Protocol PowerPoint PPT Presentations
All Time
Recommended
Protocols and Protocol Suit Review Lecture 14 IP, TCP and UDP Error Checksum Q:- IP, TCP, and UDP all discard a packet that arrives with a checksum error and do not ...
| PowerPoint PPT presentation | free to view
IF YOU IDENTIFY MISTAKES IN THE PROTOCOLS OR IF YOU HAVE SUGGESTIONS FOR ... added pediatric dose for treating torsade (CAT. B) ...
| PowerPoint PPT presentation | free to view
Modelling and Analysing of Security Protocol: Lecture 1 ... Signing SignK(M), SK(M), MACK(M) Hashing #(M), Hash(M) We assume that these are prefect ...
| PowerPoint PPT presentation | free to download
Modelling and Analysing of Security Protocol: Lecture 3. Protocol Goals. Tom Chothia ... A high level overview the to cryptography ...
| PowerPoint PPT presentation | free to download
What you have learn on this course (hopefully) are skill to ... Cross between a protocol and Crypto method. Common base for many protocols. Common Protocols ...
| PowerPoint PPT presentation | free to download
RFC4168 The Stream Control Transmission Protocol (SCTP) as a Transport for the Session Initiation Protocol (SIP) Teacher:Quincy Wu Presented by: Ying-Neng Hseih
| PowerPoint PPT presentation | free to view
Office of Training and Tertiary Education ... National Protocols for Higher Education Approval Processes ... Protocol 7: Codified internal grievance procedures ...
| PowerPoint PPT presentation | free to view
UC Berkeley WOW. Wireless Token Ring Protocol (WTRP) A Medium Access Control Protocol for ... UC Berkeley WOW. Automated Vehicle Platoon. Real-time safety ...
| PowerPoint PPT presentation | free to view
IMAP (Internet Message Access Protocol) is used for storing and retrieving e-mails ... It can connect to an email server using IMAP ...
| PowerPoint PPT presentation | free to view
A Protocol Converter is a method used to transform ordinary or registered protocol of one device to the protocol appropriate for the other device or tools to accomplish the interoperability.
| PowerPoint PPT presentation | free to download
Tech LTE World is a company at the help of 5G protocol testing and has created a comprehensive and fully integrated 5G network testing selection of cloud enabled test devices and equipment, software automation services, network test solution and reduces end-to-end latency.
| PowerPoint PPT presentation | free to download
Network Protocols Transmission Control Protocol/Internet Protocol (TCP/IP) Asynchronous Transfer Mode (ATM) NWLink NetBIOS Enhanced User Interface (NetBEUI)
| PowerPoint PPT presentation | free to view
Universal Protocol At completion of this session each individual will be able to: Verbalize the process to ensure the correct identification of the right patient ...
| PowerPoint PPT presentation | free to download
* Protocol Question Time Define a network protocol. It s an agreed-on set of rules that computers use to ensure reliable communications * 2.
| PowerPoint PPT presentation | free to view
A Protocol s Life After Attacks let s investigate beyond ... Is the Verification Problem for Cryptographic Protocols Solved? Author: Giampaolo Bella
| PowerPoint PPT presentation | free to download
TCP/IP Protocol TCP/IP Protocol TCP/IP TCP/IP Protocol Stack TCP/IP OSI TCP/IP Protocol Stack Application Layer TCP/IP Transport ...
| PowerPoint PPT presentation | free to download
allows the designer to prepare an abstract model of the protocol for testing and ... checks the packet for corrupted data. Notcorrupt(rcvpkt): checks for ...
| PowerPoint PPT presentation | free to view
Internet Protocol (IP) Basic Functions Connectionless Protocol Packet Encapsulation
| PowerPoint PPT presentation | free to download
PROTOCOL VERIFICATION & PROTOCOL VALIDATION Properties of Verification BAD THINGS WILL NOT HAPPEN Non-violation of assertions (operation that take place in a protocol ...
| PowerPoint PPT presentation | free to view
Signaling Protocol. Communication setup, tear-down and control ... multi-endpoint invitation-based communication ... Also a soft state protocol for robustness: ...
| PowerPoint PPT presentation | free to download
Border Gateway Protocol (BGP4 ... OSPF, ISIS, EIGRP, RIP EGP Exterior Gateway ... static Care required with redistribution redistribute
| PowerPoint PPT presentation | free to download
Internet Protocols Overview Internet documents Internet drafts Proposed, draft and Internet standard Informational Historical Experimental Best Common Practice For ...
| PowerPoint PPT presentation | free to download
Protocole TCP Dominique SERET TCP : Transmission Control Protocol transport fiable de la technologie TCP/IP fiabilit = illusion assur e par le service d coupage ...
| PowerPoint PPT presentation | free to download
Protocol Steganography Norka Lucena and Steve Chapin Syracuse University May 27, 2004 What is Protocol Steganography? Embedding information within messages and ...
| PowerPoint PPT presentation | free to download
Advanced Cryptographic Protocols Lecture 12 Supakorn Kungpisdan supakorn@mut.ac.th NETE4630 *
| PowerPoint PPT presentation | free to view
Standards and Protocols Chapter 7
| PowerPoint PPT presentation | free to view
Multimedia Streaming Protocols Multimedia Streaming Protocols signalling and control protocols protocols conveying session setup information and VCR-like commands ...
| PowerPoint PPT presentation | free to download
Title: CS395T - Design and Analysis of Security Protocols Subject: Protocol Logic Author: Vitaly Shmatikov Last modified by: Vitaly Shmatikov Created Date
| PowerPoint PPT presentation | free to download
Dynamic Routing Protocols Why Dynamic Routing Protocols? Each router acts independently, based on information in its router forwarding table Dynamic routing protocols ...
| PowerPoint PPT presentation | free to download
Protocol Mechanics Why do we write one? How to begin Requirements for submitting a research protocol and types - Nuts and Bolts Basic elements of informed consent
| PowerPoint PPT presentation | free to view
CS 259 Protocols for Anonymity Vitaly Shmatikov Overview Basic concepts of anonymity Chaum s MIX Dining cryptographers Knowledge-based definitions of anonymity ...
| PowerPoint PPT presentation | free to download
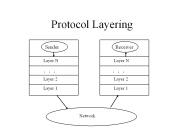
Protocol Layering Sender Receiver Layer N Layer N. . .. . . Layer 2 Layer 2 Layer 1 Layer 1 Network Motivation for Protocol Layering - The Programming Language ...
| PowerPoint PPT presentation | free to download
A network protocol refers to a set of rules that govern data transmission among different devices in a network. Its examples are TCP, IP, FTP, SMTP, HTTP, HTTPS etc.
| PowerPoint PPT presentation | free to download
ISO/OSI protocol suite. IBM Systems Network Architecture (SNA) Digital DECnet. Novell NetWare ... FTP (File Transfer Protocol) Exchanging Files ...
| PowerPoint PPT presentation | free to download
Protocolled helps you in finding natural health protocols and healing solution & treatment. These protocols will help in testing several different Natural Health Products in different ways.
| PowerPoint PPT presentation | free to download
Protocolled helps you in finding natural health protocols and healing solution & treatment. These protocols will help in testing several different Natural Health Products in different ways.
| PowerPoint PPT presentation | free to download
Protocol for New AVF Cannulation Protocol for New AVF Cannulation Define successful cannulation Cannulation guidelines New AVF Mature AVF Unsuccessful cannulations ...
| PowerPoint PPT presentation | free to download
Protocolled provides 100% Natural Health Management Protocol. It’s an excellent natural weight management program to reduce your extra weight in natural way. This protocol will test different applications of the Natural Products.
| PowerPoint PPT presentation | free to download
Communications Protocol All communications between devices require that the devices agree on the format of the data. The set of rules defining a format is called a ...
| PowerPoint PPT presentation | free to download
SIP Protocol Evaluation Rajiv Dharmadhikari SIP SIP is a protocol for initiating, modifying, and terminating multimedia sessions. SIP is a pretty mature, well ...
| PowerPoint PPT presentation | free to download
Amendments immediately placed into protocol. Helps mapping protocols ... Continuing review report - List of amendments and adverse events ...
| PowerPoint PPT presentation | free to view
Network File System Protocol By Authentication Experts
| PowerPoint PPT presentation | free to download
Elements of Transport Protocols THE INTERNET TRANSPORT PROTOCOL (TCP and UDP) The Internet has two main protocols in the transport layer, connectionless protocol ...
| PowerPoint PPT presentation | free to download
Example (Needham-Schroeder) Properties. Evaluation. Security Protocol Specification Languages ... Needham-Schroeder Protocol. Devised in '78. Example of weak ...
| PowerPoint PPT presentation | free to download
Understand the historical nature Gopher protocol ... Gopher - only develop in 1992 ... Gopher will go and locate the information for you - no longer popular ...
| PowerPoint PPT presentation | free to view
Title: Border Gateway Protocol Author: Philip Smith Description: Based on work by Abha Ahuja (2001), Philip Smith (2002, 2003), Alan Barrett (2004)
| PowerPoint PPT presentation | free to download
Standards and Protocols Unit 6, Chapter 12 LAN Installation & Operation Objectives Describe the installation and operation of a LAN. Describe the necessary management ...
| PowerPoint PPT presentation | free to download
(But, the collusion is possible.) Everyone knows who voted and who didn't. ... As stated above, the collusion is possible. Protocols. 1. Simplistic voting protocols #1 ...
| PowerPoint PPT presentation | free to view
Authentication Protocols Celia Li Computer Science and Engineering York University * * Outline Overview of authentication Symmetric key authentication protocols ...
| PowerPoint PPT presentation | free to download
Cryptographic Protocols Reference: , Charles P., Security in Computing, 2nd Edition, Prentice Hall, 1996. Definition of Protocols A protocol is an orderly sequence of ...
| PowerPoint PPT presentation | free to view
Title: Point-to-Point Protocol Author: MP Perrenot Last modified by: RESPECI Created Date: 4/19/1996 4:53:16 PM Document presentation format: Personnalis
| PowerPoint PPT presentation | free to download
Title: The Internet Protocols Author: Hans Kruse Last modified by: Hans Kruse Created Date: 9/15/1997 1:56:56 PM Document presentation format: Letter Paper (8.5x11 in)
| PowerPoint PPT presentation | free to view
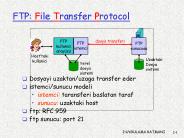
FTP: File Transfer Protocol dosya transferi FTP kullan c aray z FTP istemci FTP sunucusu Host taki kullan c Uzaktaki Dosya sistemi Yerel dosya sistemi
| PowerPoint PPT presentation | free to download
A VPN is the process of creating the safe and secure connection to and from the computer or the network. In other words, VPN is the virtual private network which allows the users to connect with the private network over the Internet for accessing the data privately and securely. Secure VPN protocols creates the encryption which is known as VPN tunnel.
| PowerPoint PPT presentation | free to download