65535)
2
Interdomain Routing Goals
- Scalability
- Internet has over 80,000 routes and is still
growing - Secure routing information exchange
- Routers from another autonomous system cannot be
trusted - Tight filters are required, authentication is
desirable - Routing policies support
- Routing between autonomous systems might not
always follow the optimum path
3
Routing Policies - Case Study
2 Mbps
Company X (AS 20)
Service Provider
(AS 10)
2 Mbps
64 kbps
2 Mbps
Company B (AS 2)
Company A (AS 1)
- Q Assuming standard IGP route selection rules,
how will the traffic between AS1 and AS20 flow? - Q Will AS 2 allow this traffic?
- Q How would you solve this problem with OSPF or
EIGRP?
4
BGP Characteristics
- Distance-vector protocol with enhancements
- Reliable updates
- Triggered updates only
- Rich metrics (called path attributes)
- Designed to scale to huge internetworks
5
Reliable Updates
- Uses TCP as transport protocol
- No periodic updates
- Periodic keepalives to verify TCP connectivity
- Triggered updates are batched and rate-limited
(every 5 seconds for internal peer, every 30
seconds for external peer)
6
Common BGP Usages
- Customer connected to one Internet Service
Provider (ISP) - Customer connected to several Service Providers
- Service Provider networks (transit autonomous
systems) - Service providers exchanging traffic at an
exchange point (CIX, GIX, NAP ) - Network cores of large enterprise customers
7
Single-homed Customers
- Large customer or small ISP connecting to the
Internet
Internet
Customer or small
Service Provider
Service Provider
BGP
8
Customer Connected to One ISPUsage Guidelines
- Use BGP between the customer and the Service
Provider - Customers multi-homed to the same Service
Provider - Customer that needs dynamic routing protocol with
the Service Provider to detect failures - Hint Use private AS number for these customers
- Smaller ISPs that need to originate their routes
in the Internet - Use static routes in all other cases
- Static routes are always simpler than BGP
9
Multi-homed Customers
- Customer connecting to several service-providers
(multi-homed customer)
Internet
Service Provider 1
Multi-homed
BGP
Customer
Service Provider 2
BGP
10
Multi-homed Customer Usage Guidelines
- BGP is almost mandatory for multi-homed customers
- Multi-homed customers have to use public AS
numbers - Multi-homed customers should use
provider-independent address space
11
Transit and Non-transit AS
12
Transit Autonomous System
- Using BGP to exchange routes is mandatory for
transit autonomous systems (provider networks
carrying customer traffic)
Internet
Multi-homed
Another Service
Customer
Provider
BGP
BGP
BGP
Simple Customer
Static
Routing
Service Provider
(Transit AS)
13
BGP Limitations
- RFC 1771 BGP does not enable one AS to send
traffic to neighbor AS intending that the traffic
take a different route from that taken by traffic
originating in the neighbor AS - BGP and associated tools cannot express all
routing policies - You cannot influence the routing policies of
downstream autonomous systems - BGP-enabled routers make decisions based on the
destination IP - Source IP does not affect the decision
14
Protocol Development Considerations
- BGP was designed to perform well in
- Interdomain Routing application
- Huge internetworks with large routing tables
- Environments that require complex routing
policies - Some design tradeoffs that were made
- BGP uses TCP for reliable transport - CPU
intensive - Scalability is the top priority - slower
convergence
15
BGP does not Auto-discover Neighbors
- BGP neighbors are not discovered - they must be
configured manually - Configuration must be done on both sides of the
connection - Both routers will attempt to connect to the other
with a TCP session on port number 179 - Only one session will remain if both connection
attempts succeed - Source IP address of incoming connection attempts
is verified against a list of configured neighbors
16
Small BGP Network Used in Following Examples
AS 21
21.0.0.0/8
2.3.4.5
AS 123
2.3.4.6
Rtr-B
1.0.0.0/8
3.4.5.7
Rtr-A
3.4.5.6
AS 37
Rtr-C
37.0.0.0/8
17
BGP Neighbors - Idle State
- Initially all BGP sessions to the neighbors are
idle
Rtr-Ashow ip bgp sumBGP table version is 1,
main routing table version 1 Neighbor V
AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down
State 2.3.4.5 4 21 0 0
0 0 0 never Idle 3.4.5.6 4 37
0 0 0 0 0 never Idle
18
Establishing Session
- TCP session is established when the neighbor
becomes reachable - BGP Open messages are exchanged
Rtr-Adebug ip tcp transactions Rtr-Adebug ip
bgp events 00617 BGP 2.3.4.5 went from Idle
to Active 00622 TCB0012A910 created 00622
TCB0012A910 setting property 0 12A8B4 00622
TCB0012A910 bound to 2.3.4.6.11003 00622 TCP
sending SYN, seq 3142900499, ack 0 00622 TCP0
Connection to 2.3.4.5179, advertising MSS
1460 00622 TCP0 state was CLOSED -gt SYNSENT
11003 -gt 2.3.4.5(179) 00622 TCP0 state was
SYNSENT -gt ESTAB 11003 -gt 2.3.4.5(179) 00622
TCP0 Connection to 2.3.4.5179, received MSS
1460, MSS is 1460 00622 TCB0012A910 connected
to 2.3.4.5.179 00622 BGP 2.3.4.5 went from
Active to OpenSent 00622 BGP 2.3.4.5 went
from OpenSent to OpenConfirm 00622 BGP
2.3.4.5 went from OpenConfirm to Established
19
BGP Open
- The BGP Open message contains
- BGP Version number
- My Autonomous System number
- Hold Time
- BGP Router Identifier
- Optional Parameters
20
BGP Keepalives
- TCP-based BGP session does not provide any means
of verifying BGP presence - Except when sending BGP traffic
- BGP needs an additional mechanism
- Keepalive BGP messages provide verification of
neighbor existence - Keepalive messages sent every 60 seconds
21
BGP Keepalives (2)
- Keepalive interval value is not communicated in
the BGP Open message - Keepalive value is selected as
- Configured value, if local holdtime is used
- Configured value, if holdtime of neighbor is used
and keepalive lt (holdtime/3) - Smaller integer in relation to (holdtime/3), if
keepalive gt (holdtime/3) and holdtime of neighbor
is used.
22
BGP Neighbors - Steady State
- All neighbors shall be up (no state info)
- Rtr-Ashow ip bgp sum
- BGP table version is 10, main routing table
version 10 - 3 network entries (3/6 paths) using 516 bytes of
memory - 3 BGP path attribute entries using 284 bytes of
memory - 0 BGP route-map cache entries using 0 bytes of
memory - 0 BGP filter-list cache entries using 0 bytes of
memory - Neighbor V AS MsgRcvd MsgSent TblVer InQ
OutQ Up/Down State/PfxRcvd - 2.3.4.5 4 21 17 22 10 0
0 00147 27 - 3.4.5.6 4 37 11 17 10 0
0 00707 35
23
MD5 Authentication
- BGP Peers may optionally use MD5 TCP
authentication using shared secret - Both routers must be configured with the same
password (MD5 shared secret) - Each TCP segment is verified
24
FSM State Transitions Diagram BGP Link Setup
25
FSM State Transitions Diagram BGP Link Setup
26
BGP Operation
When two routers establish a TCP-enabled BGP
connection between each other, they are called
neighbors or peers Each router running BGP is
called a BGP speaker
27
Initial Exchange
- When BGP neighbors first establish a connection,
they exchange all candidate BGP routes - After initial exchange, incremental updates are
sent as network information changes
28
Withdrawn Routes
- The information for network reachability can
change such as when a route becomes unreachable
or a better path becomes available - BGP informs its neighbors of this by withdrawing
the invalid routes and injecting the new routing
information - Withdrawn routes are part of the update message
29
Summary
- With interior routing protocols, adjacent routers
are usually discovered through a dedicated hello
protocol. In BGP, neighbors must be manually
configured to increase routing protocol security. - BGP neighbors, once configured, establish a TCP
session and exchange the BGP Open message, which
contains the parameters each BGP router proposes
to use. - BGP keepalives are used by the router to provide
verification of the existence of a configured BGP
neighbor. - MD5 authentication can be configured on a BGP
session to help prevent spoofing, denial of
service attacks, or man-in-the-middle attacks.