Log1 PowerPoint PPT Presentations
All Time
Recommended
The students will solve logarithmic expressions. ( Application) (Mathematics, ... ( loge or ln) STAI 6, 23, 26. Examples. Evaluate the expression log381. 3x = 81 ...
| PowerPoint PPT presentation | free to download
INTERESTING QUESTIONS & UNDOING EXPONENTS: LOGS Hey, hey logarithm When we get the blues
| PowerPoint PPT presentation | free to view
O(max(m,n)) if only similarity score is needed. More complicated 'divide-and-conquer' algorithm that ... log2(3)=1.585 bits or loge(3) = ln(3) = 1.1 nats ...
| PowerPoint PPT presentation | free to download
Exponents and Logarithms. In general, an exponential function is of the form: ... ln 14.3 means loge 14.3. Laws of Logarithms. loga(x y) = logax logay x 0, y 0 ...
| PowerPoint PPT presentation | free to view
Gene screening using ROC curves. Identifying differentially expressed genes ... Logs of ratios are symmetric around zero: The average of log(2) and log(1/2) is 0. ...
| PowerPoint PPT presentation | free to view
Both of these functions are invertible. The Graphs of f-1(x) for f(x) = ax. a ... loge x = ln x The 'Natural Logarithm' log10 x = log x The 'Common Logarithm' ...
| PowerPoint PPT presentation | free to view
But for what value of y does 2y = 6? ... Vert line x=0 is asy. Connect the dots. X=0. Graph y =log5(x 2) Plot easy points (-1,0) & (3,1) ...
| PowerPoint PPT presentation | free to view
Divide Pv into chunks of BlogBN. Divide each chunk into minichunks of size B ... ?2[k]: for each chunk, encode a Cartesian tree on the O(logBN) minichunks for ...
| PowerPoint PPT presentation | free to download
A New Idea: The Logarithm. Logs have a base ... On the one hand, you might always use 10, because that's what's on your calculator. ...
| PowerPoint PPT presentation | free to view
set c = (a*b-1) mod 2d. then C= (A-c*B)/2d is d bits shorter than A. The ... This method for computing b/a requires only O(log2k) bit operations, and so over ...
| PowerPoint PPT presentation | free to view
Log Equations Review OBJ: Review for Quest 2 Solve 1.162 s 2 = 24(2 s 2) = 2-1 4(2 s2) = -1 8 4s2 = -1 9 4s2 = 0 (3 2s)(3 + 2s) = 0 s ...
| PowerPoint PPT presentation | free to download
LOGARITMOS EXEMPLOS Compor (transformar num nico logaritmo) a express o E = log m log 3 + 2 log n. 1 . Vamos transformar a parcela 2 na forma de logaritmo ...
| PowerPoint PPT presentation | free to view
Clase 14.2 Tema: Funci n Exponencial ... Porque 10-2=0,01 , Porque 101/2 = 10 y = ln x significa ey = x Logaritmo natural com n (base e) Ejemplos: ...
| PowerPoint PPT presentation | free to view
Usando logaritmos, determine ap s quanto tempo os ve culos ter o o mesmo valor de mercado. Exemplo Fun es Logaritmos Neperianos 1) ...
| PowerPoint PPT presentation | free to view
Title: Funciones reales de variable real Author: Jos Manuel Reyes Brito Last modified by: Usuario Created Date: 3/25/2003 9:54:03 AM Document presentation format
| PowerPoint PPT presentation | free to view
Exponential and Logrithmic Functions
| PowerPoint PPT presentation | free to download
Funciones reales de variable real x f(x) x y = f(x) Jos Manuel Reyes Brito I.E.S. Albert Einstein Sevilla Funciones Lineales: y = mx + n Funciones ...
| PowerPoint PPT presentation | free to view
UNIVERSIDAD C SAR VALLEJO Facilitador: Lic. Mat. Patricia Isabel Aguilar Incio. * Se muestra el resumen general: Todas las funciones lineales tienen dominio y ...
| PowerPoint PPT presentation | free to view
Microsoft SQL Server Administration for SAP SQL Server with SAP
| PowerPoint PPT presentation | free to view
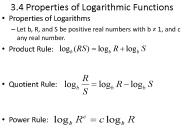
3.4 Properties of Logarithmic Functions Properties of Logarithms Let b, R, and S be positive real numbers with b 1, and c any real number. Product Rule:
| PowerPoint PPT presentation | free to download
2006/07/05 3 Succinct Data Structure
| PowerPoint PPT presentation | free to download
Specific, not abstract. Can only be done after code is written. 24 ... This is why we talk about the time in terms of a function of n. In the ArrayMax example, ...
| PowerPoint PPT presentation | free to download
Query Assurance on Data Streams. Ke Yi (AT&T Labs, now at HKUST) Feifei Li (Boston U, now at Florida State) Marios Hadjieleftheriou (AT&T Labs) Divesh Srivastava (AT ...
| PowerPoint PPT presentation | free to download
Constructing a Rooted Balanced Tree for ( , r)-decomposable graph ... Use the separators as nodes of the rooted balanced tree and let S be their father. ...
| PowerPoint PPT presentation | free to download
Specimen Fabrication. Specimen Testing. Fine-Tune Rubber Substitution. Gradation Manipulation ... Specimen Fabrication. Specimen Fabrication. Gyratory ...
| PowerPoint PPT presentation | free to download
Book: Fortran 95-2003 for Scientists and Engineers, by S. J Chapman Transparencies prepared by Anthony T. Chronopoulos
| PowerPoint PPT presentation | free to download
Minimum Dominating Set Approximation in Graphs of Bounded Arboricity
| PowerPoint PPT presentation | free to view
Different materials, styles. Classical lecturing/demonstrations/lab work. Videos ... Introduction to two worksheets (with necessary DERIVE command explained) ...
| PowerPoint PPT presentation | free to download
Title: Carry Select Adders Author: Mitch Thornton Last modified by: Jim C. Harden Created Date: 8/16/2001 11:02:14 PM Document presentation format
| PowerPoint PPT presentation | free to download
Title: How Hard is it to Approximate the Best Nash Equilibrium? Last modified by: Adi Document presentation format: On-screen Show (4:3) Other titles
| PowerPoint PPT presentation | free to download
Title: A global spectrum of emerging pathogens Today s challenge Author: rebecca.goodwin Last modified by: qy Created Date: 5/3/2005 1:37:06 PM
| PowerPoint PPT presentation | free to download
Web S mantique RDF Olivier.Corby@sophia.inria.fr Semantic Web World Wide Web Consortium : www.w3.org Extension du Web actuel o l information serait munie d une ...
| PowerPoint PPT presentation | free to download
BIOPHYSIQUE BIOPHYSIQUE DES RAYONNEMENTS Radioactivit Rayonnements lectromagn tiques et particulaires, interactions Appareils de d tection, dosim trie
| PowerPoint PPT presentation | free to download
Dense Linear Algebra (Data Distributions) Sathish Vadhiyar Gaussian Elimination - Review Version 1 for each column i zero it out below the diagonal by adding ...
| PowerPoint PPT presentation | free to view
Due to the birthday principal: The probability that 2 Error will ... Backward compatibility. Even if you don't have the whole file you can mix functionals. ...
| PowerPoint PPT presentation | free to view
Constructive Algorithms for Discrepancy Minimization Nikhil Bansal (IBM) Discrepancy: What is it? Study of gaps in approximating the continuous by the discrete.
| PowerPoint PPT presentation | free to download
any edge e of T is in at most O(log h) of the subtrees ... ys=yt for each pair (s,t), and then find a subset of nodes to solve the SS-BB ...
| PowerPoint PPT presentation | free to download
Transaction Management and Concurre cy Overview R & G Chapter 16-17 There are three side effects of acid. Enhanced long term memory, decreased short term memory, and ...
| PowerPoint PPT presentation | free to download
Clock Synchronization in Practice? Radio Clock Signal: Clock signal from a reference source (atomic clock) is transmitted over a long wave radio signal
| PowerPoint PPT presentation | free to download
Feature space. query. What is it good for? Many things! Examples: Optical Character Recognition ... Given a query point q, let: p* point in P closest to q. r ...
| PowerPoint PPT presentation | free to download
Cyril Gavoille (Univ. Bordeaux) Christophe Paul (Univ. Montpellier) Milgram's Experiment ... Letter transmitted via a chain of individuals related on a personal basis ...
| PowerPoint PPT presentation | free to download
Approximation Algorithms for Non-Uniform Buy-at-Bulk Network Design Problems. Guy Kortsarz ... The algorithm iteratively finds a partial solution connecting ...
| PowerPoint PPT presentation | free to download
Manku et al. (2002) Symphony. arrange all participants in a ring I [0,1) ... Symphony: Distributed hashing in a small world. ...
| PowerPoint PPT presentation | free to download
Get the element whose key is Tiger Woods. Update the element whose key is Seri Pak ... 21. Hash Functions. Two parts. Convert key into an integer in case the ...
| PowerPoint PPT presentation | free to download
Workshop in R and GLMs: #4. Diane Srivastava. University of British Columbia ... So when p=0.5, solve log(1)=a bx. Coefficients: Estimate Std. Error z value Pr( |z ...
| PowerPoint PPT presentation | free to download
If pki,j be the minimum cost path among them, the cost being d(k)i,j ... Isoefficiency function. Parallel. Run time. Max Processes for E = O(1) Algorithm ...
| PowerPoint PPT presentation | free to download
Empirical Path Loss Model for Outdoor 802.11b Wireless Links Motivation 802.11b is a promising technology for Wireless Connectivity. It is designed for indoor use.
| PowerPoint PPT presentation | free to download
The image is read by a raster scan and the matching algorithm works with a ... raster scan of each of the areas where the areas are ordered by a raster scan as well. ...
| PowerPoint PPT presentation | free to download
Laboratory culture: pure culture. Contaminants = other microorganisms present ... deamidation of Gln and Asn - Thermal denaturation: reversible or irreversible. ...
| PowerPoint PPT presentation | free to view
What makes it hard? Chapter 7 in DS&AA Chapter 8 in DS&PS Insertion Sort Algorithm Conceptually, incremental add element to sorted array or list, starting with an ...
| PowerPoint PPT presentation | free to download
Event publishing (trader alerts and closed orders) Performance Metrics ... AUTO- REFRESH. Async. Writethrough. ODBC/JDBC. App. Client. Web-based GUI Administrator ...
| PowerPoint PPT presentation | free to view
Improved Compact Routing Tables for Planar Networks via Orderly Spanning Trees. Hsueh-I Lu (???) ... Compute an orderly spanning tree T for the input planar network G. ...
| PowerPoint PPT presentation | free to view
Hardening Linux for Enterprise Applications. Peter Knaggs & Xiaoping Li ... Hardening Linux - Using NIC Failover for HA. Understanding network bonding driver ...
| PowerPoint PPT presentation | free to download
Kinetic data structures. Goal. Maintain a configuration of moving objects ... What is known about parametric and kinetic heaps? Overmars and Van Leeuwen (1981) ...
| PowerPoint PPT presentation | free to download
If both sodium acetate and acetic acid are dissolved in the same solution they both dissociate and ionize to produce acetate ions.
| PowerPoint PPT presentation | free to download
Extension du Web actuel o l'information serait munie d'une ... Associer s mantique (sens) aux documents. http://www.scientificamerican.com/2001/0501issue ...
| PowerPoint PPT presentation | free to download