Tnew PowerPoint PPT Presentations
All Time
Recommended
FOR MORE CLASSES VISIT www.comm470outlet.com COMM 470 Week 1 Analyzing Messages Essay COMM 470 Week 1 DQ 1 and DQ 2 COMM 470 Week 2 DQ 1 and DQ 2
| PowerPoint PPT presentation | free to download
Copy Link ; good.readbooks.link/pwr/0323443370
| PowerPoint PPT presentation | free to download
[318 Pages Report] The market for instrument transformers is anticipated to witness substantial growth, projected to increase from an estimated USD 7.1 billion in 2023 to reach USD 10.6 billion by 2030. The growing demand for precise electrical measurements is a major driving force behind the global expansion of instrument transformers. These transformers are critical for accurately measuring and monitoring electrical properties in power systems.
| PowerPoint PPT presentation | free to download
Virtualization: Object-based Parallelization. User View. System implementation ... Dynamically allocate one instance of globals ...
| PowerPoint PPT presentation | free to download
Impact of Variability. Optimal Sharing. Compare the two ... Idea of Proof ... What is the impact on waiting time when capacity is doubled ? 21. Case Study. 22 ...
| PowerPoint PPT presentation | free to view
Birkbeck college, University of London. ER 2004. 8th ~ 12th November 2004. Outline. Motivation ... Jack. CS01. C03. C02. C01. SName. SID. CStab: 'CStab' 'Cstab, ...
| PowerPoint PPT presentation | free to view
offsets along the same reflection in the CRP gather will diverge in time from the ... The estimated velocity update for each CRP gather are backprojected ...
| PowerPoint PPT presentation | free to view
A = B op C. Assume memory access takes 4 cycles and a typical operation takes 2 cycles ... Double operation speed. Calculate how many memory accesses are needed first? ...
| PowerPoint PPT presentation | free to download
float FirstIntersect(ray iobject, x) // =0 if no intersection. t = -1. FOR each object ... Color Trace( ray ) IF (FirstIntersect(ray object, x) = 0) RETURN La. ENDIF ...
| PowerPoint PPT presentation | free to download
SIGMOD 2006, Chicago, IL. 1 ... SIGMOD 2006, Chicago, IL. 4. Skycube (Yuan, ... SIGMOD 2006, Chicago, IL. 14. Querying CSC. Overview example: query space ...
| PowerPoint PPT presentation | free to view
be 'implementable' at PHON; in effect, they (would) induce Crash at PF. ... Syntactically Valued features as PHON features; solves the 'after is too late' problem. ...
| PowerPoint PPT presentation | free to view
Title: Introduction to Real-Time Systems Author: Computer Science Department Last modified by: CITYU Created Date: 9/3/1996 8:45:46 PM Document presentation format
| PowerPoint PPT presentation | free to download
[Das et al., ISVLSI, 2003] Generalized view. Bulk wafer. Metal level. of wafer 1. Layer 1 ... [Joyner, Zarkesh-Ha and Meindl, ASIC/SOC '01] from Intel. 5 ...
| PowerPoint PPT presentation | free to view
001011101 (codeword: a=0, b=00, c=01, d=11.) Where to cut? ... Output: a binary tree representing codewords so that the total number of bits ...
| PowerPoint PPT presentation | free to download
Good News ... Exciting News ... parameterization (black) better than the Kessler-type parameterization (green) ...
| PowerPoint PPT presentation | free to view
Title: : PCR-PLS Author: Andrey Bogomolov Last modified by
| PowerPoint PPT presentation | free to view
Faculty of Electrical Engineering Department of Computer Engineering University of Belgrade, Serbia and Informatics Autonomous Visual Model Building based ...
| PowerPoint PPT presentation | free to download
COSC 3407: Operating Systems Lecture 4: Concurrency: Threads and Dispatching
| PowerPoint PPT presentation | free to view
Pipeline stalled for one cycle. Recovery steps initiated based on ... Stall reservation station. Invalidate instruction in ROB as well as dependent instructions ...
| PowerPoint PPT presentation | free to view
Title: Introduction to Computer Systems Author: Binyu Zang Last modified by: Yi Li Created Date: 1/15/2000 7:54:11 AM Document presentation format
| PowerPoint PPT presentation | free to view
move queen so it conflicts with fewer queens. Local Search - Exchange Heuristics ... Ant Colony Optimization: pheromones - good for networks, dynamic optimization ...
| PowerPoint PPT presentation | free to view
guru a religious leader or teacher in the Hindu or Sikh religion or, more ... Get your scent right! Do you have the right scent? Engagement metric 5: ...
| PowerPoint PPT presentation | free to view
John Deere NO.4 Big Enclosed Gear Mower (High Lift) Operator’s Manual Instant Download (Publication No.OMH2850)
| PowerPoint PPT presentation | free to download
Read an whole text beforehand, and build an index (suffix array/trees) for it. ... A case where we don't know the length of data beforehand, e.g. streaming data ...
| PowerPoint PPT presentation | free to view
Medicinal & Natural Products Chemistry Research Center, Shiraz University ... Scree plot, indicator function, imbedded error, real error, ... 4Th. ICW. 4Th ICW ...
| PowerPoint PPT presentation | free to view
00000000 52 6F 6C 65 78 20 4E 65 77 62 69 65 20 46 41 51 Rolex Newbie FAQ ... 00000050 20 6D 79 20 6E 65 77 20 72 6F 6C 65 78 3F 0D 0A my new rolex? ...
| PowerPoint PPT presentation | free to download
John Deere NO.4 Big Enclosed Gear Mower (High Lift) Operator’s Manual Instant Download (Publication No.OMH2850)
| PowerPoint PPT presentation | free to download
Confinement and Local Transport in the National Spherical Torus ... H. Park1, G. Rewoldt1, S.A. Sabbagh6, D. Smith1, D. Stutman7, K. Tritz7, W. Wang1, H. Yuh4 ...
| PowerPoint PPT presentation | free to download
Run pixie -idtrace. Run dis -h. Dynamic trace. Scheduler. Result ... Instrumented program prog.pixie. Block Diagram of the Scheduler. Dependency analyzer ...
| PowerPoint PPT presentation | free to download
Clock and Time Management. Communications Kernel. Interrupt Handling. Operating ... System needs some data structures to keep track the state and miscellaneous ...
| PowerPoint PPT presentation | free to view
John Deere NO.4 Big Enclosed Gear Mower (High Lift) Operator’s Manual Instant Download (Publication No.OMH2850)
| PowerPoint PPT presentation | free to download
'Chemometrics is the application of mathematical or statistical ... Beer-Lambert. ANOVA. Projection methods and latent variables -0.6 -0.4 -0.2. 0. 0.2. 0.4 ...
| PowerPoint PPT presentation | free to view
vulnerable to a replay attack and an impersonation attack. Hwang-Li's scheme (2000) ... Knowing the session key K = w, E can impersonate U to communicate with S. ...
| PowerPoint PPT presentation | free to view
Christopher M. Bishop, Pattern Recognition and Machine Learning degree of belief data W * capture our beliefs about the ...
| PowerPoint PPT presentation | free to view
http://www.antivirus.com/pc-cillin/vinfo/virusencyclo/ Activation or Trigger ... Reboot computer from a clean disk then run anti-viral software ...
| PowerPoint PPT presentation | free to view
Main Topics in the Lecture. Process and thread management. Interrupt and trap handling ... Point to the PCB of the parent process. A link list of PCBs of the ...
| PowerPoint PPT presentation | free to view
... there can be clumping caused by the complex underlying genome sequence structure ... ENm001: ENCODE Consortium annotated over 2500 feature-instances ...
| PowerPoint PPT presentation | free to view
... cost of manufacturing each copy of the system, excluding NRE cost ... Program memory. General datapath with large register file and general ALU. User benefits ...
| PowerPoint PPT presentation | free to view
Each multicast group has a group leader. 1st node joining a group becomes ... Mauve, M., F ler, H., Widmer, J., Lang, T., 'Poster: Position-Based Multicast ...
| PowerPoint PPT presentation | free to download
(1) Lexical analysis of the text with the objective of treating digits, hyphens, ... sow fox pig eel yak hen ant cat dog hog. ant cat dog eel fox hen hog pig sow yak ...
| PowerPoint PPT presentation | free to download
extract the corresponding CRP trace. Change the azimuth and angle to repeat the process ... a) The estimated velocity updates for each CRP gather are ...
| PowerPoint PPT presentation | free to view
Simple algorithms to construct & manipulate. Application Niche ... Also called Cofactor operation (UCB) 13. Argument F. Restriction Execution Example ...
| PowerPoint PPT presentation | free to download
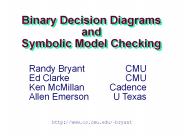
Ken McMillan Cadence. Allen Emerson U Texas. 2. Binary Decision Diagrams ... Simple algorithms to construct & manipulate. Application Niche ...
| PowerPoint PPT presentation | free to download
(Joint work with Xiaojing Xiang and Zehua Zhou) Xin Wang Assistant Professor Director, Wireless and Networking Systems Lab (WINS) http://www.cse.buffalo.edu/~xwang8
| PowerPoint PPT presentation | free to view
NSTX Addresses Transport & Turbulence Issues Critical to Both Basic Toroidal ... ITPA database to address high priority ITPA ... Weak vs Reverse-Shear L-mode ...
| PowerPoint PPT presentation | free to download
When they combine, constructive or destructive interference ... Space-time trellis codes. Orthogonal design Space-time block codes (ODSTBC): [Tarokh et al] ...
| PowerPoint PPT presentation | free to view
Electrical properties of neurons. Rub n Moreno-Bote. Galvani frog's legs experiment ... Passive properties of neurons (resting potential) Action potential ...
| PowerPoint PPT presentation | free to view
Integrating micro and macroevolution of development:
| PowerPoint PPT presentation | free to download
Chapter 6 Parallel Processors from Client to Cloud
| PowerPoint PPT presentation | free to download
... most widely used in computing systems such as computer algebra systems (maple, ... perform computations indicated by the formulas (semantics) Presentation: ...
| PowerPoint PPT presentation | free to view
Chapter 7 Multicores, Multiprocessors, and Clusters
| PowerPoint PPT presentation | free to view
Economic Impacts of Aquatic Invasive Species Oconto County presentation Dale Mohr CNRED UW-Extension Originally Presented by Chad Cook Basin Educator
| PowerPoint PPT presentation | free to view
Momentum Heat Mass Transfer MHMT4 Navier-Stokes equations Non-Newtonian fluids Newtonian fluids and Navier Stokes equations. Steady and transient flow between ...
| PowerPoint PPT presentation | free to download
If you don t know where you are going, any road will take you there George Harrsion Kompetansem l og vurdering Vurdering og vurderingskriterier som verkt y ...
| PowerPoint PPT presentation | free to download
Creating and Modifying Datasets in SAS A Little Background Before creating any data sets we need to discuss a little bit about SAS programming Programming is done ...
| PowerPoint PPT presentation | free to view


![[Download ]⚡️PDF✔️ Slatter's Fundamentals of Veterinary Ophthalmology 6th Edition PowerPoint PPT Presentation](https://s3.amazonaws.com/images.powershow.com/10128474.th0.jpg)