Application PowerPoint PPT Presentation
1 / 20
Title: Application
1
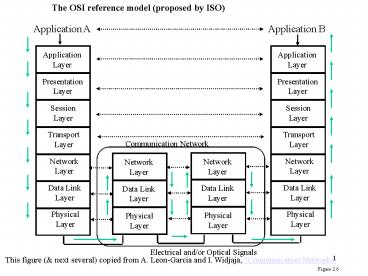
The OSI reference model (proposed by ISO)
Application A
Application B
Application Layer
Application Layer
Presentation Layer
Presentation Layer
Session Layer
Session Layer
Transport Layer
Transport Layer
Communication Network
Network Layer
Network Layer
Network Layer
Network Layer
Data Link Layer
Data Link Layer
Data Link Layer
Data Link Layer
Physical Layer
Physical Layer
Physical Layer
Physical Layer
Electrical and/or Optical Signals
This figure ( next several) copied from A.
Leon-Garcia and I. Widjaja, "Communication
Networks
Figure 2.6
2
TCP/IP network architecture
Application Layer
Application Layer
Transport Layer
Transport Layer
Internet Layer
Internet Layer
Network Interface
Network Interface
(b)
(a)
TCP/IP model does not require strict layering
Figure 2.10
3
RTP
HTTP
SMTP
DNS
App.
Transport
TCP
UDP
TCP/UDP Provides a network independent platform
IP provides independence from
underlying networks
Internet
(e.g., Ethernet driver)
(e.g., PPP driver)
TCP/IP protocol graph
Figure 2.12
4
Internet security protocols at layers
SSH, SFTP, PGP, PEM, HTTPS
SSL/TLS, SSH
IPSec
Security in data link layer?
Other security systems Kerberos, X.509
Figure 2.10
5
Terms about Internet security
- HTTPS
- Secure Hypertext Transfer Protocol
- an application layer protocol for WWW
- using a Secure Socket Layer (SSL).
- SSL
- Secure Socket Layer,
- a transport layer protocol
- Similar to socket but adding encryption and
authentication - TLS
- Transport Layer Security
- A transport layer protocol
- The IETF version of SSL
6
Terms about Internet security
- SSH
- Secure SHell
- An application layer protocol (initially)
- Replace telnet, rlogin, ftp
- Generalized as a transport layer protocol
- PGP
- Pretty Good Privacy
- An application layer protocol
- Embedded in email such as elm
- Flexible public key certificate and verification
7
Terms about Internet security
- PEM
- Privacy Enhanced Mail
- An application protocol
- For secure email
- Strict hierarchy in public key certificate
- IPSec
- Internet Protocol Security
- A network layer protocol
- Contains two parts (may use separately)
- AH Authentication Header
- ESP Encapsulation Security Payload
8
Terms about Internet security
- IKE
- Internet Key Exchange, Establishing key used in
IPSec. - PKI
- Public Key Infrastructure
- Refer to the widespread availability of public
keys and certificates - ISAKMP
- Internet Security Association and Key Management
Protocol. - Kerberos
- A system for authentication based on secret keys
- OAKLEY
- An IETF protocol that provides s mechanism that
two authenticated parties can agree on secure and
secret keying material
9
SSHSecure Shell
- Originated from an academic project in Finland
- commercialized in 1998 by SSH Communications
Security - SSH1 expired in May 1995 because of security
flaws - SSH2 is currently used
10
SSH protocol suite (architecture)
- SSH transport layer protocol (TLP)
- (server) authentication, confidentiality, and
integrity - SSH (user) authentication protocol (UAP)
- run on top of the above transport layer protocols
- SSH connection protocol (CP)
- Provides interactive login sessions, remote
execution of commands, forwarded TCP/IP
connections, and forwarded X11 connections. (all
these connections are called channel) - Run on top of above two protocols
- SSH secure file transport protocol (SFTP)
11
SFTP protocol
- runs over a secure channel
- Server and client are inter-authenticated
- The channel will support encryption and integrity
- Run in request-response mode
- Independent from other SSH protocols
- may run on top of other secure protocols, e.g.,
TLS - Current use with the SSH Connection Protocol
- Run as a subsystem of the connection, name is
sftp - After a channel is opened, activate sftp server
by starting a shell or command.
12
Format of starting a shell or command
- byte SSH_MSG_CHANNEL_REQUEST uint32
recipient channel - string "subsystem"
- boolean want reply
- string subsystem-name (i.e., sftp)
13
A typical login session (connection) scenario
14
A SSH login session steps
- The client makes a connection to a server.
- The server identifies itself with it's public
host key (1024 bit RSA or DSA). - The client then generates a random 256-bit number
and chooses an encryption algorithm (eg. 3DES).
The random number is then encoded with RSA or
DSA. - The server decodes the RSA/DSA encryption and
reconstructs the session key and sends a
confirmation. - The above 4 steps authenticate the server
and setup a secure transport layer connection
(TLP) - The client then sends a username authentication
request. The server replies with a success or
failure. - this step will authenticate user (UAP) by
user password or user public key. - A default login session is established
- the user can do whatever he/she wants to do
(CP)
15
SSH and man-in-the-middle attack
- How does a client verify the host key?
- Check local database
- If exist, the server is authenticated, connection
is established - If not exist, currently let user to determine
- (because public certificates are not used widely)
- Build connection with saving the server host key
- Build connection without saving.
- Therefore there exists a possibility of
man-in-the-middle attack.
16
SSH2 Features and Specifications
- Authentication methods.
- Host-based (SSH server host key)
- password protection with 1024 bit RSA-key
(public-key cryptographic algorithm). - Ability to add certificate and public key
authentication. - Public key algorithm support DSA and
Diffie-Hellman key exchange. - PGP key support.
17
SSH2 Features and Specifications (cont.)
- Data encryption for confidentiality and
integrity. - Encryption algorithms DES, 3DES Blowfish,
Twofish, Arcfour, CAST128-CBC, 128 bit AES, or
256 bit AES. - Hash Algorithms MD5 and SHA1.
18
SSH2 Features and Specifications (cont.)
- Additional functionality.
- SFTP (secure file transfer protocol) was
introduced with SSH2 - TCP/IP port forwarding (Tunneling)
- X11 connections for secure X Window System
- TCP Wrapper support.
- The TCP Wrappers is a public-domain tool/package
you can monitor and filter incoming requests for
the SYSTAT, FINGER, FTP, TELNET, RLOGIN, RSH,
EXEC, TFTP, TALK, and other services - Multiple channel support.
- Distributed key management.
19
Tunneling
- A mechanism to encapsulate a message/packet
within another message/packet and transfer
through a network without touching the internal
message/packet. - Analogy to English Channel (railway tunneling)
- Typical scenario for Tunneling
- Two same networks connected by a different
network - Multicast backbone
- Mobile host moves out of its home area
- IPSec tunneling mode
- SSH port forwarding
20
TCP/IP port forwarding
Picture copied from http//www.bitvise.com/port-fo
rwarding.html