Motivation PowerPoint PPT Presentation
Title: Motivation
1
Group-based Peer Authentication for Wireless
Sensor Networks
Taojun Wu, Nathan Skirvin, Jan Werner, Brano
Kusy, Akos Ledeczi, Yuan Xue (Vanderbilt
University)
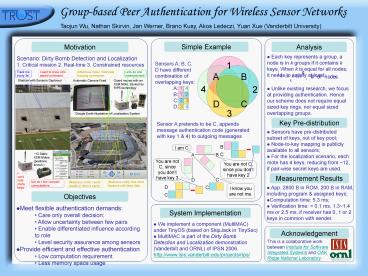
Motivation
Simple Example
Analysis
- Each key represents a group, a node is in k
groups if it contains k keys. When k is equal for
all nodes, it needs to satisfy at least - Unlike existing research, we focus at providing
authentication. Hence our scheme does not require
equal sized key rings, nor equal sized
overlapping groups.
- Scenario Dirty Bomb Detection and Localization
- 1. Critical mission 2. Real-time 3. Constrained
resources
Key Pre-distribution
Sensor A pretends to be C, appends message
authentication code (generated with key 1 4) to
outgoing messages
- Sensors have pre-distributed subset of keys, out
of key pool - Node-to-key mapping is publicly available to all
sensors - For the localization scenario, each mote has 4
keys, reducing from 12, if pair-wise secret keys
are used.
Measurement Results
- App. 2800 B in ROM, 200 B in RAM, including
program assigned keys - Computation time 5.3 ms
- Verification time lt 0.1 ms, 1.31.4 ms or 2.5
ms, if receiver has 0, 1 or 2 keys in common with
sender.
Objectives
- Meet flexible authentication demands
- Care only overall decision
- Allow uncertainty between few pairs
- Enable differentiated influence according to
role - Level security assurance among sensors
- Provide efficient and effective authentication
- Low computation requirement
- Less memory space usage
System Implementation
- We implement a component (MultiMAC) under TinyOS
(based on SkipJack in TinySec) - MultiMAC is part of the Dirty Bomb Detection and
Localization demonstration (Vanderbilt and ORNL)
of IPSN 2006. http//www.isis.vanderbilt.edu/proje
cts/rips/
Acknowledgement
This is a collaborative work between Institute
for Software Integrated Systems and OAK Ridge
National Laboratory.
PowerShow.com is a leading presentation sharing website. It has millions of presentations already uploaded and available with 1,000s more being uploaded by its users every day. Whatever your area of interest, here you’ll be able to find and view presentations you’ll love and possibly download. And, best of all, it is completely free and easy to use.
You might even have a presentation you’d like to share with others. If so, just upload it to PowerShow.com. We’ll convert it to an HTML5 slideshow that includes all the media types you’ve already added: audio, video, music, pictures, animations and transition effects. Then you can share it with your target audience as well as PowerShow.com’s millions of monthly visitors. And, again, it’s all free.
About the Developers
PowerShow.com is brought to you by CrystalGraphics, the award-winning developer and market-leading publisher of rich-media enhancement products for presentations. Our product offerings include millions of PowerPoint templates, diagrams, animated 3D characters and more.