Create Avg Network PowerPoint PPT Presentations
All Time
Recommended
Using this, add more devices to Network, install applications on other PCs, phones & tablets and even invite your family members to join your network. Source: https://avgsupportaustralia.blogspot.com.au/2018/01/create-and-connect-to-avg-network.html
| PowerPoint PPT presentation | free to download
Trojan horse. Claims to be something desirable, but hides something harmful. Network Virus ... Environments with huge data quantities requiring quick availability ...
| PowerPoint PPT presentation | free to download
Data storage plays an essential role in today's fast-growing data-intensive network services. ... Amortize request/transfer cost. Client uses a disk cache ...
| PowerPoint PPT presentation | free to view
... of spatial preference do ... Analyze the graph properties? Group of good friends... Cliques with ... (1 day) its metrics (CC, PL) almost saturate ...
| PowerPoint PPT presentation | free to download
Title: NetShield: Massive Semantics-Based Vulnerability Signature Matching for High-Speed Networks Author: ZHICHUN Last modified by: Yan Created Date
| PowerPoint PPT presentation | free to download
100 KB/hr, 25 GB/lifetime. Hear (Speech @ 10KB/s) 40 MB/hr, 10 TB/lifetime. See (TV @ .5 MB/s) 2 GB/hr, 500TB/lifetime. 1K=210. 1M=220 ...
| PowerPoint PPT presentation | free to view
Money doesn't create man but it is the man who created money. -Warren Buffet WELCOME TO ALL OF YOU RAHUL JAIN (Striving for excellence) BCOM (H), MBA, ACS Cost Any ...
| PowerPoint PPT presentation | free to download
Networks and Pervasive Computing program. National ICT Australia. June 2005 ... class of subtle distributed programming bugs due to locking, race conditions, etc. ...
| PowerPoint PPT presentation | free to view
Title: Chapter 7 Lecture Presentation Subject: Packet-Switching Networks Author: Leon-Garcia/Widjaja Last modified by: Stephen Asa Baber Created Date
| PowerPoint PPT presentation | free to download
AVG has created a complete solution for users to save data through avg retail , which is AVG internet security. Malware and internet threats only do not affect your computer or device, but it is affecting your personal data as well. Using webcam spying and ransomware, hackers can easily steal your personal files, photos, videos, and any of your personal data.
| PowerPoint PPT presentation | free to download
SENSOR NETWORKS ARCHITECTURE MICA Motes BWN Lab @ GaTech SENSOR NETWORKS FEATURES APPLICATIONS: Military, Environmental, Health, Home, Space Exploration ...
| PowerPoint PPT presentation | free to view
SENSOR NETWORKS ARCHITECTURE MICA Motes BWN Lab @ GaTech SENSOR NETWORKS FEATURES APPLICATIONS: Military, Environmental, Health, Home, Space Exploration ...
| PowerPoint PPT presentation | free to view
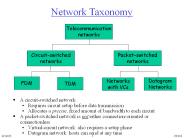
UNIT 3 NETWORK LAYER Network Layer It is responsible for end to end (source to destination) packet delivery, whereas the data link layer is responsible for node to ...
| PowerPoint PPT presentation | free to download
AVG has created a complete solution for users to save data through avg retail , which is AVG internet security. Malware and internet threats only do not affect your computer or device, but it is affecting your personal data as well. Using webcam spying and ransomware, hackers can easily steal your personal files, photos, videos, and any of your personal data.
| PowerPoint PPT presentation | free to download
SENSOR NETWORKS BY Umesh Shah Mayuresh Patil G P Reddy GUIDES Prof U.B.Desai Prof S.N.Merchant
| PowerPoint PPT presentation | free to view
all milestones in resolution of problem create a new ticket entry with reference ... Ticket information log : toppingb@facesofdeath.ns.itd.umich.edu said ...
| PowerPoint PPT presentation | free to download
Title: TCP Author: Younghee Lee Last modified by: Created Date: 7/19/1998 12:47:56 PM Document presentation format:
| PowerPoint PPT presentation | free to view
SMTP, POP3, IMAP. 2.5 DNS. 2.6 P2P file sharing. 2.7 Socket programming with TCP ... SMTP / POP3 / IMAP. DNS. programming network applications. socket API. 4/12 ...
| PowerPoint PPT presentation | free to download
Sensor Networks & Applications Partly based on the book Wireless Sensor Networks by Zhao and Guibas Constraints and Challenges Limited hardware: Storage Processing ...
| PowerPoint PPT presentation | free to download
1. INTRODUCTION SENSOR NETWORKS ARCHITECTURE Key technologies that enable sensor networks: Micro electro-mechanical systems (MEMS) Wireless communications Digital ...
| PowerPoint PPT presentation | free to view
Title: End-to-end Architecture for Quality Adaptive Streaming Applications in Best-effort Networks Author: Library Last modified by: asodeh Created Date
| PowerPoint PPT presentation | free to download
NEXT STEPS: Open For Business CVC Business Plan Competition Network Community Vitality Center A Catalyst for Creating Real Impact in Real Communities
| PowerPoint PPT presentation | free to download
Impact on devices (measurements and measuring) ... (to inform the source that it's pointless to keep sending more packets at the present time) ...
| PowerPoint PPT presentation | free to download
Countries monitored. Contain 78% of world population. 99% of online users of Internet ... nlanr.net/training/presentations/tcp-tutorial.ppt. www-didc.lbl.gov ...
| PowerPoint PPT presentation | free to download
xgraph (gnuplot, MS Excel, ..) - ps file. Uni Innsbruck Informatik - 10. Simulation elements ... example in the Marc Greis tutorial (easy - try it!) simple end ...
| PowerPoint PPT presentation | free to download
School of Electrical and Computer Engineering. Georgia ... Motes. BWN ... Rene Mote. Dot Mote. weC Mote. Mica node. 7. IFA'2004. SENSOR NETWORKS ...
| PowerPoint PPT presentation | free to view
Title: PowerPoint Presentation Author: Rajeev Balasubramonian Last modified by: RB Created Date: 9/20/2002 6:19:18 PM Document presentation format
| PowerPoint PPT presentation | free to download
... time slot, each node computes an MD5 hash, that computes its priority ... Each node computes a schedule of slots (and intended receivers) in which will transmit ...
| PowerPoint PPT presentation | free to view
Title: High Performance Active End-to-end Network Monitoring Author: cottrell Last modified by: cottrell Created Date: 10/17/1999 7:36:36 PM Document presentation format
| PowerPoint PPT presentation | free to download
Database Middleware for Sensor Networks
| PowerPoint PPT presentation | free to download
Title: PCI Express Author: almdavis Last modified by: yzhang01 Created Date: 6/29/2004 2:06:31 PM Document presentation format: On-screen Show Company
| PowerPoint PPT presentation | free to download
IT351: Mobile & Wireless Computing Wireless Personal Area Networks (WPAN) Part-2: IEEE802.15 Bluetooth Objectives: To introduce Ad Hoc networking and discuss its ...
| PowerPoint PPT presentation | free to download
Title: PowerPoint Presentation Last modified by: ABC Created Date: 1/1/1601 12:00:00 AM Document presentation format: On-screen Show Other titles
| PowerPoint PPT presentation | free to download
Title: Neural Networks Author: David R. Musicant Last modified by: Carleton College Created Date: 1/29/2001 2:55:52 AM Document presentation format
| PowerPoint PPT presentation | free to download
nsrc@summer workshop. eugene, oregon. Network Performance Definitions & Analysis ... Very little free memory. Lots of swap activity (swap in, swap out)? Slow I/O ...
| PowerPoint PPT presentation | free to download
Middleware The fascinating world between network and application Erik Ombelets EAI, KBC ICT
| PowerPoint PPT presentation | free to download
... sort packets according to completion time in ideal system Packetized GPS/WFQ Compute ... no protection Aggregation into ... Transmission line User ...
| PowerPoint PPT presentation | free to download
Applications of Network Theory. World Wide Web and hyperlink structure ... 1937: J.L. Moreno introduced sociometry; he also invented the sociogram ...
| PowerPoint PPT presentation | free to download
reverse mapping on the way back. destination host does not know ... Disadvantage: one lookup may take O(m), where m is number of bits (32 in the case of IPv4) ...
| PowerPoint PPT presentation | free to view
Critical Infrastructure Protection In the Transportation Network A Mathematical Model and Methodology for Determining and Analyzing The k-Critical Links of a Highway ...
| PowerPoint PPT presentation | free to view
Automatically Building Special Purpose Search Engines with ...
| PowerPoint PPT presentation | free to download
Automatically Building Special Purpose Search Engines with ...
| PowerPoint PPT presentation | free to download
Macro Virus- These types of viruses load themselves into the templates used in ... http://i122.photobucket.com/albums/o272/softarchive/img13/26909_s__avast_pr o_v_1. ...
| PowerPoint PPT presentation | free to view
Automatically Building Special Purpose Search Engines with ...
| PowerPoint PPT presentation | free to download
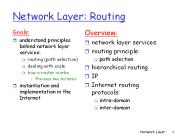
abstraction provided. by network layer: service abstraction. Network Layer #4. Virtual circuits ... each packet carries VC identifier (not destination host ID) ...
| PowerPoint PPT presentation | free to download
Wireless Ad Hoc Network Routing Protocols CSE 802.11 Maya Rodrig Ad hoc networking Infrastructureless networking mobile nodes dynamically establish routing among ...
| PowerPoint PPT presentation | free to download
Identifying stocking points ... Compare the output of the model to existing data ... Simulation models: provide a mechanism to evaluate specified design alternatives ...
| PowerPoint PPT presentation | free to download
Design or configure the logistics network so as to minimize annual system-wide ... Assign each market to closet WH. Then assign each plant based on cost. D = 50,000 ...
| PowerPoint PPT presentation | free to view
CSE 592 Applications of Artificial Intelligence Neural Networks & Data Mining Henry Kautz Winter 2003 Kinds of Networks Feed-forward Single layer Multi-layer ...
| PowerPoint PPT presentation | free to download
Title: End-to-end Estimation of Available Bandwidth Variation Range Author: Manish Last modified by: localadmin Created Date: 12/5/2004 11:04:05 PM
| PowerPoint PPT presentation | free to download
An Introduction to Computer Networks Lecture 16: Security I have used s from Mackeown, Stanford, Raj Jain, WuStl, etc, to prepare these s
| PowerPoint PPT presentation | free to view
Title: Presentation Title Author: PacifiCorp Last modified by: Les Bahls Created Date: 6/25/1999 4:13:50 PM Document presentation format: On-screen Show
| PowerPoint PPT presentation | free to download
Earthquake monitoring in shake-test sites. ... Habitat Monitoring: Storm petrels on Great Duck Island, microclimates on James Reserve. ...
| PowerPoint PPT presentation | free to download
Title: PowerPoint Presentation Author: bhuyan Last modified by: Laxmi Bhuyan Created Date: 5/29/2002 7:33:54 PM Document presentation format: On-screen Show (4:3)
| PowerPoint PPT presentation | free to download
e.g 'oscar winners' Resistant to text spamming. Generated substantial amount of research ... adj list. Mercator Crawler [NH01] Not much different from what we ...
| PowerPoint PPT presentation | free to view
Network Operations Centers Training Programs Quilt NOC Workshop Panel Discussion: CENIC Indiana University/Global NOC WiscNet Pacific Northwest GigaPop
| PowerPoint PPT presentation | free to view